Administrator Dashboard Manual¶
Introduction¶
Excalibur Dashboard is part of the Excalibur Enterprise system, which serves to manage activities in the Excalibur environment. Excalibur Dashboard contains several objects which affect the User's competences in Excalibur environment or allow User / User group execute a specific action.
Roles:
| Role | Description |
|---|---|
| Superadministrator | First person registered in Excalibur Dashboard. |
| Administrator | Role who can manage all Excalibur system. |
| Auditor | Role to preview / control of managing of Excalibur. |
| ServiceDesk | Role who has access to specific parts of Excalibur Dashboard for User support. |
| Manager | Assigned role based on AD setup. |
| User | Every registered user has an automatically User or Manager role. It is dependent on AD setup. |
For more information read: Excalibur Enterprise Roles Description
Groups:
Excalibur works with User Groups for which it is possible to assign other groups, roles and policies.
| Group | Description |
|---|---|
| Users Group | Section where is possible to create UserGrups and assign Users, policies and ComputersGroups. By default, Default User Grup contains all users registered in Excalibur. Default policy is applied on Default User Group. |
| Computers Group | Section where is possible to create Computers Groups and assign Computers and PAM resources. By default, Default Computers Group contains all Computers registered in Excalibur. |
| Geofences Group | Section where is possible to create Geofence Group and assign a geofences created in Geofences part. |
Security policies:
Every user is in the Default UserGroup which has a Default policy presetted by the Excalibur system. To assign a new policy is necessary:
-
Create UserGroup and assign a required users
-
Create a new policy with rules and assign it to required UserGrup (in case that rules contain restriction for location, then define geofences in Geofences section)
For more information read: Excalibur Security Policies Management
Geofences:
Excalibur allows you to define Location /Geofence/ from where a user can execute a specific action. To set a required location/geofence is necessary to set rules for Set Geofence policy. Default policy has disabled rules to set location.
For more information read: Excalibur Security Policies Management
| Type of geofence | Description |
|---|---|
| Home | Every user can have 2 locations. Home location is possible to set in the User's detail or via its token. |
| Temporary | Temporary location can be used for business meetings etc. Temporary location is possible to set in user's detail. Validity of temporary location ends on 23:59:59 server time. |
| Geofence | Global location setup in Geofence section |
Logging in¶
To log into the Excalibur Dashboard, please use your initialized Excalibur mobile app. You will be logged in automatically after all authentication factors are successfully verified.
In spite of the fact that User might have a multiple User roles, everyone who is logged into the Dashboard, is logged under the User role by default. Regular User only sees own Actions and Sessions. A deployed Excalibur always has at least one User with the Administrator role assigned.
In Dashboard User Interface (UI) in the top left corner, there is a drop-down menu to choose among different User Roles assigned to the User. Each Role implies its own range of capabilities available in the Dashboard.
This manual is focused on capabilities available to the Administrator role only.
Sections¶
Dashboard functionality is organized into logical sections to make navigation easier.
Overview¶
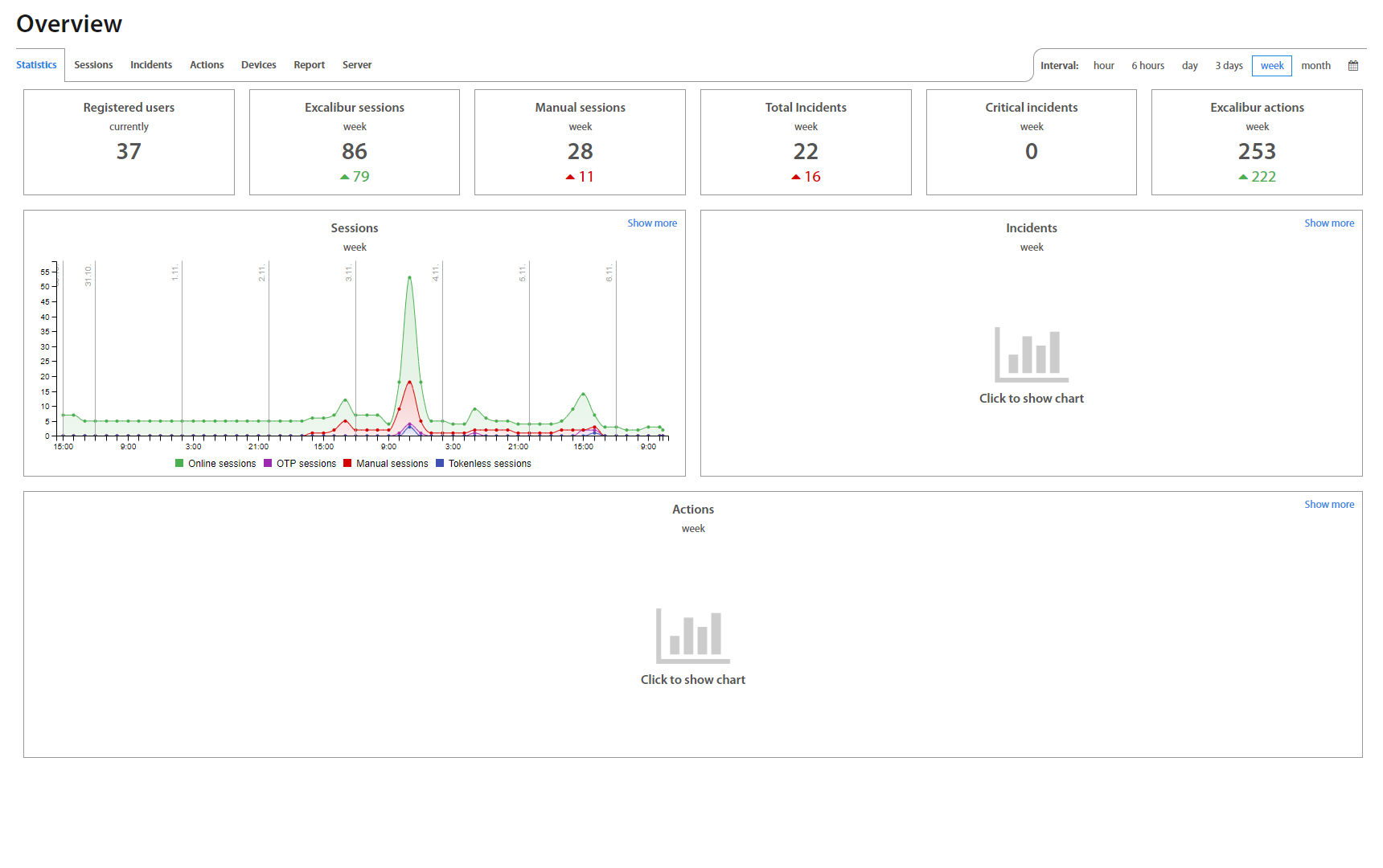
- Overview - Summary of all activities and their statistics, Devices as wel as Usage report and Server setup.
- Users - List of all Active Directory users with Excalibur app installed and registered into Excalibur.
- Timeline - Summary view of users activity during a given day.
- Actions - List of all actions took by every user.
- Sessions - List of all logged, active, and manual sessions, as well as their history.
- Computers - List of all computers with their names, Excalibur version, OS and current status information.
- Components - List of all currently deployed Excalibur components and their versions.
- PAM - List of all PAM resources, which are available for users
- SAML - Service Providers - Page where SAML is uploaded
Groups¶
- Users - List of all groups of users created in Excalibur.
- Computers - List of all computers groups created in Excalibur.
- Geofences - List of all groups of geofences created in Excalibur.
Security¶
- Roles - List of all roles from the company's Active Directory.
- Security policies - Page to view, edit, add or remove individual policies.
- Incidents - Lists of all registered incidents in Excalibur.
- Verifications - List of all verifications that happened or are currently happening in Excalibur.
- Geofences - Page which serves to manage existing and create new geofences in Excalibur.
- Audit - List of all changes in Excalibur dashboard divided into tabs.
- Logger - List of all actions provided by user's tokens.
- Notifications - Page to set email notification.
Status¶
- Configurations - Page to set email notification.
- Versions - List of all Operating System (OS) versions, Statuses andExcalibur versions (version of a respective component) of every device in Excalibur ecosystem, as well as a summary of all versions currently used.
- API access tokens - Page from where the static tokens can be configured.
- Syslog - Lists of all errors that happened in Excalibur under every component.
There is a countdown timer, located at the bottom, next to the Login button. User is logged out after 15 minutes of inactivity.
General¶
Overview¶
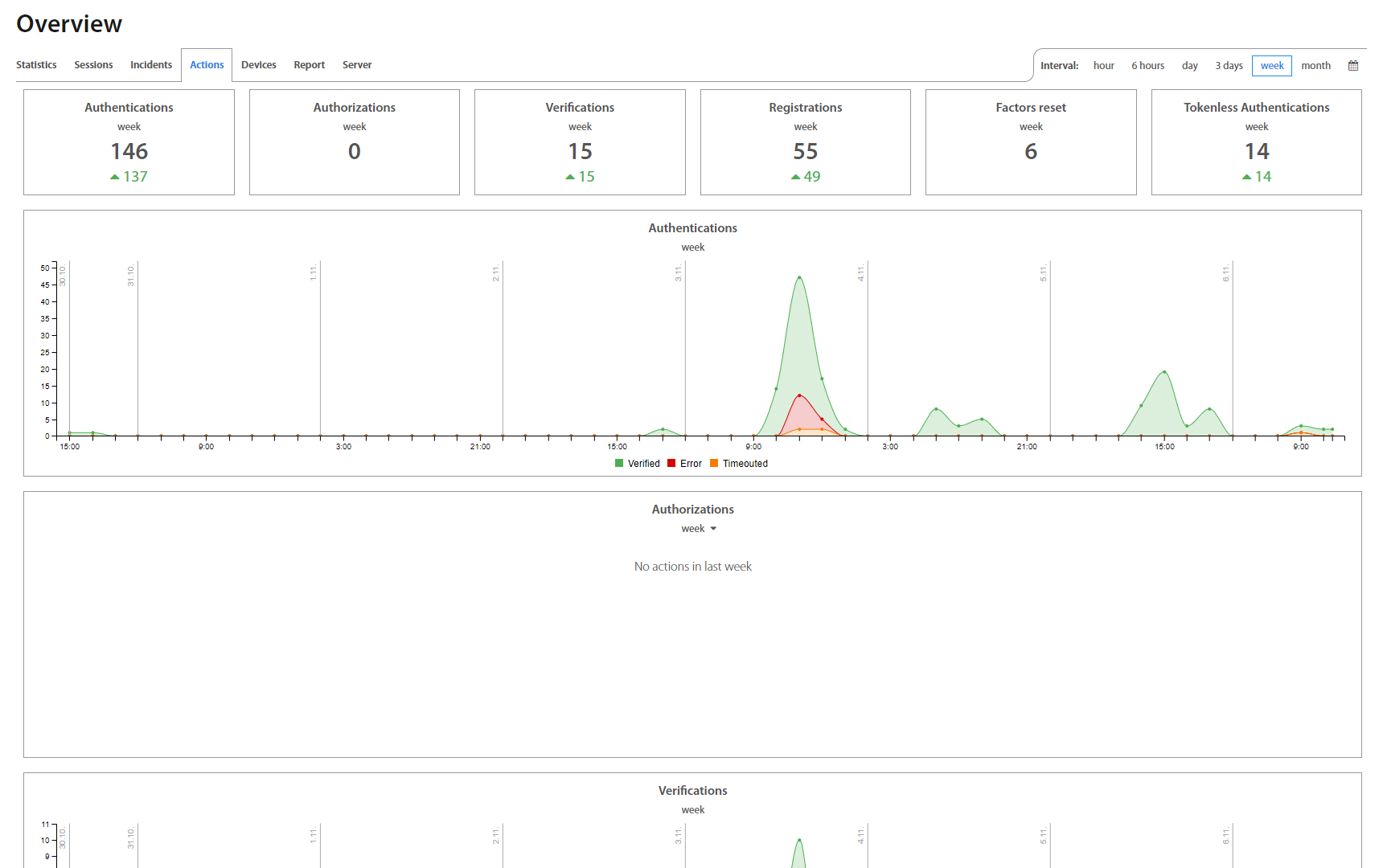
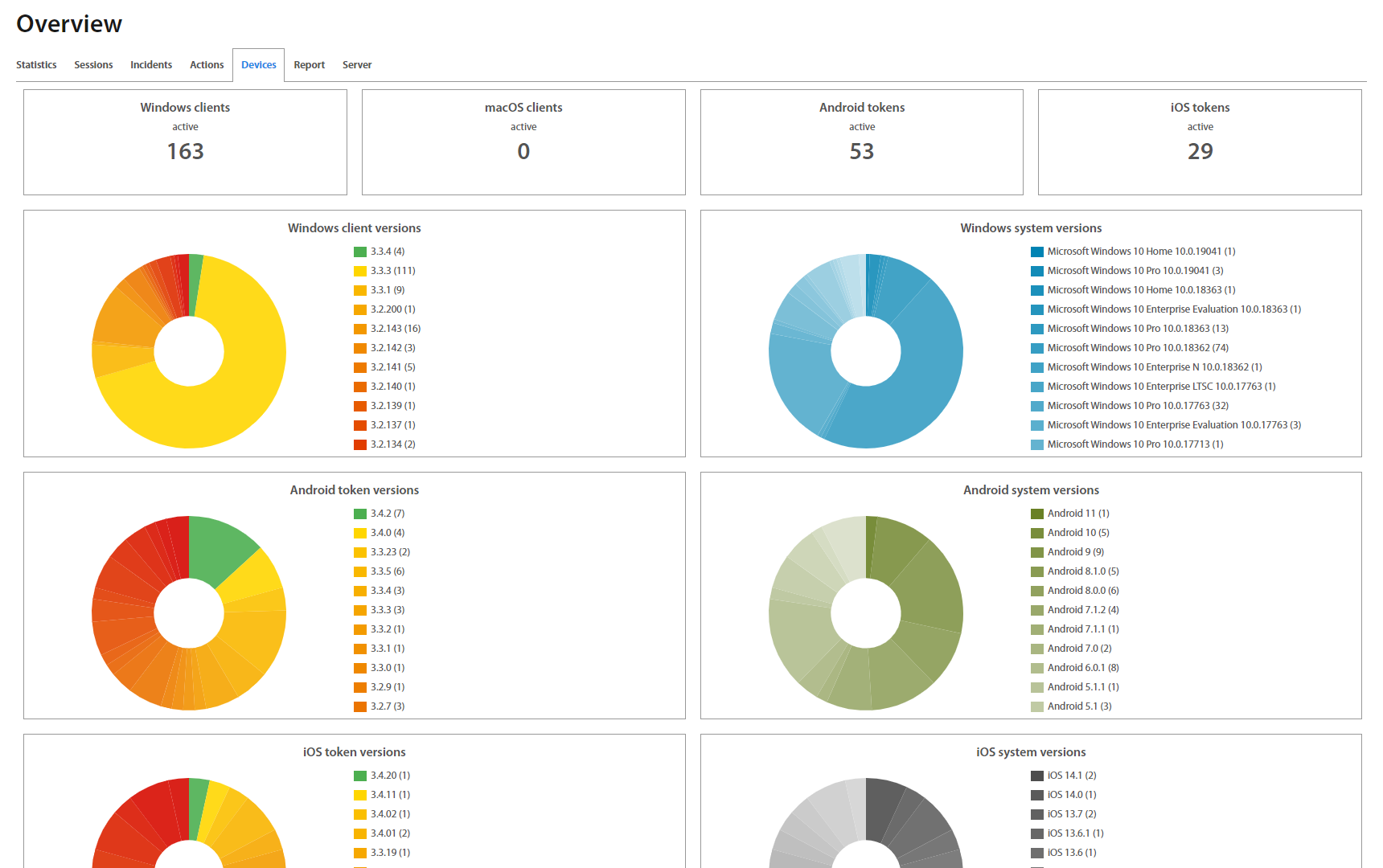
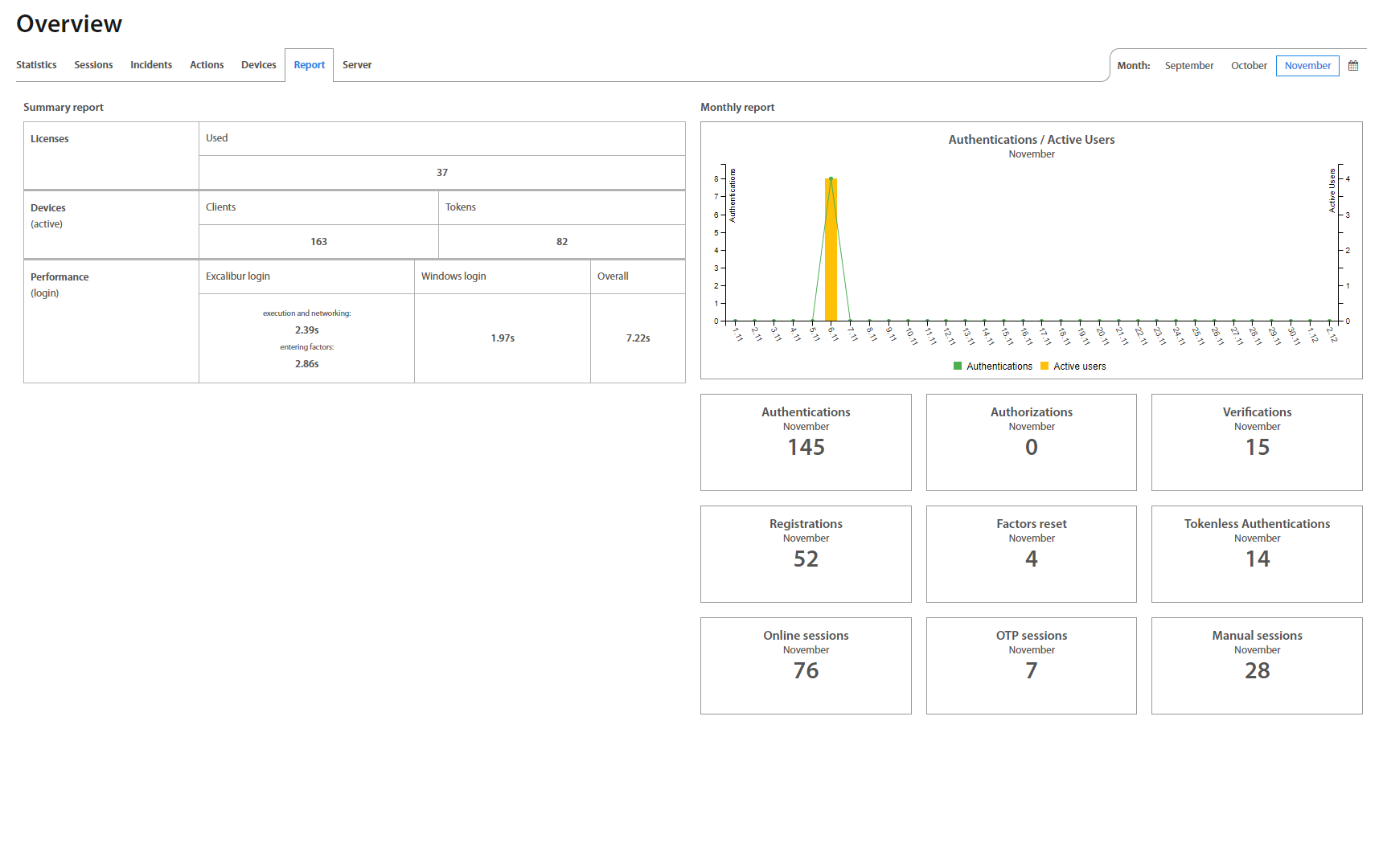
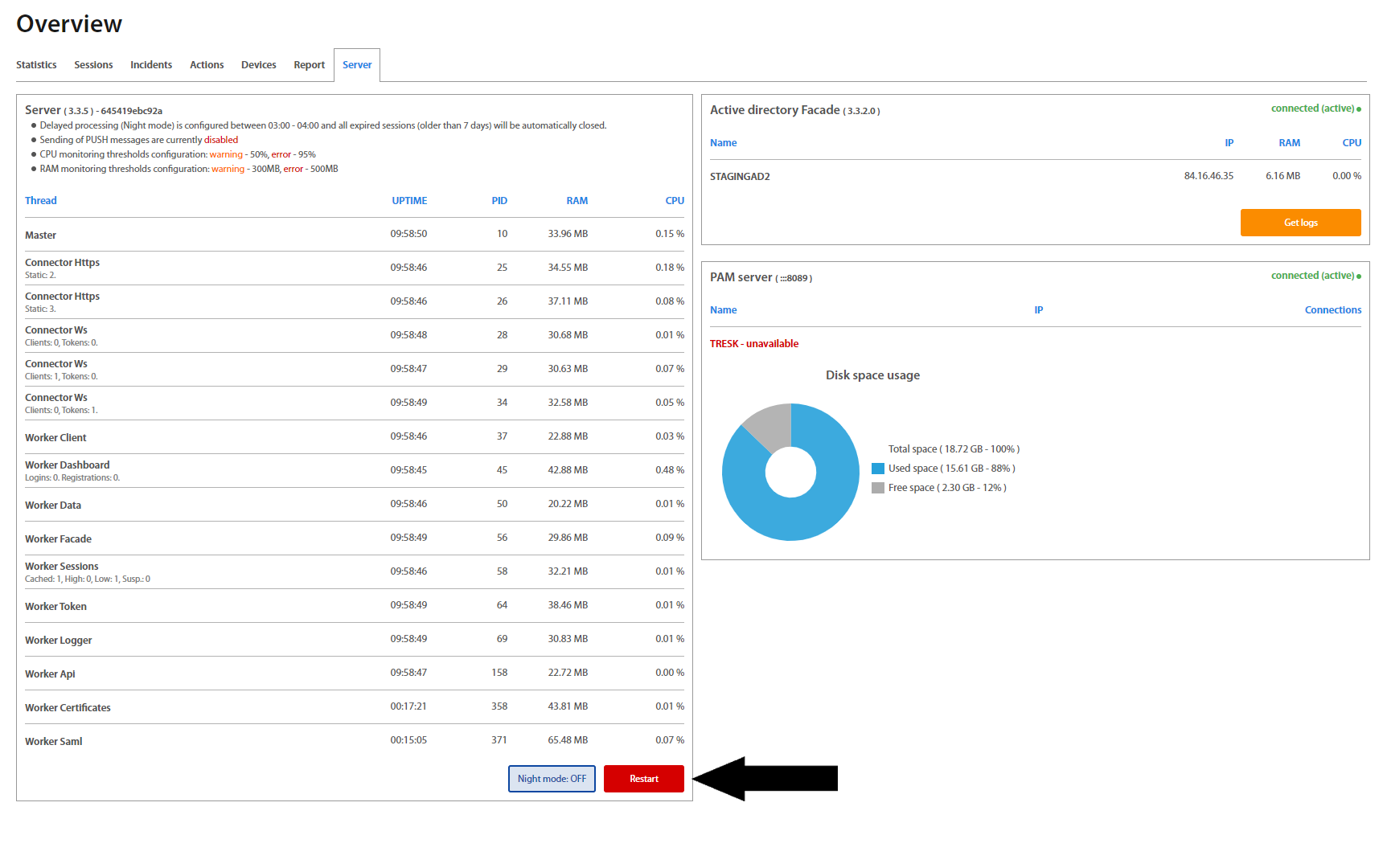
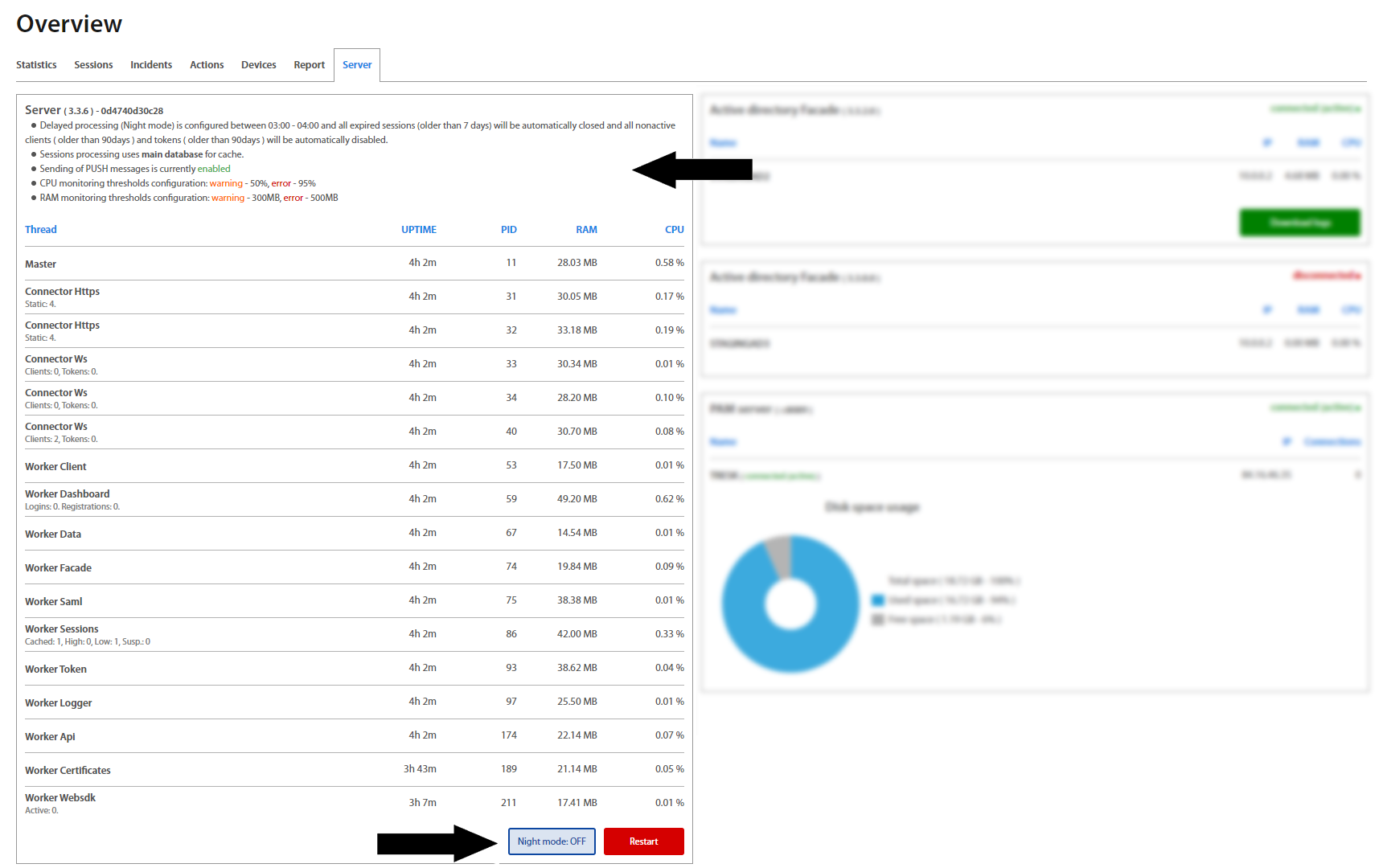
After the successful login, an Administrator is redirected on the Overview page. Overview includes Users activity statistics (Statistics, Sessions, Incidents, Actions, Devices) and an overview of the Server and Active Directory Facade statuses - their connection state, version, as well as RAM and CPU usage, etc. Administrator may set desired timeinterval based on his / hers needs. To show charts click on the button.
To restart the Server, please click on the “Restart” button.
Server tab providess to process a delayed sessions /manual sessions/. By default, these sessions are processed in the nigth time interval /Night mode button is Off/. If is needed to process delayed sessions in another time, set the Night mode button to On. Inactive sessions or sessions which last more than 7 days are automatically closed. Computers which were not logged more than 90 days are automatically disabled.
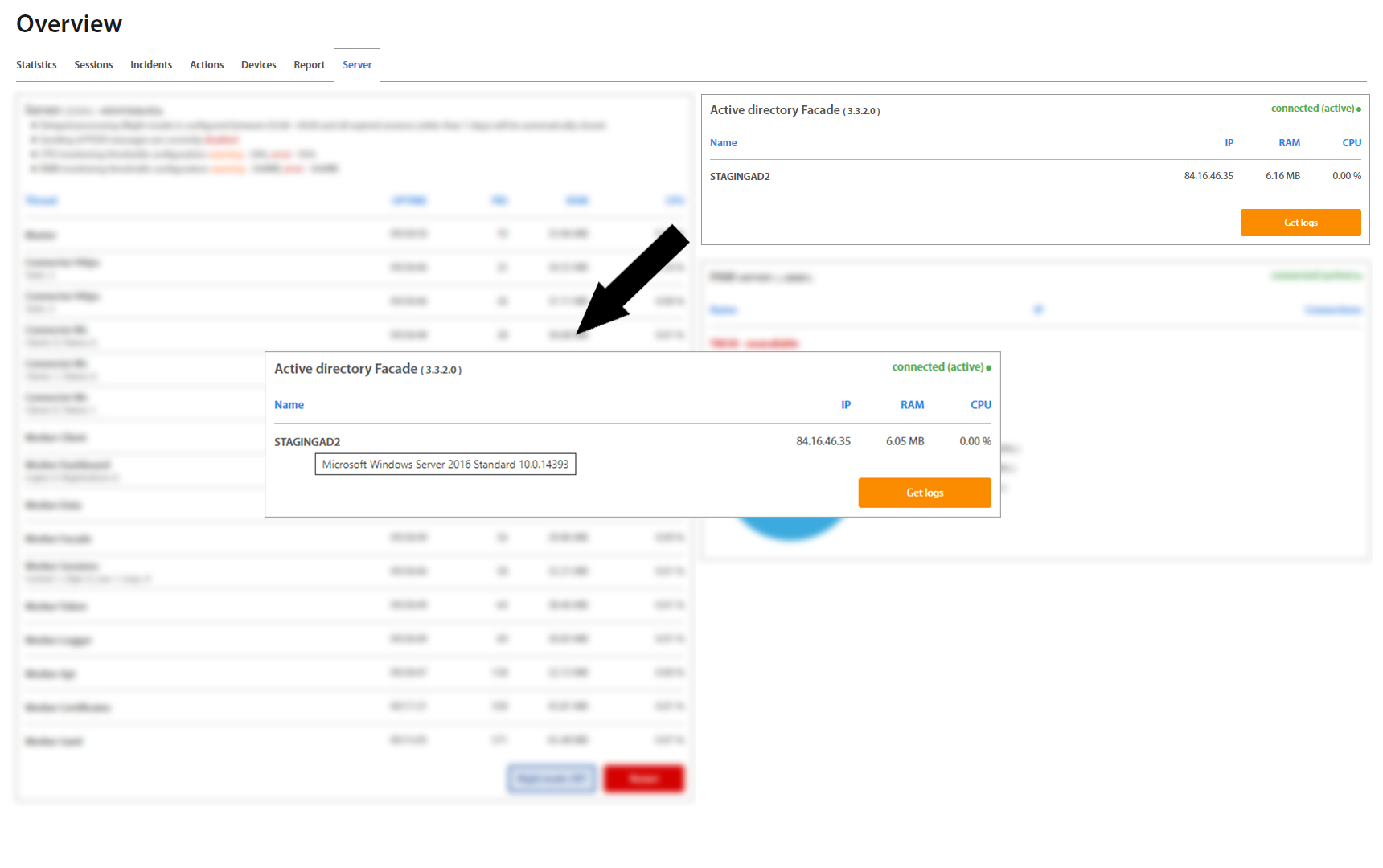
Facades which are installed on the server are shown on the right side. There is information about the version of Facade, name of server and IP address where facade is installed, usage of RAM and CPU. Green colored status means that Facade is connected, active and works properly. Orange colored status means that Facade is connected, but passive and waits. Red colored status means that Facade is disconnected and is necessary to launch it. If the active facade is disconnected, the passive facade is switched to active status and works. By hovering with the mouse over the server’s name, the version of server shows up.
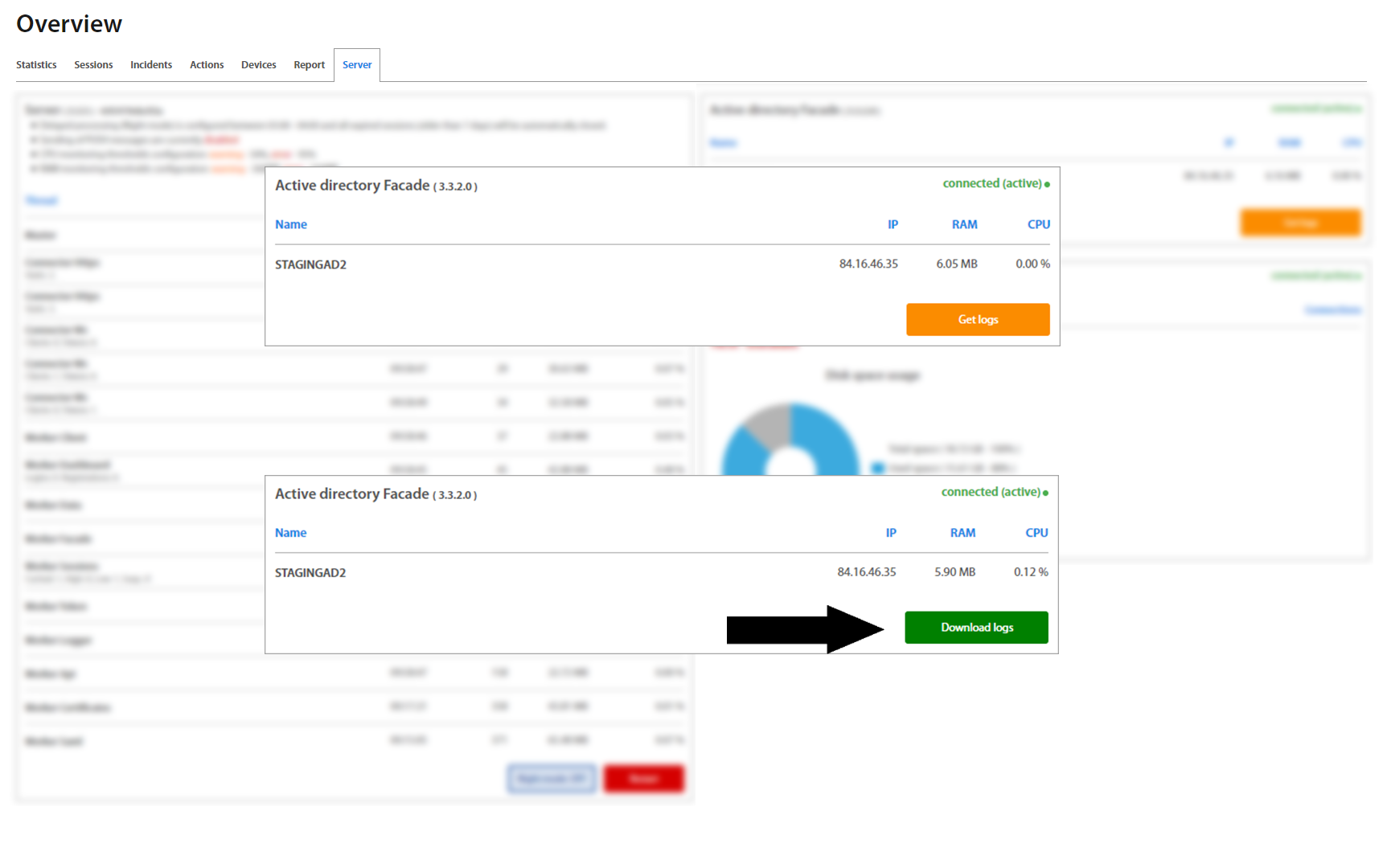
To download Facade logs, click on the “Get logs” button of required Facade. Logs will be fetched and then click on the “Download logs” button. Logs are downloaded immediately.
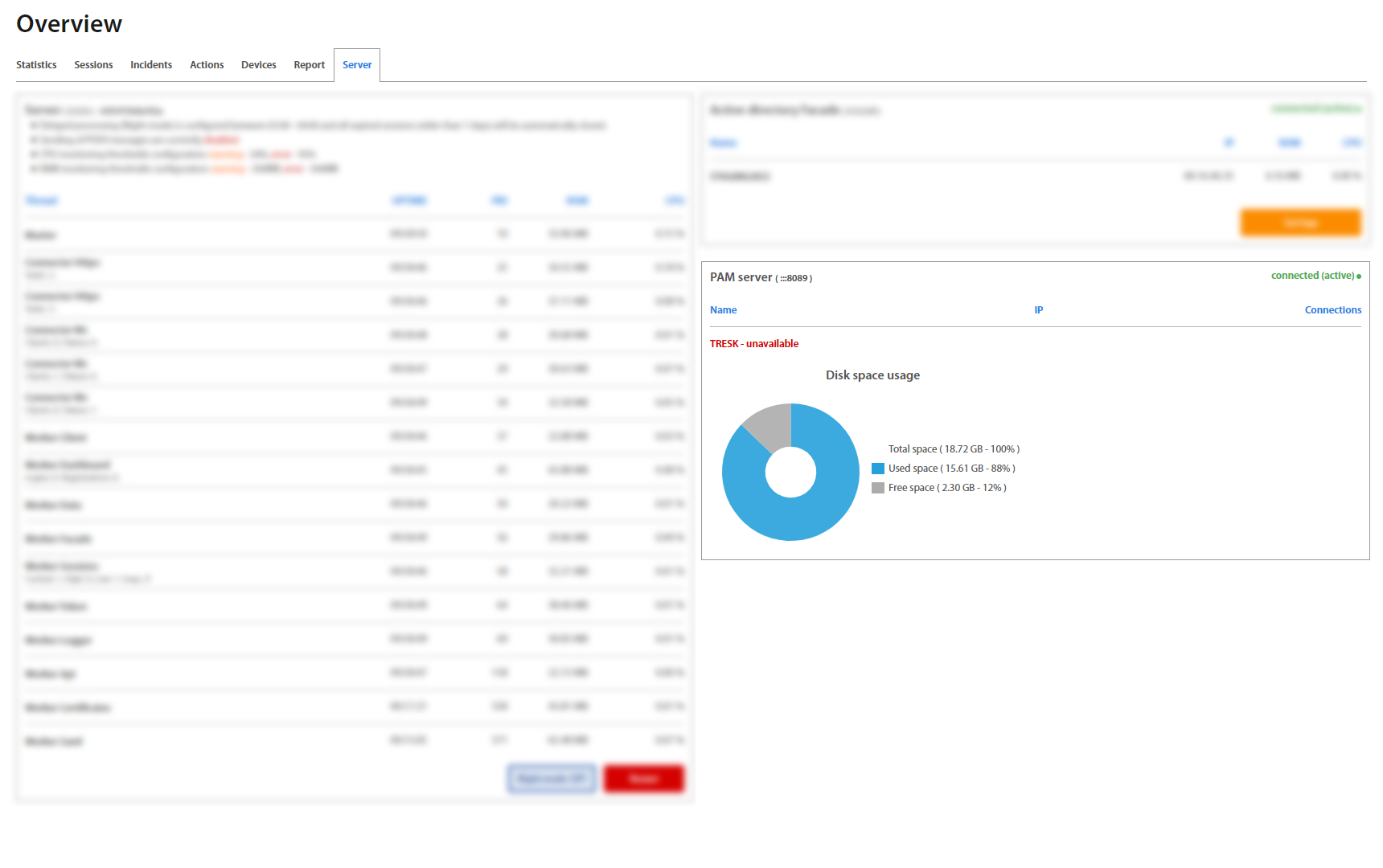
If Excalibur contains the PAM, the server tab shows the status of PAM server, TRESK connection, and diskspace available for recording.
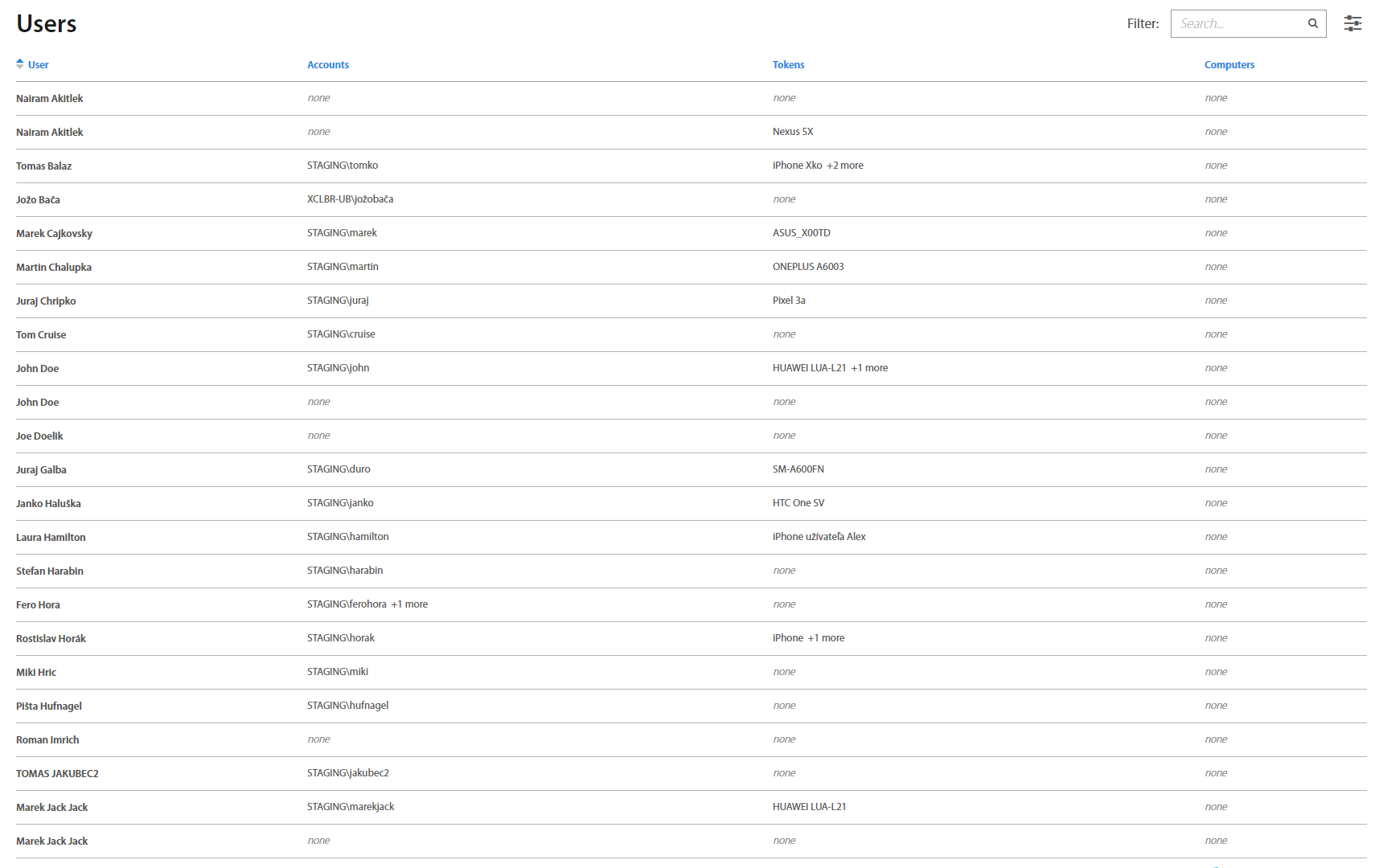
Users¶
All Active Directory Users who are registered into Excalibur can be found on the Users page. Filtering by groups, accounts, tokens and computers as well as search by name are available in the top right corner.
User: Account Detail, Sessions¶
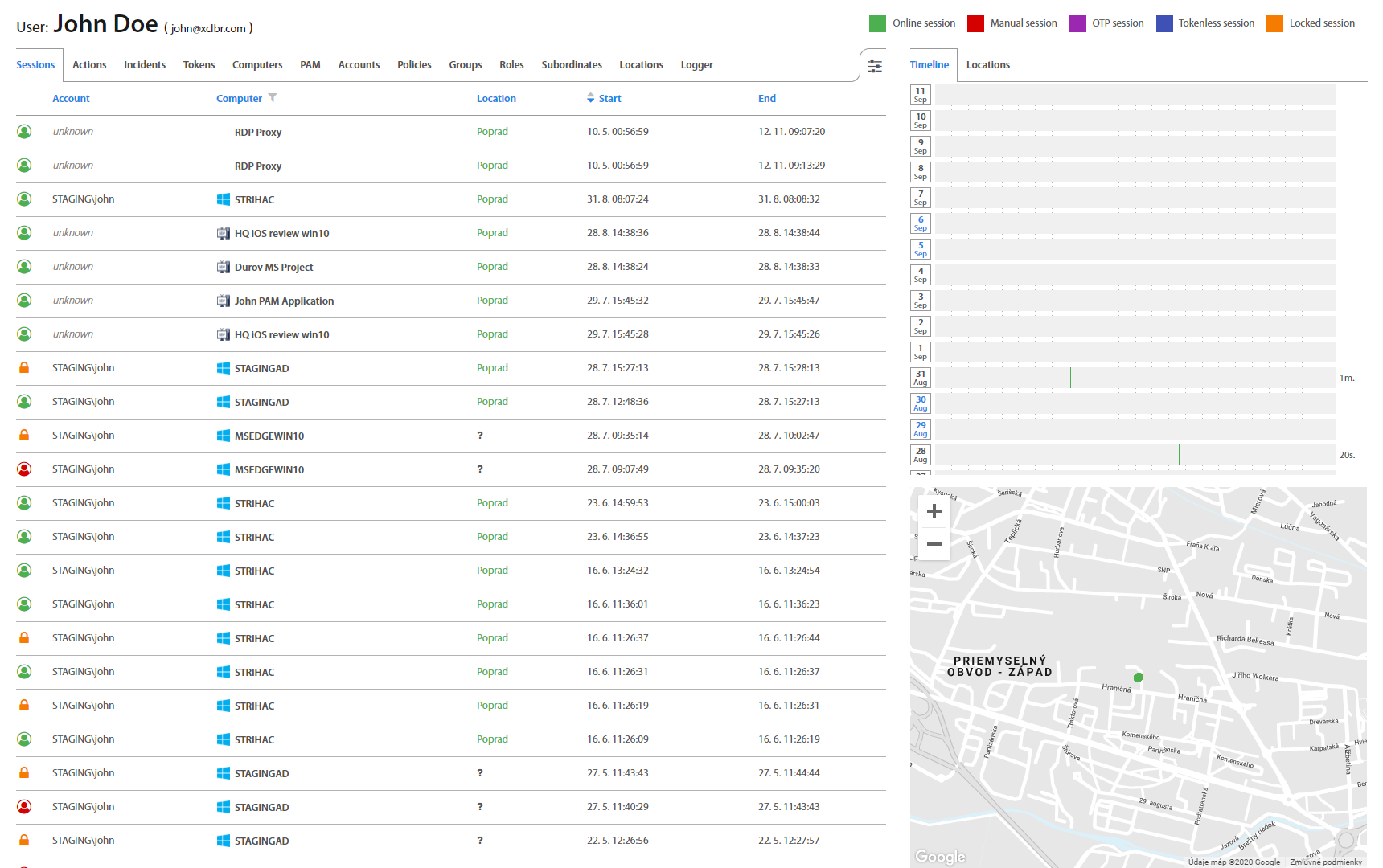
Click on the username of selected User in the list of Users and User’s account details page (User page) shows up. User page contains User’s Sessions, Actions, Incidents, Tokens, Computers, Accounts, Policies, Groups, Roles, Subordinates and Locations organized in tabs. In the Sessions tab, all User’s sessions with start and end times are recorded. If the User is still logged, an Administrator can lock or end User’s session - logout the User.
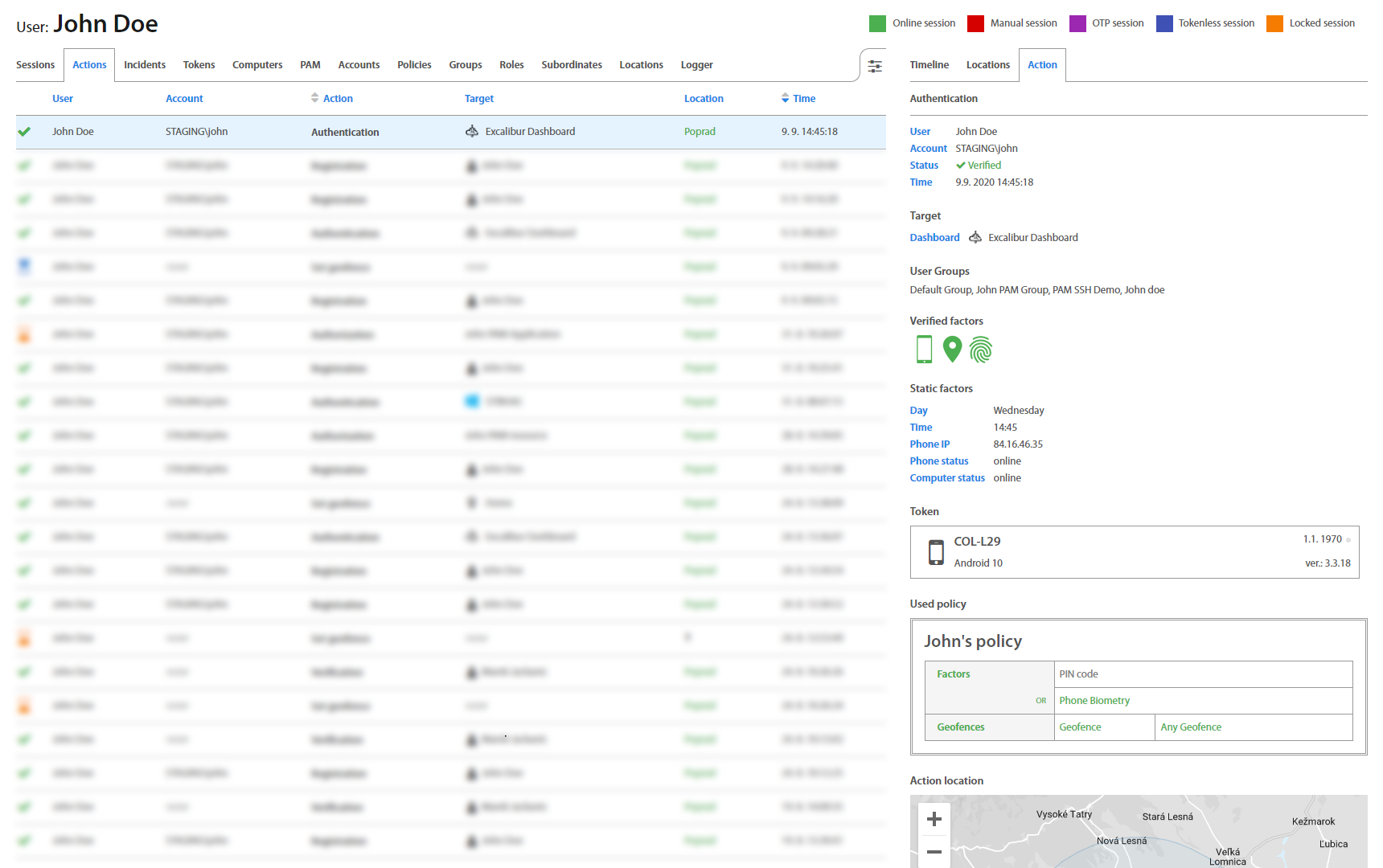
User: Actions¶
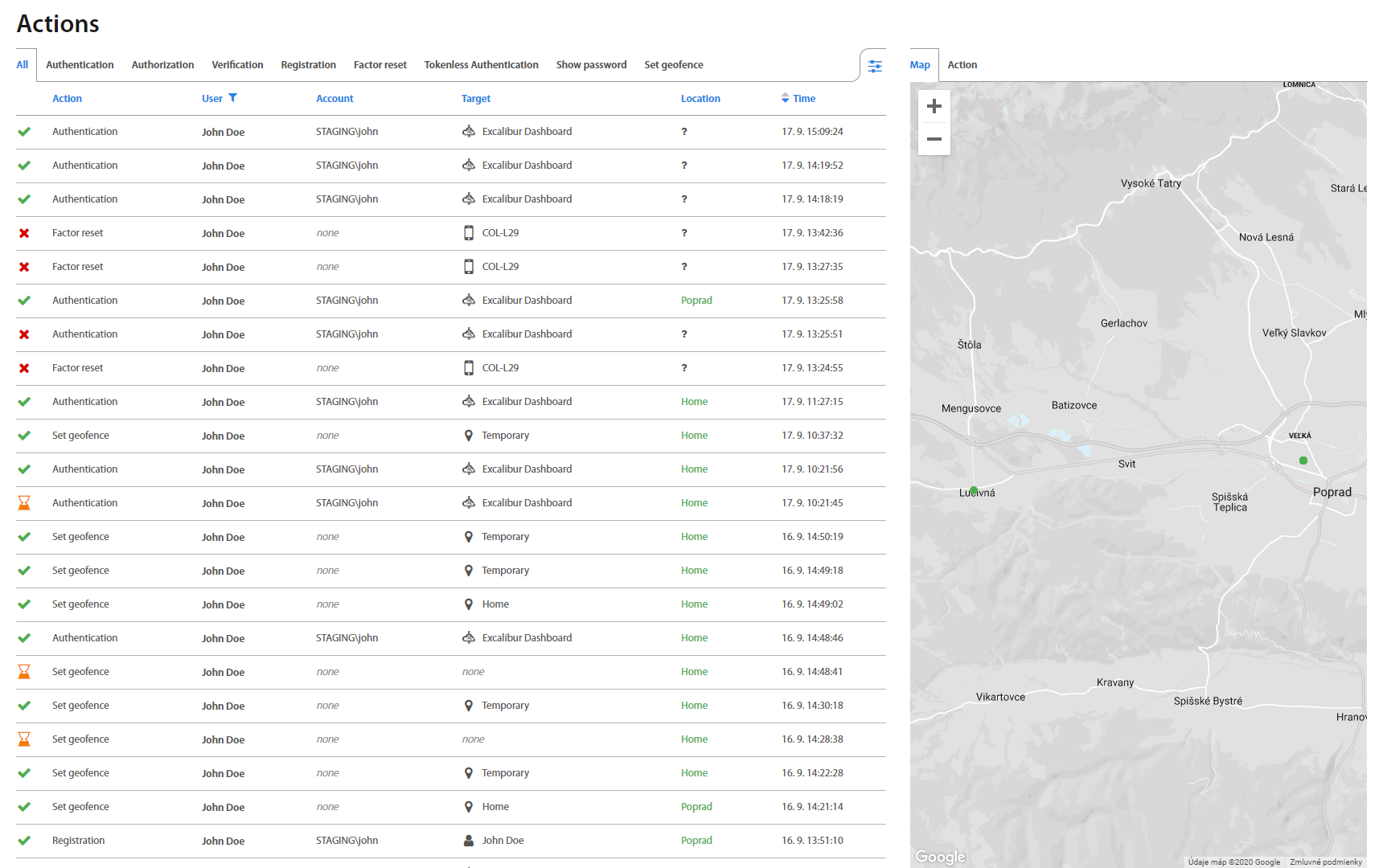
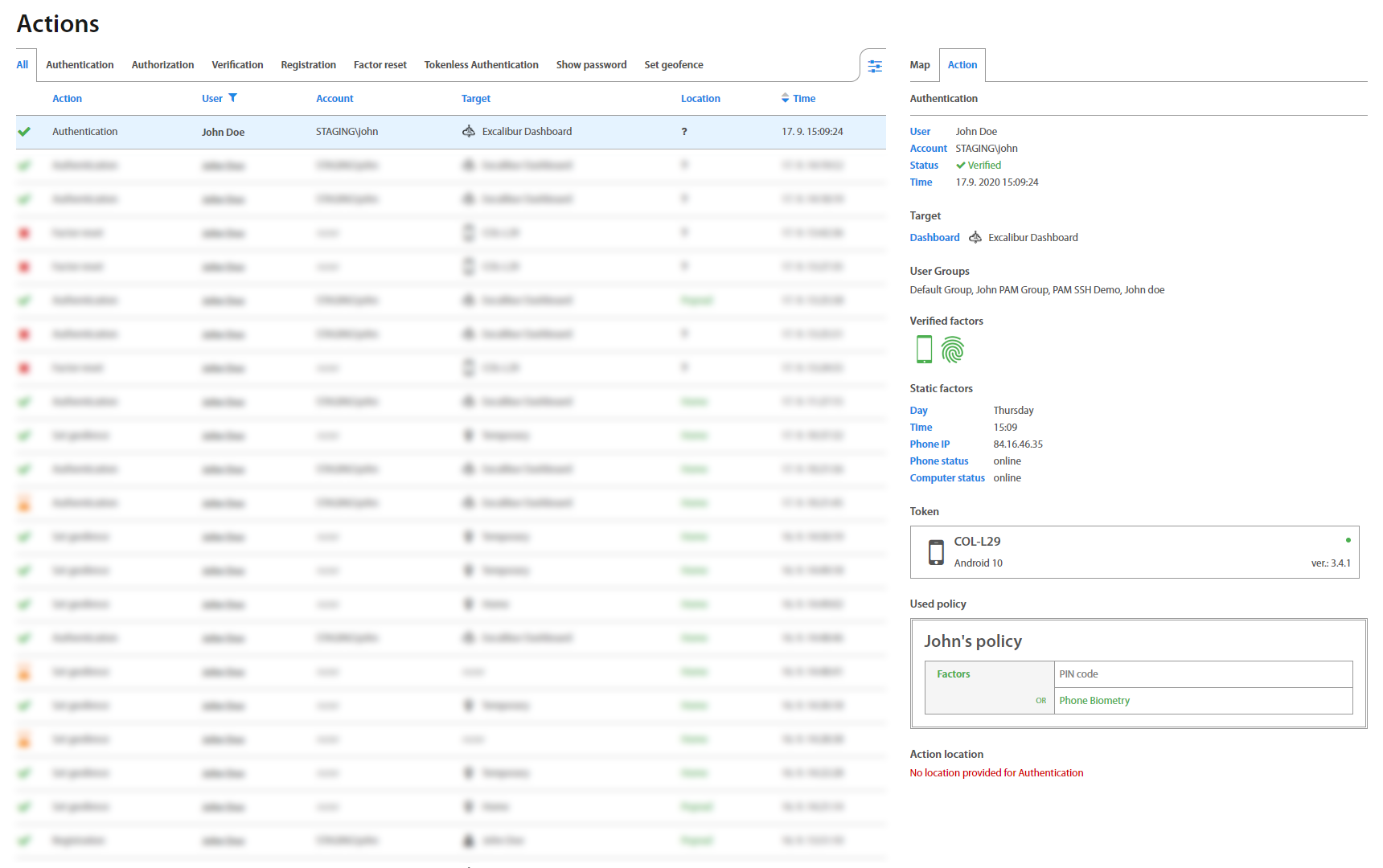
Actions tab displays all actions which the User executed or currently executes, such as: Authentication, Authorization, Verification, Registration and Factor reset, together with an action’s status. Clicking on an individual Action, detailed information shows up. Green colored status means that action has been done successfully. Red means that action failed because one of the required factors of policy was not verified. In the policy table are marked factors which were verified or not.
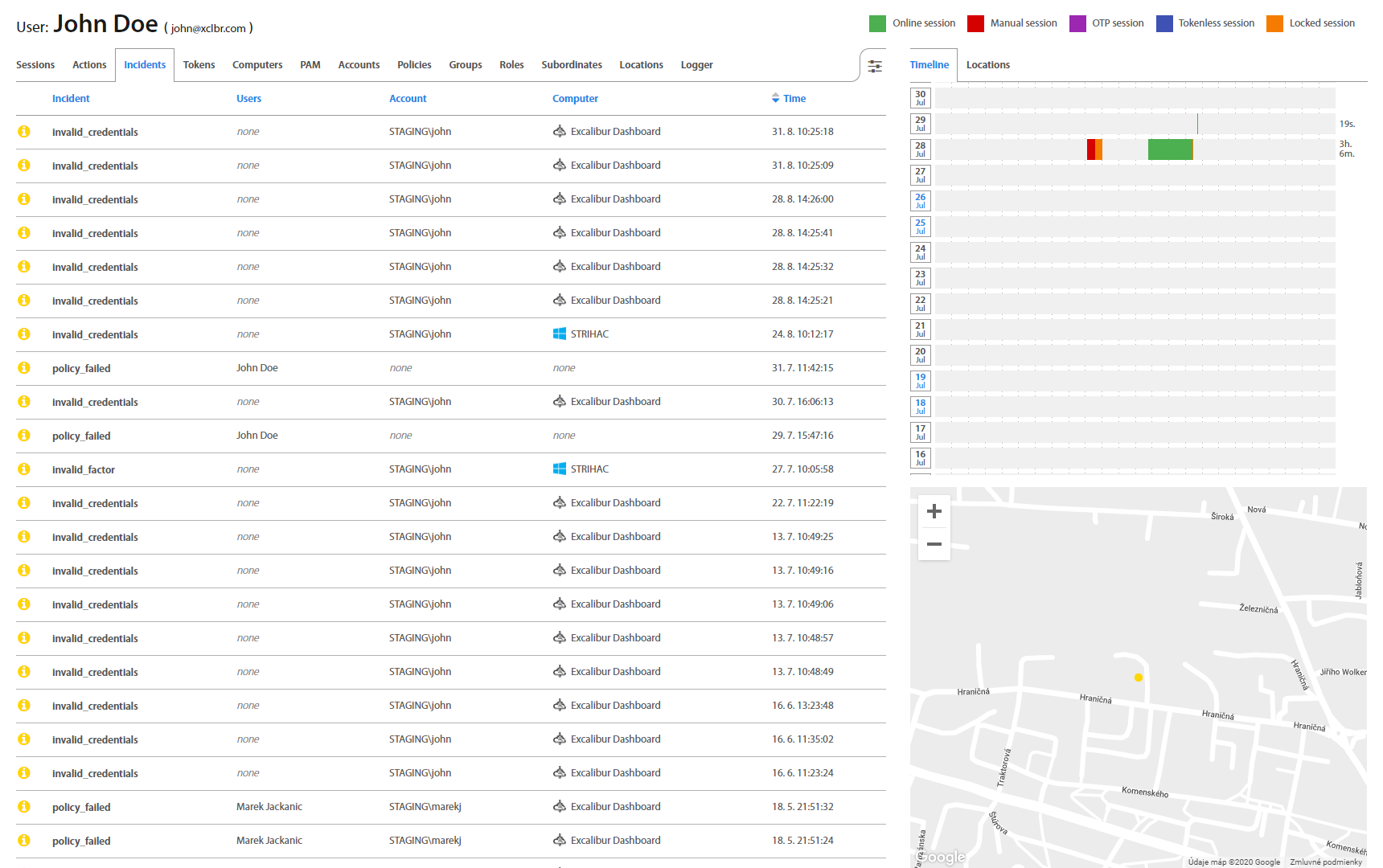
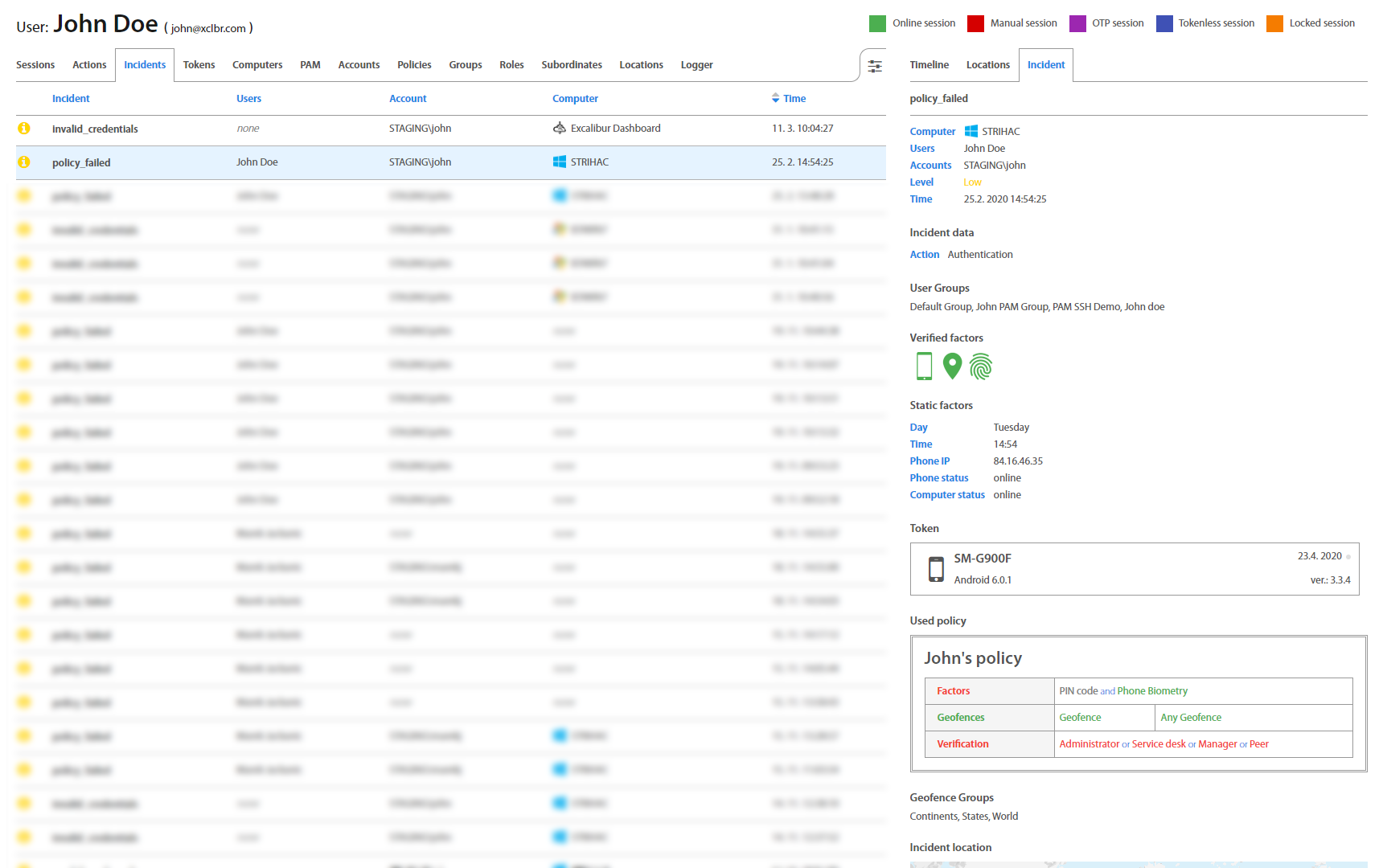
User: Incidents¶
Incidents tab provides a list of all User’s Security Incidents (like Invalid credentials) for a review. Clicking on an individual Incident detailed information shows up.
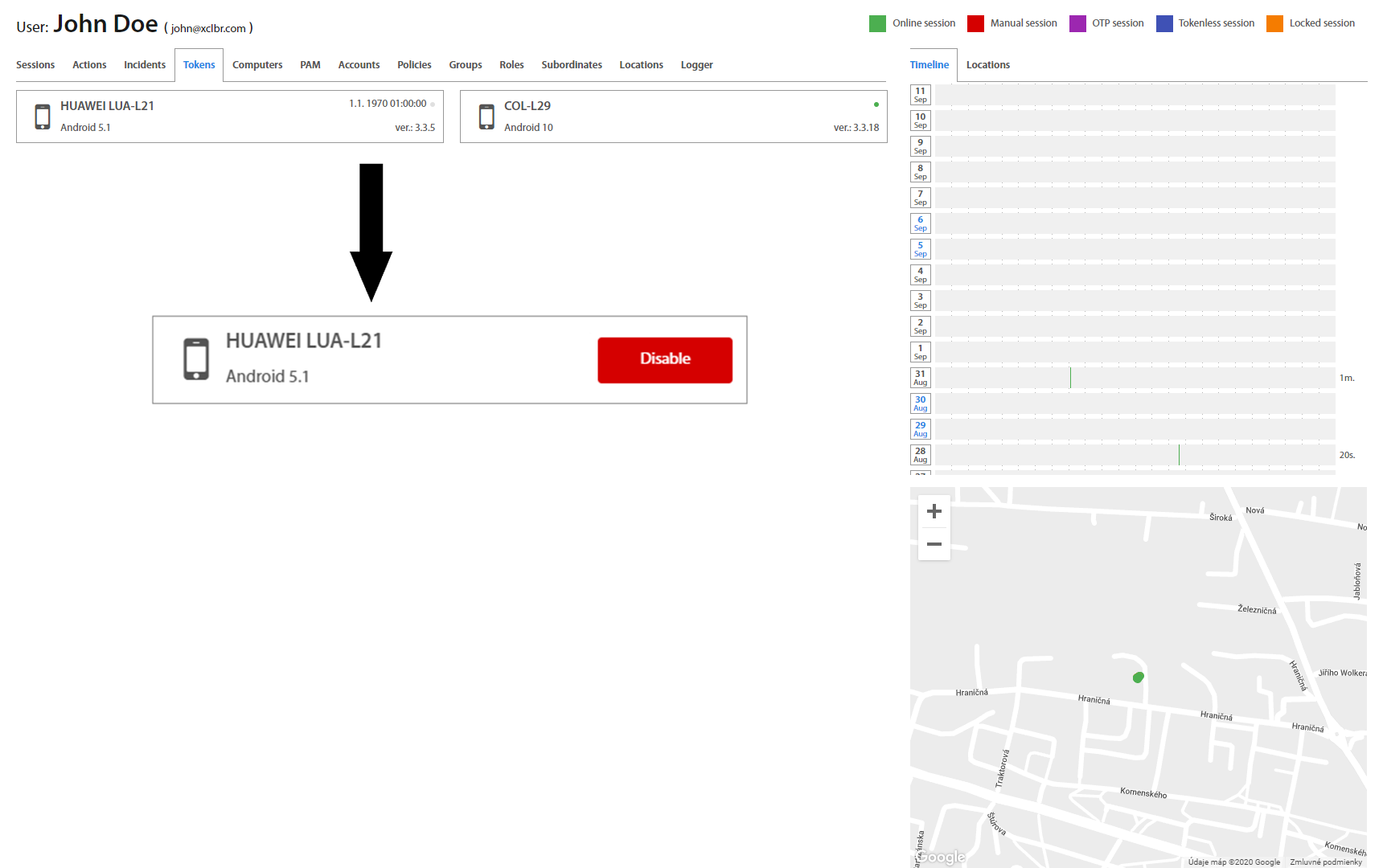
User: Tokens¶
Tokens tab shows all registered tokens which the User has. A color dot next to the device name represents the token's online / offline state, and below it a mobile app version could be found. By hovering the mouse over the token “Disable” option will show up. After disabling the token, User will not be able to use the selected token.
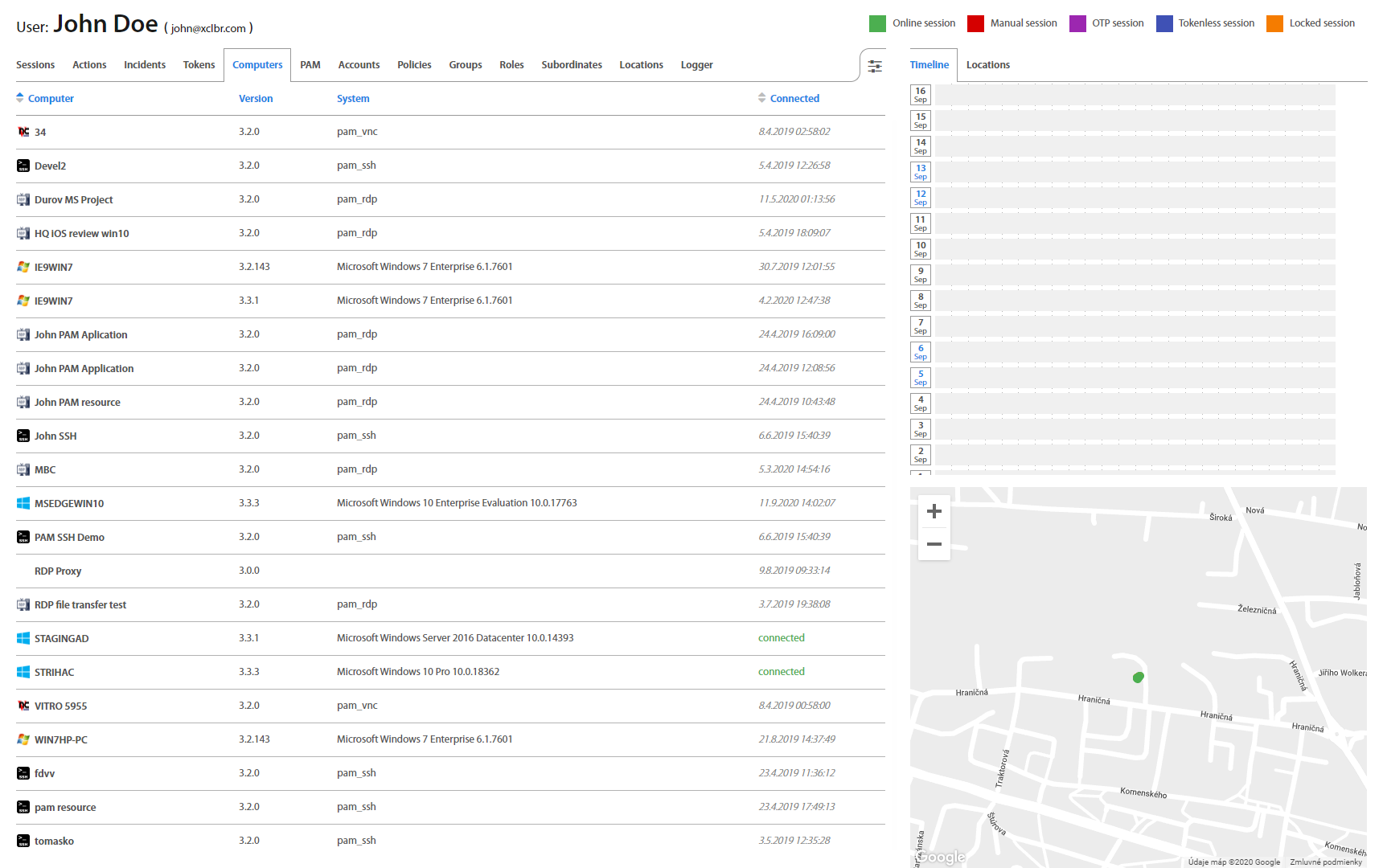
User: Computers¶
Computers tab contains all computers and PAM resources where the User was or is logged in. If the User is currently connected, status connected is indicated in green. If the User is already logged out, the last time of logout is shown in grey. By clicking on the computer name, the Computer detail page shows up.
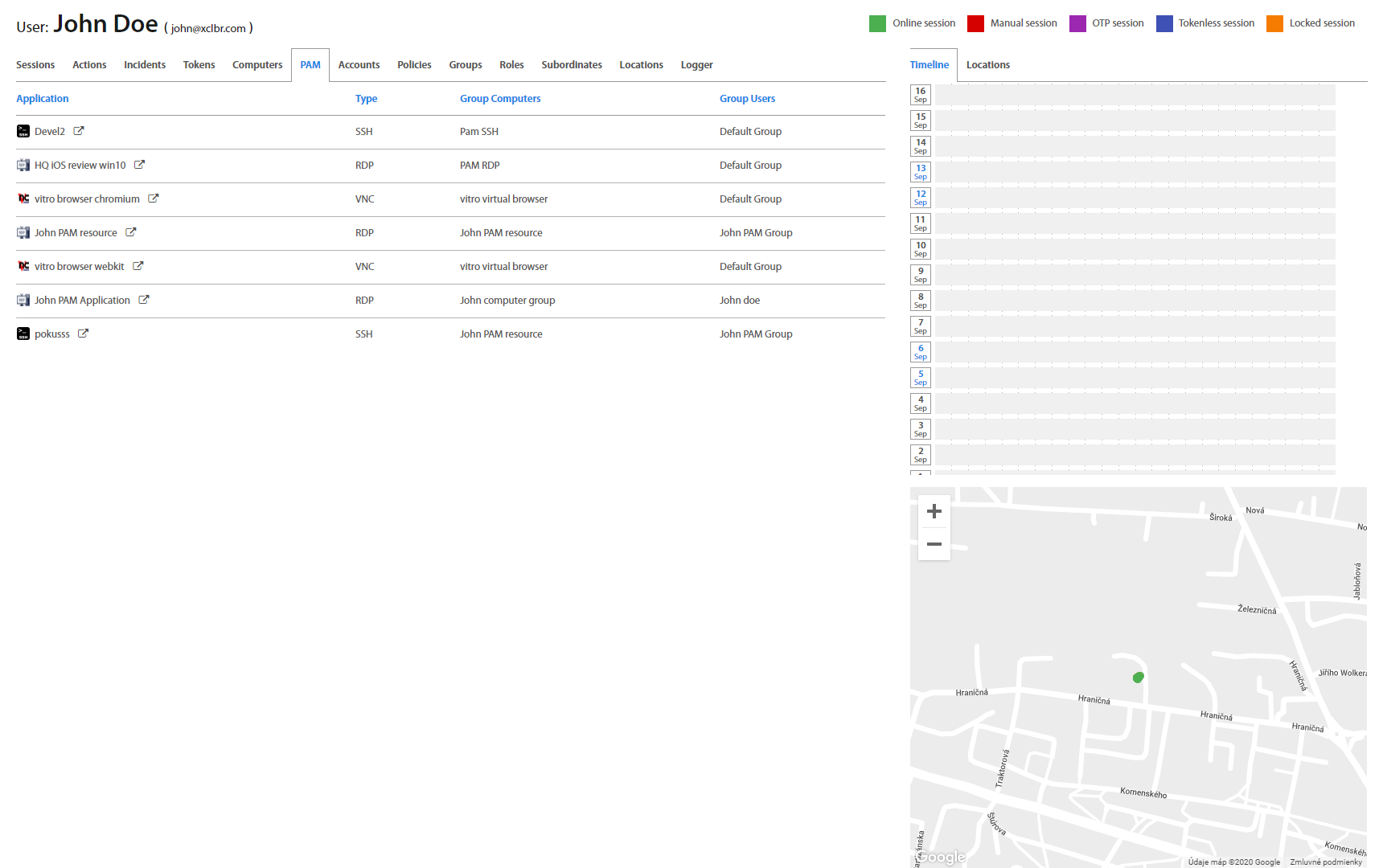
User: PAM¶
PAM tab contains all PAM resources which are assigned to the user and describes the type of PAM, group where is PAM resource assigned and user groups where is PAM resource assigned. By clicking on an icon or name of a PAM resource, PAM resource details show up. By clicking on button, PAM resource opens.
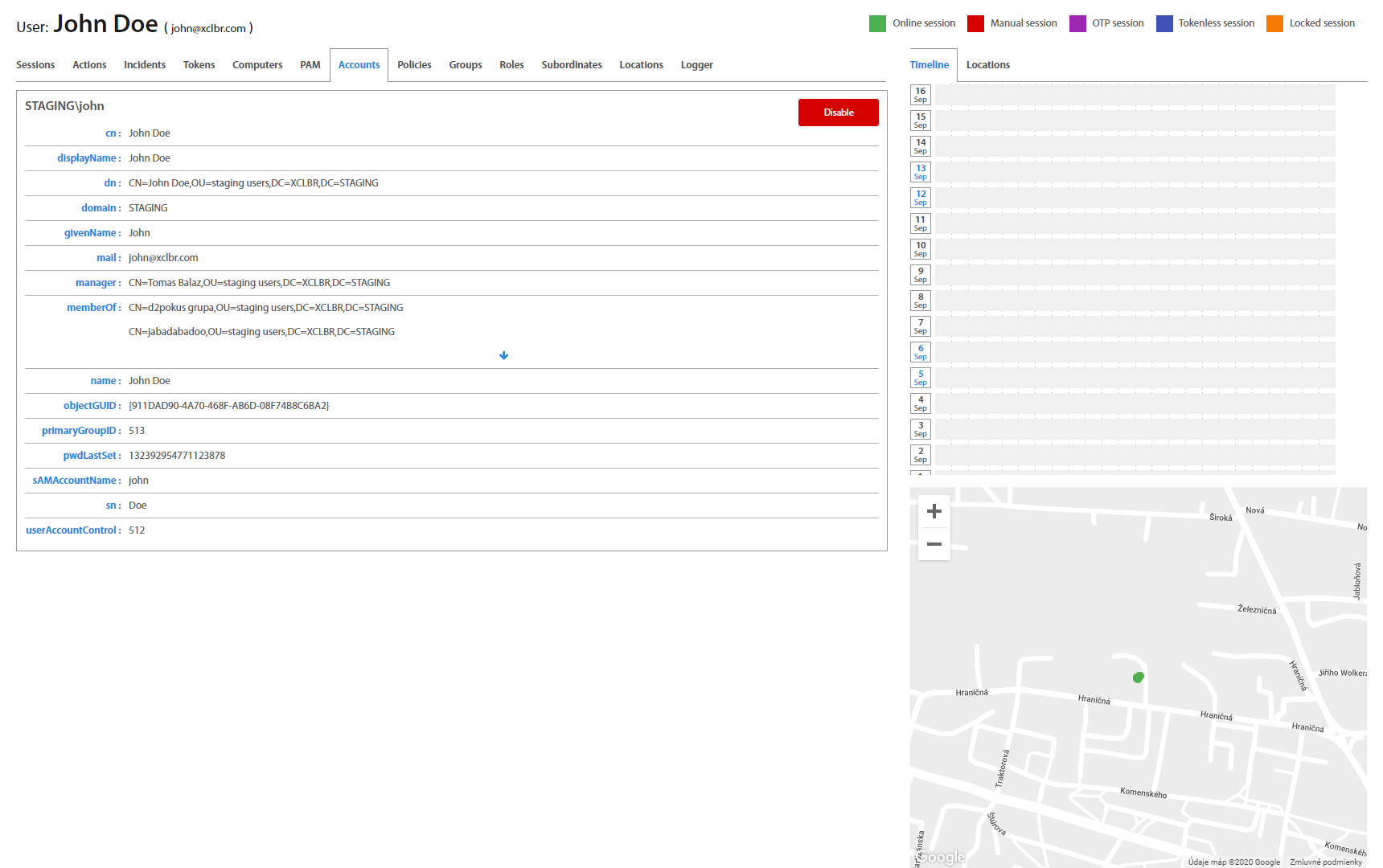
User: Accounts¶
Accounts tab represents User’s Active Directory / LDAP account details as Excalibur sees them.
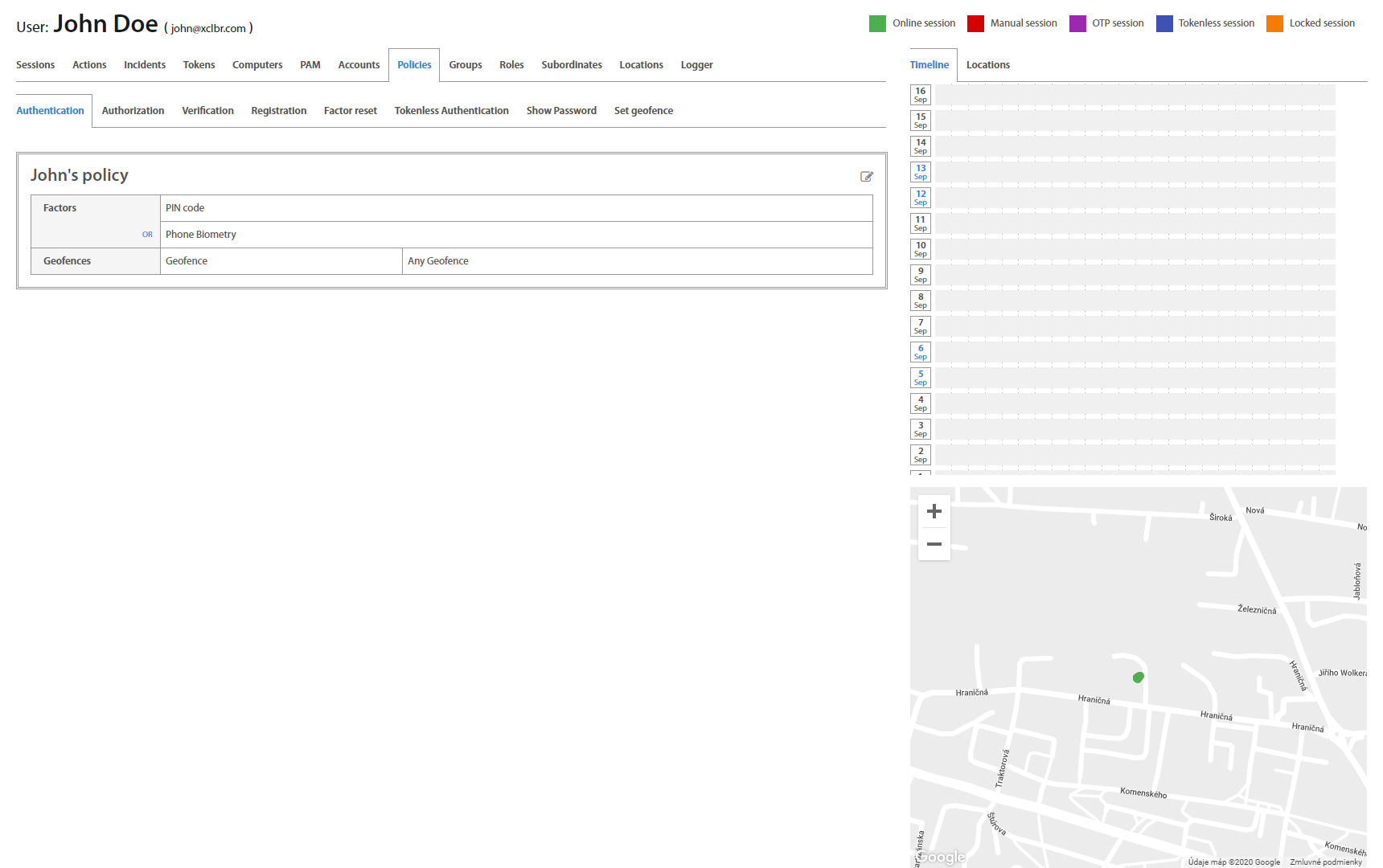
User: Policies¶
Policies tab serves to review security policies assigned to the User. With Excalibur, a different set of authentication factors or geofence rules could be set for every Excalibur Action. Administrators can set these rules on the Security policies page.
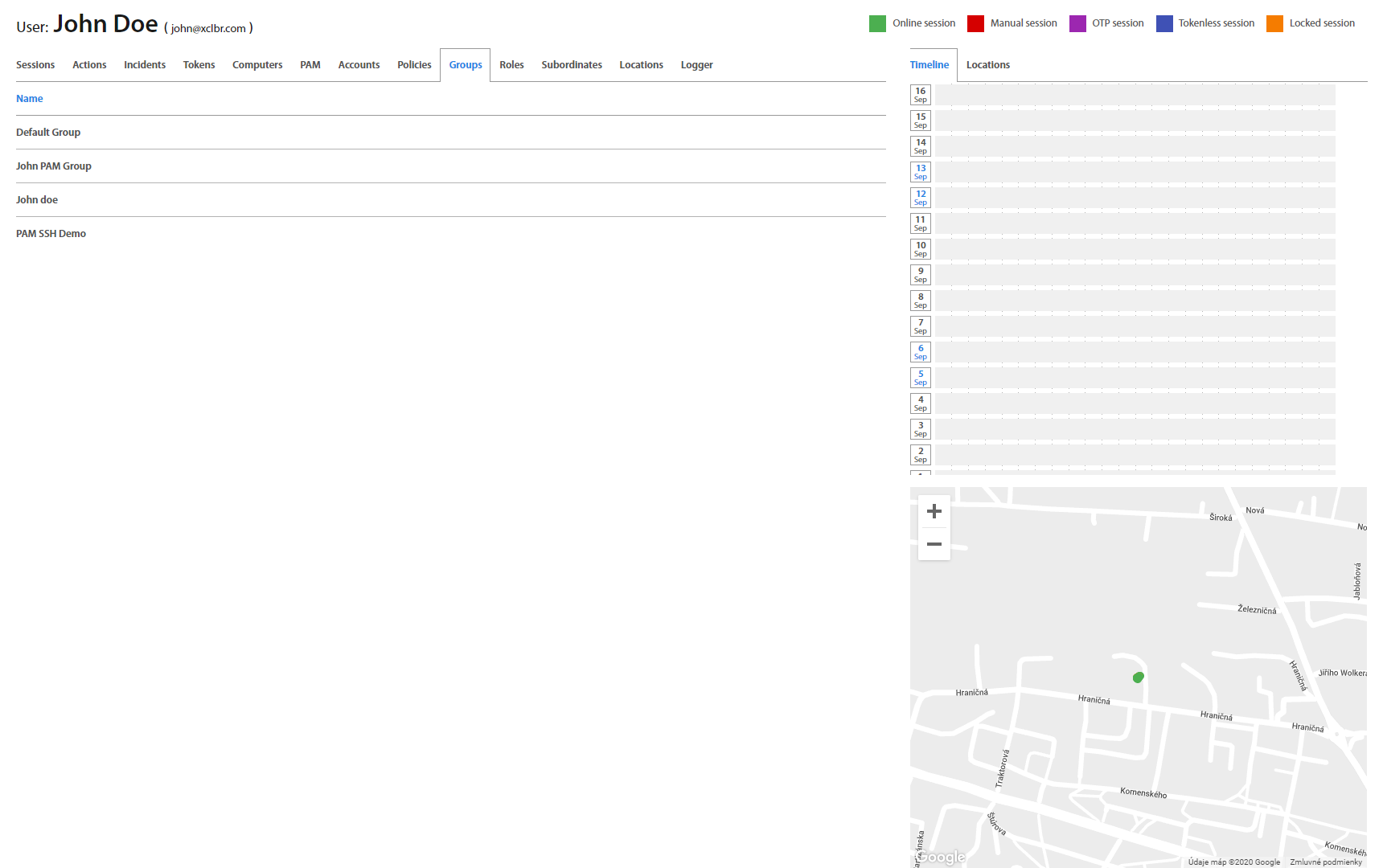
User: Groups & Roles¶
Groups tab displays every group the User belongs to. Clicking on a group name will show Groups > Users page, where groups could be reviewed, edited or created.
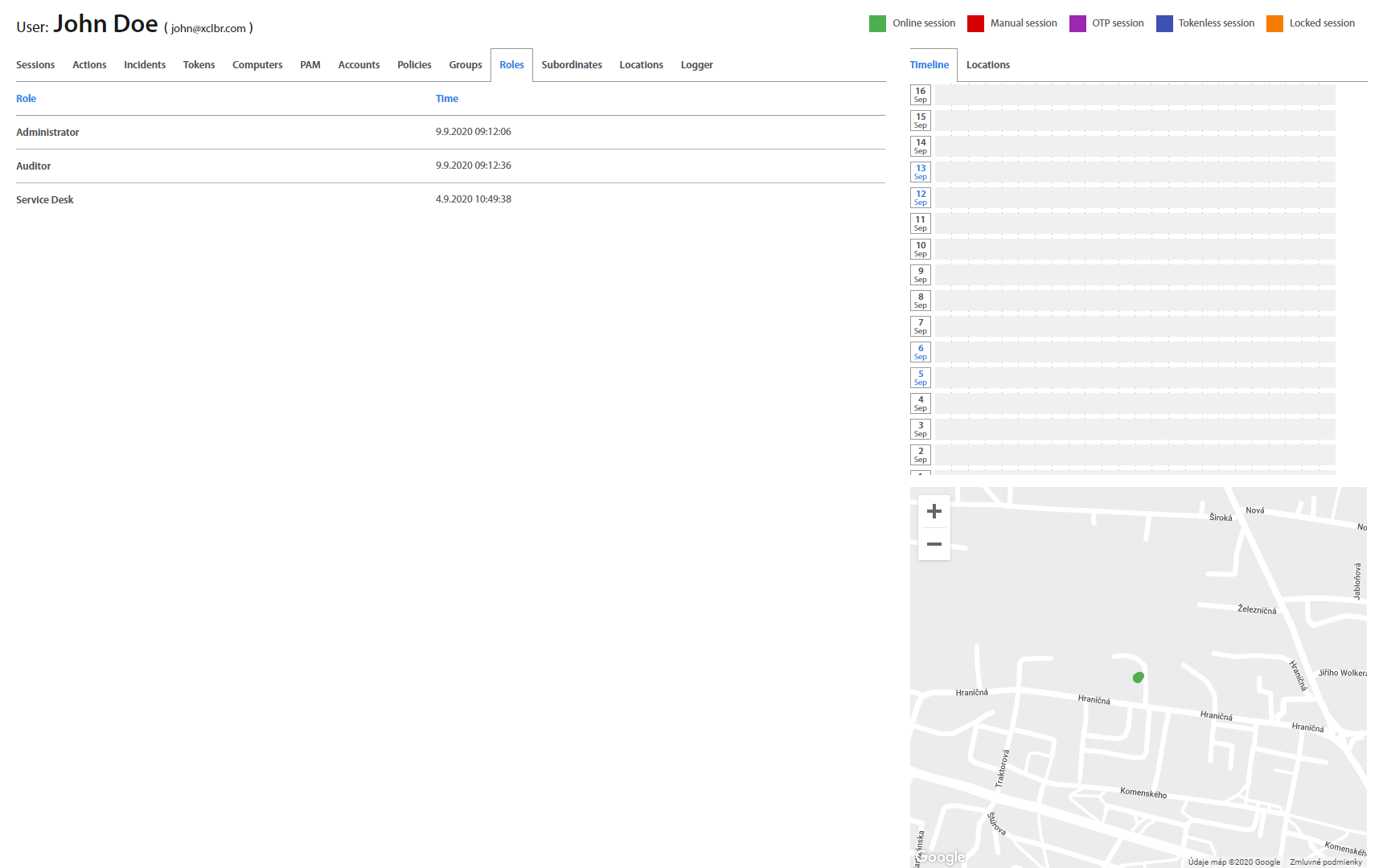
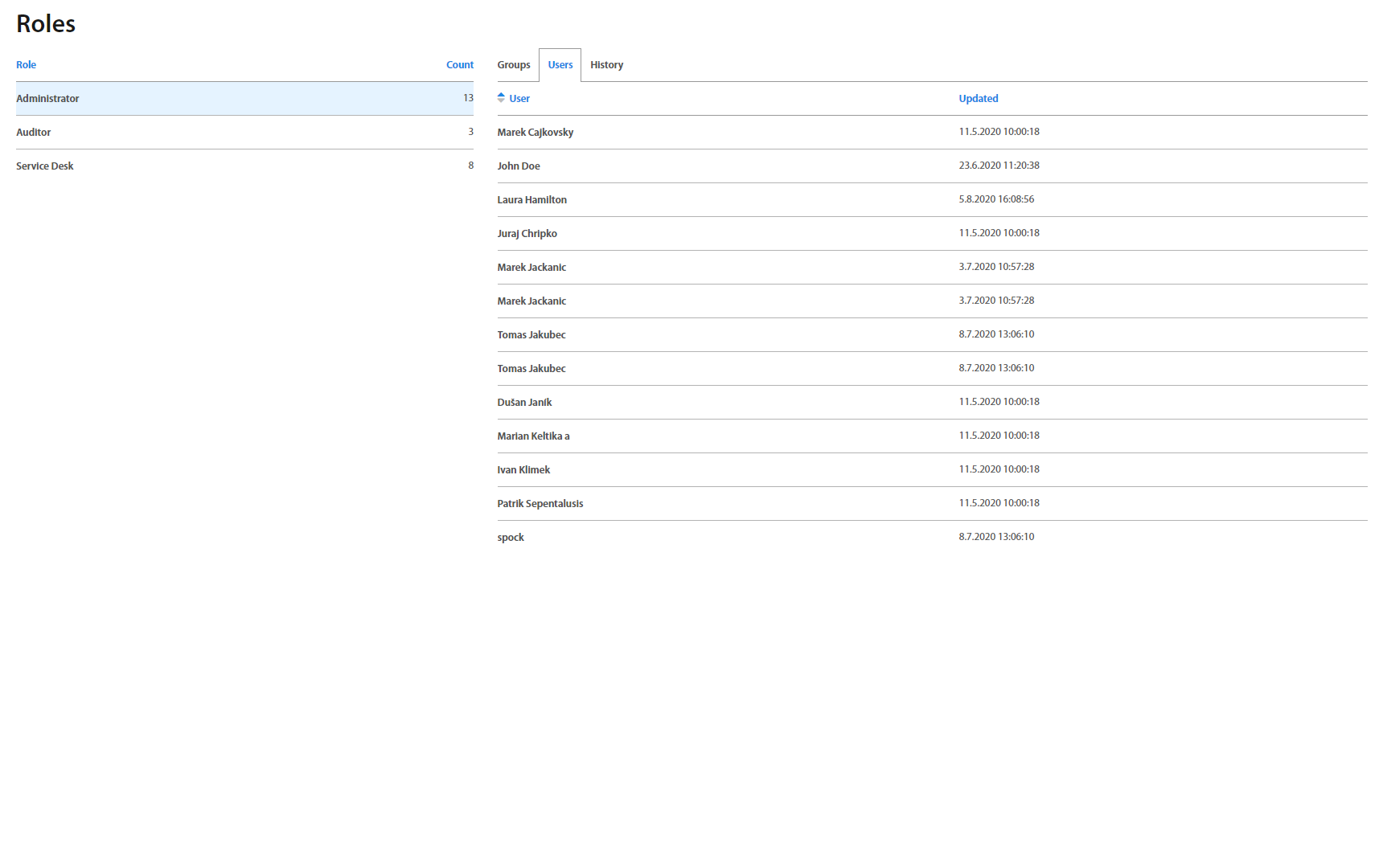
Roles tab contains all roles assigned to the User. Roles could be managed on the Security > Roles page.
User: Subordinates¶
Subordinates tab contains all User’s subordinates in the company hierarchy. Clicking on the subordinate's username shows his / hers account details page (User page).
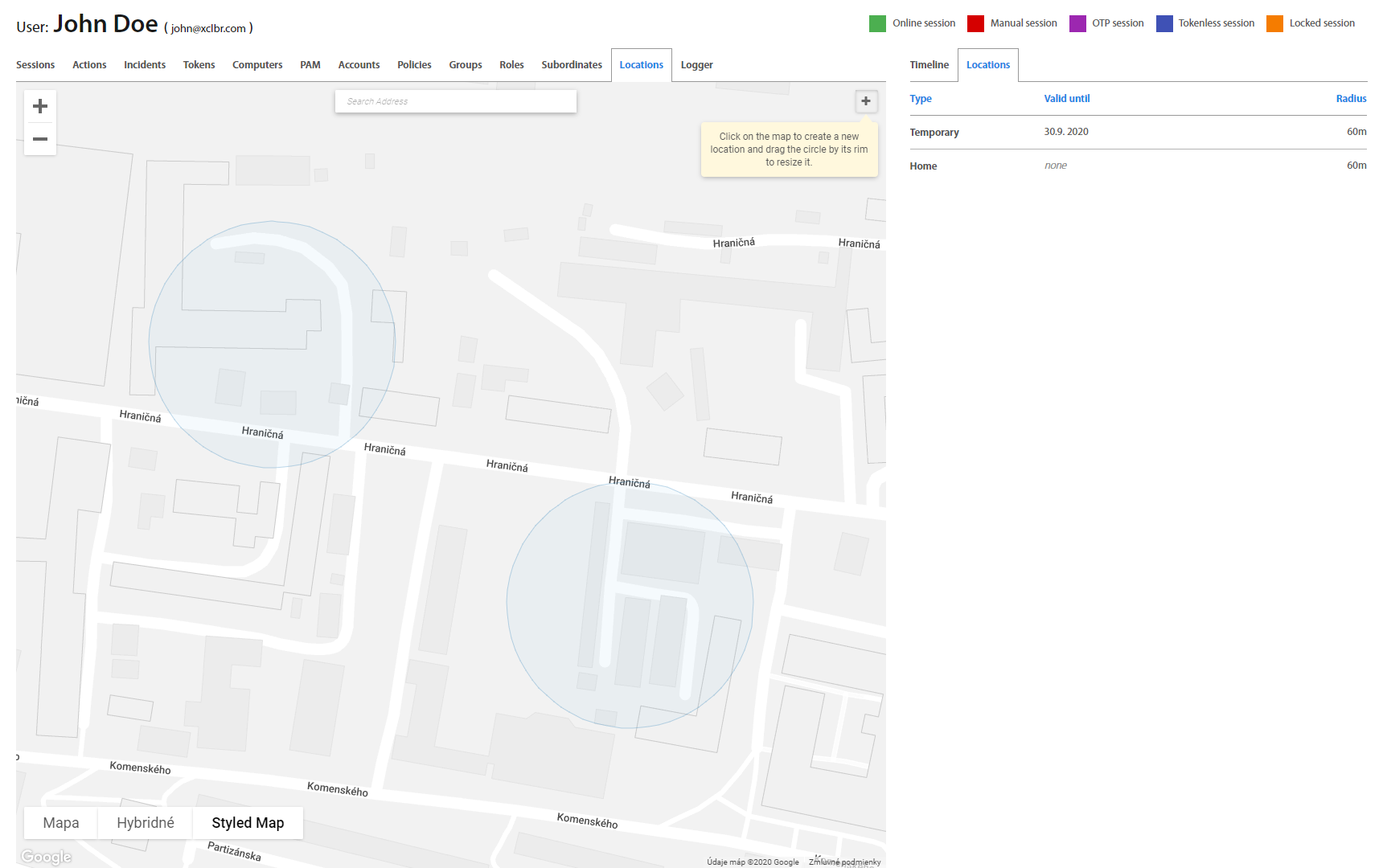
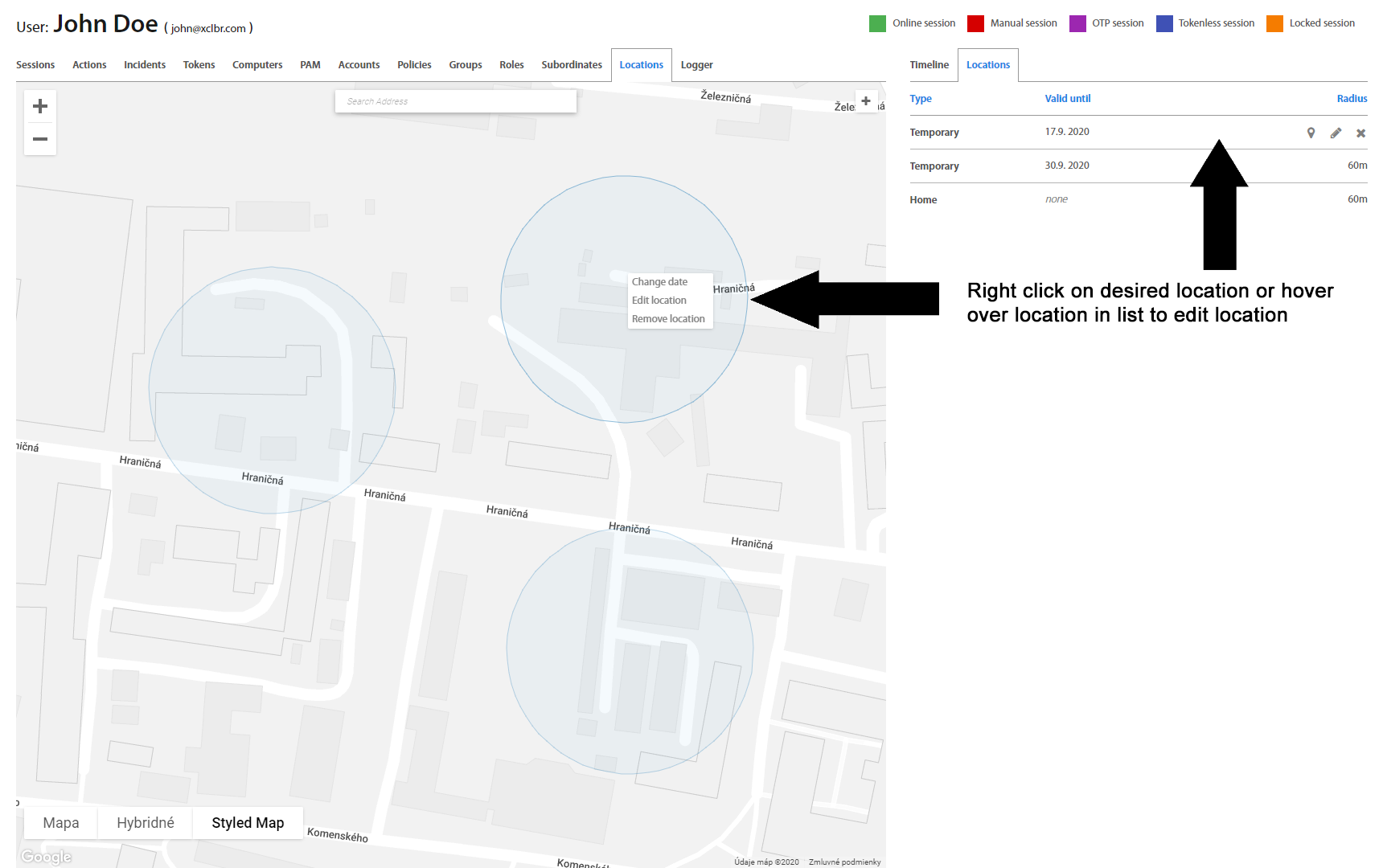
User: Locations¶
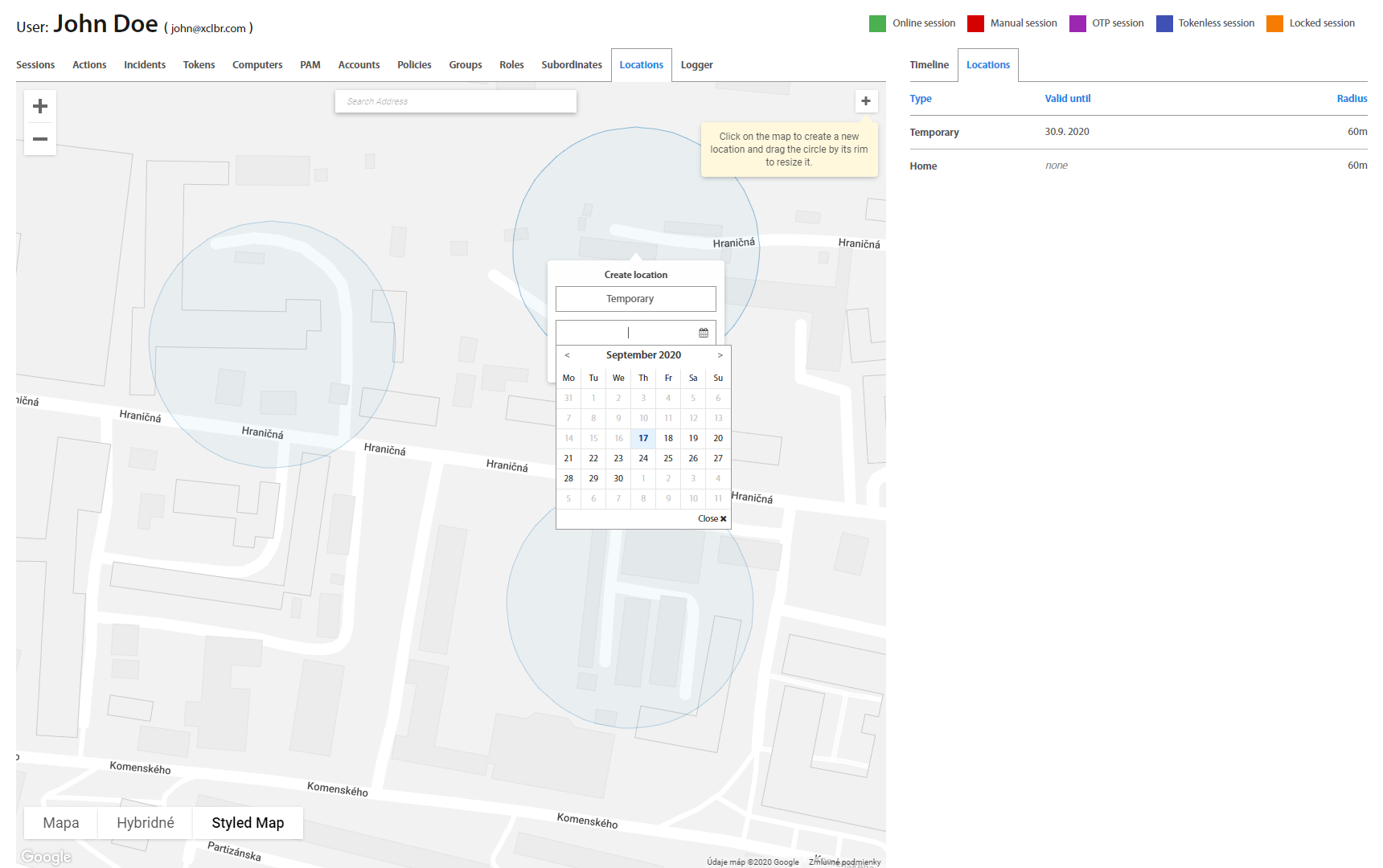
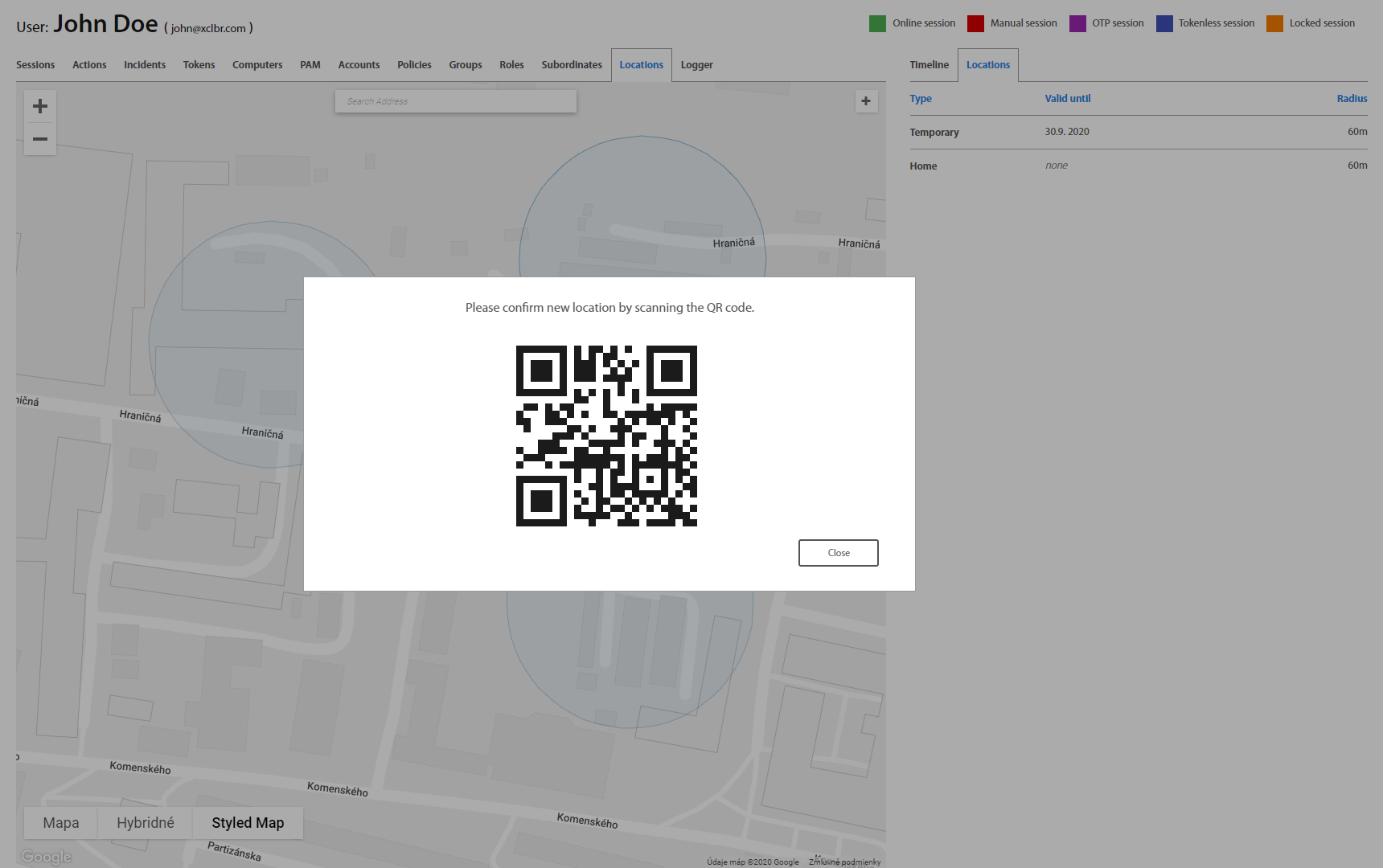
Locations tab contains the list of all User’s locations from where the User most probably will be logged into PC. User or Administrator may define different locations like Home or Temporary location. Locations may be used to create a Security policy for specific User to allow login only from Company’s Office premises, Home in case of a home office or Temporary location in case of a business trip. For Temporary location date until location will be valid might be specified. Locations can be added by clicking on the “+” button in the top right corner and dragging the circle around the map. If needed to edit or delete location, click on circle by right mouse button or click on selected location in list and select the desired action. For Home location can be changed position only and for Temporary location can be changed expiration date, radius and position. All changes of location have to be authorized with User’s / Administrator’s token by confirming push notification on token or by scanning the QR code.
Note
Remember, the temporary location expires at the time 23:59:59 set on the server. If you will be logged from another time zone you must select another day. Home location has 60m radius, and it is not possible to change it.
Edit location
Change date
Remove location
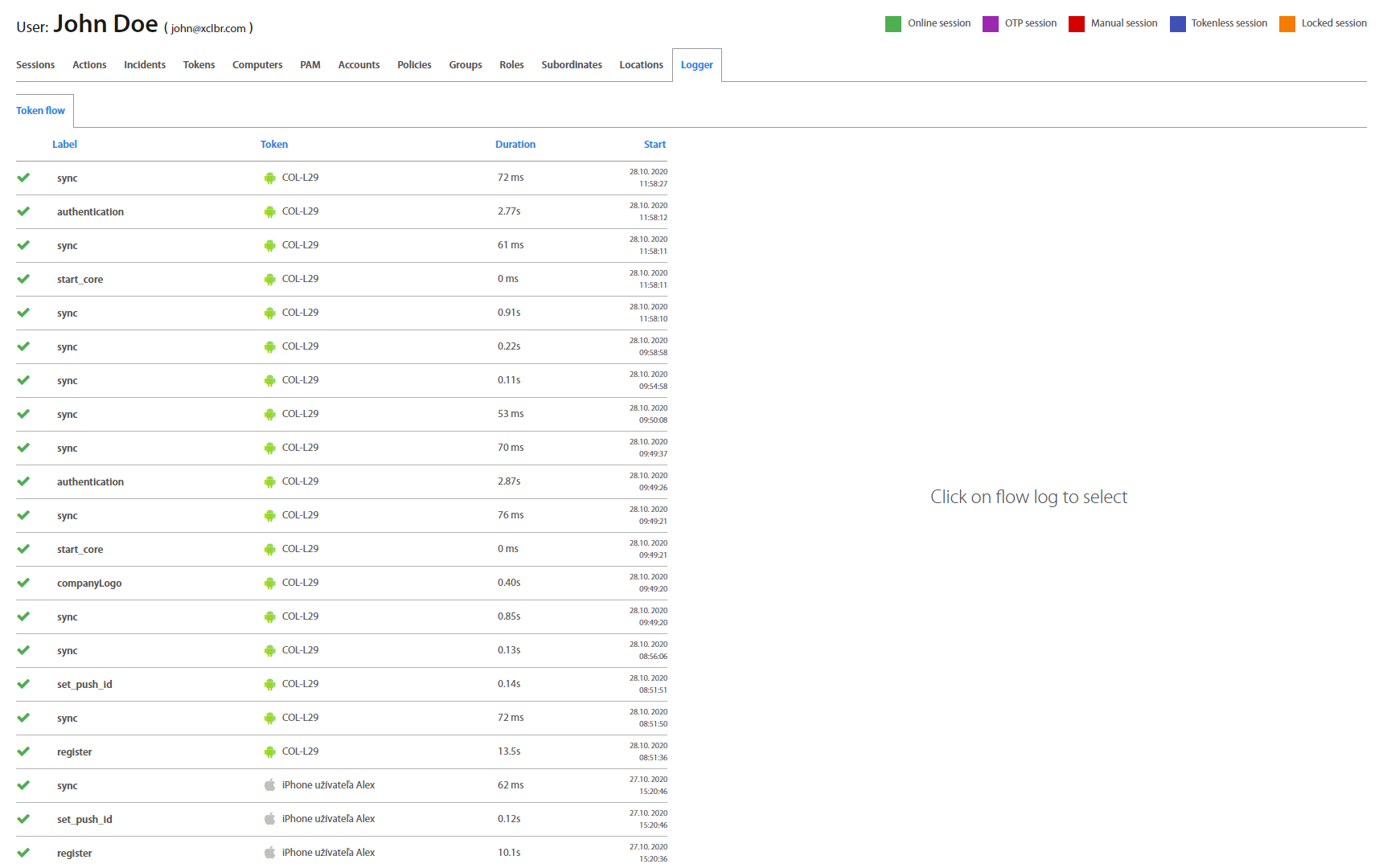
User: Logger¶
Logger tab provides information about each action of the user's token. On the left side is a list of all actions with their description such as status of action, action, used token, duration of action and datetime of action. To load all actions from the user's token is necessary to enable Usage & Diagnostics in the user’s token. In case that this option is not enabled, only a few actions are shown /for instance: authentication, sync… /.
Status: - successful operation, - error, - warning, - timeouted
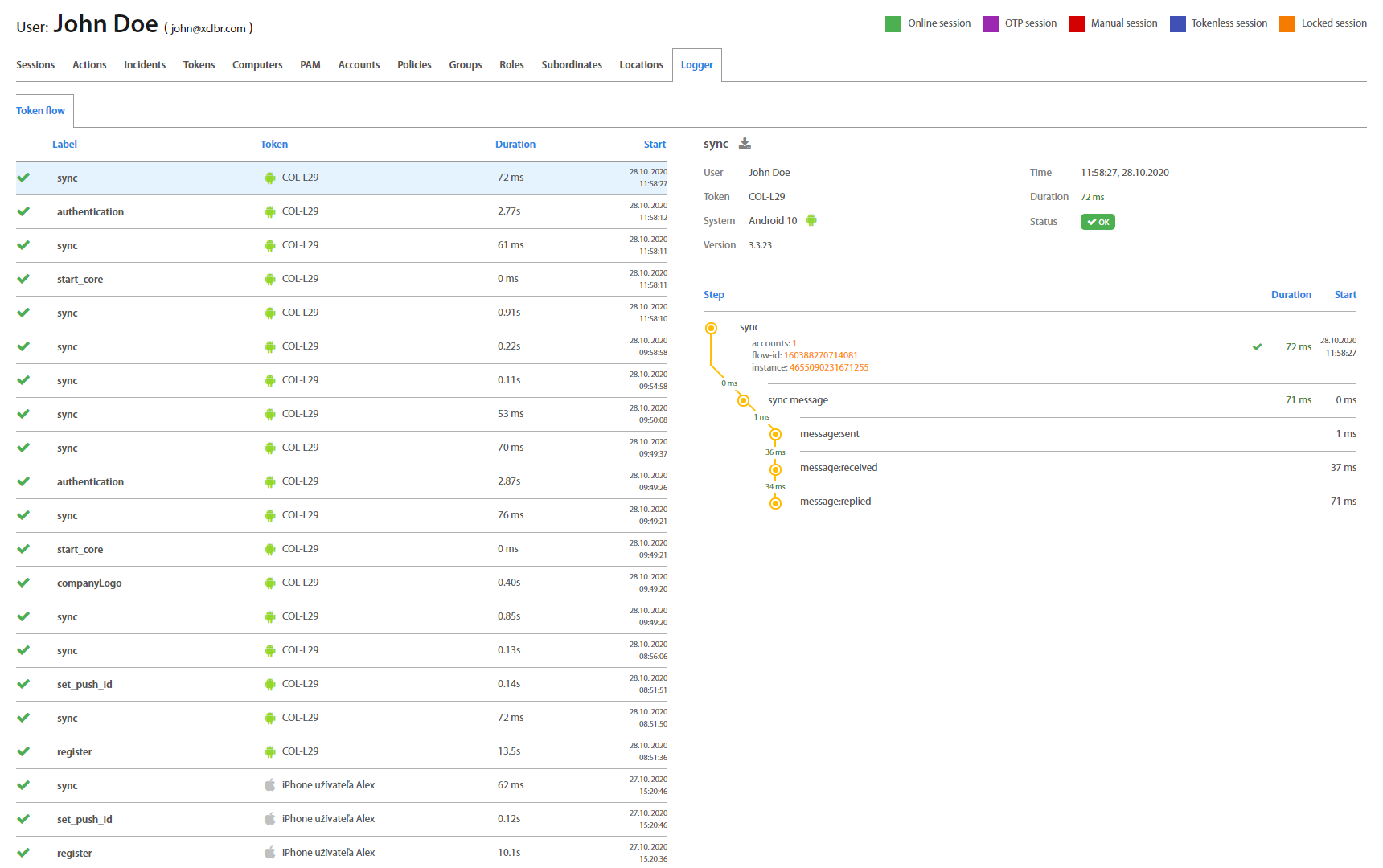
By clicking on the specific action, the detail of the action shows up. First part of detail contains information about User, user’s token as well as duration and status of action. The second part contains a diagram of flow with steps of action and duration between steps. Action may have additional parallel steps or data. By clicking on the button is possible to download the flow in the html format.
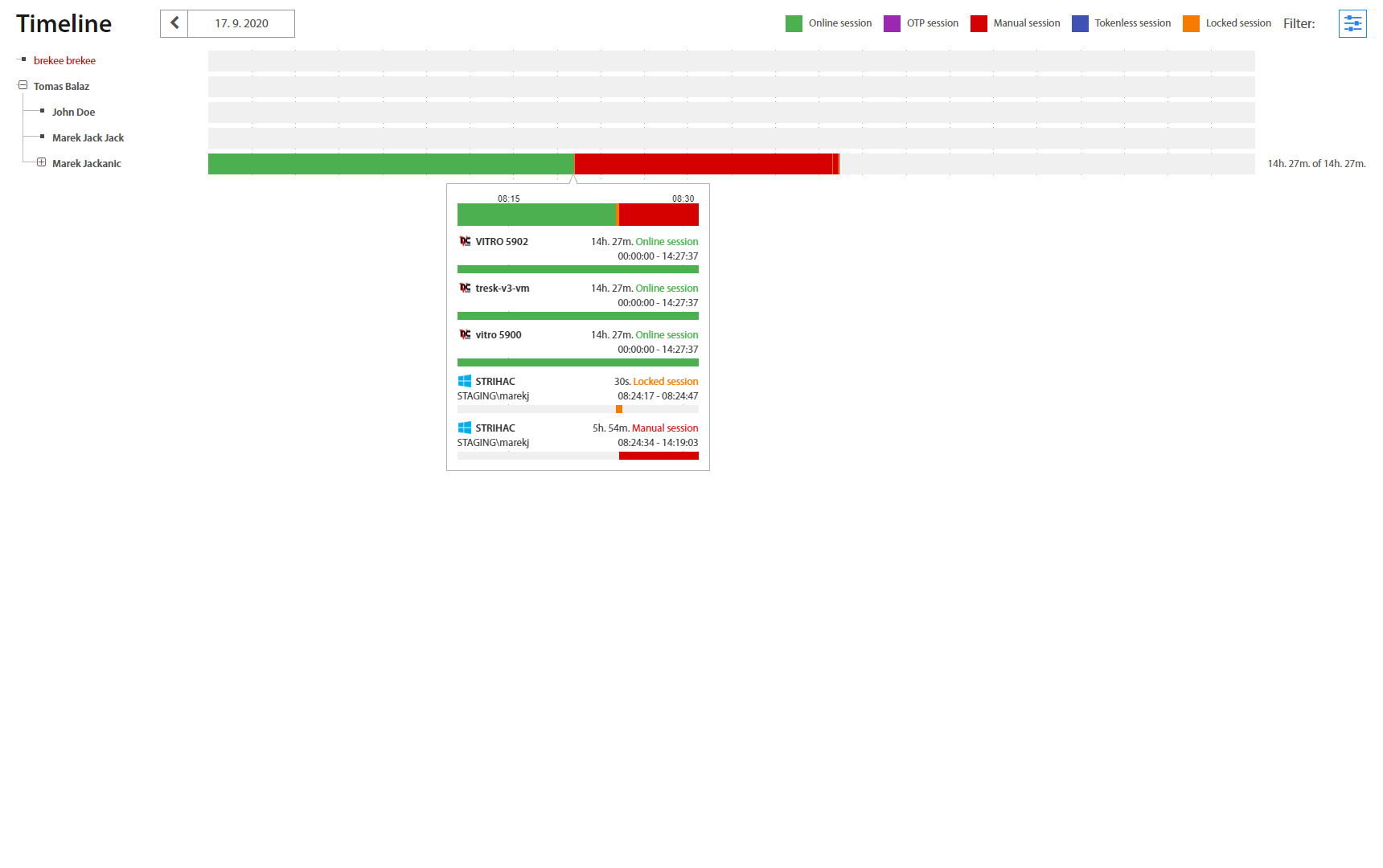
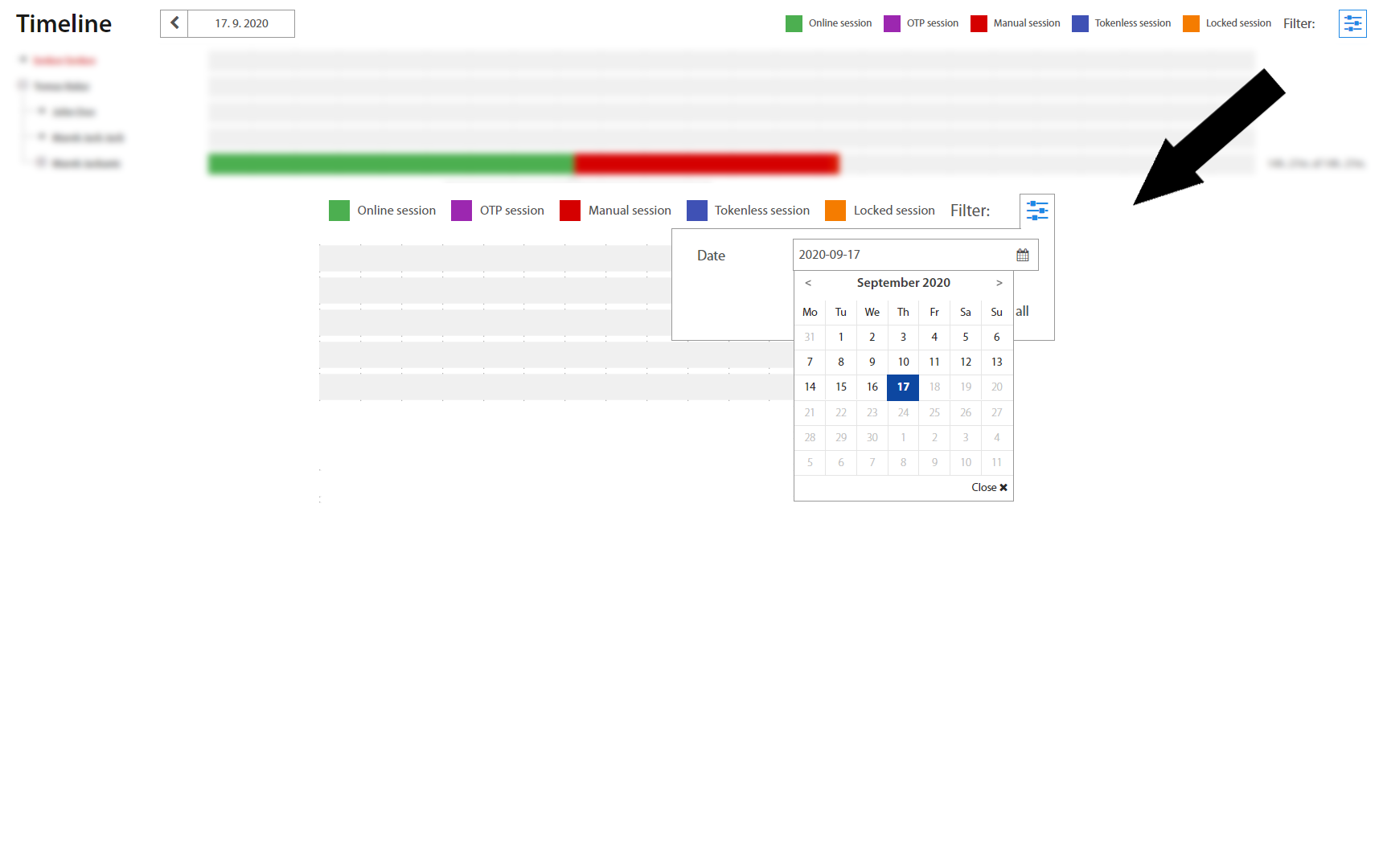
Timeline¶
Timeline page is a summary view of Users’ activity during a given day. Timeline visualizes when every User was logged, locked or disconnected during the day. By hovering and dragging with the mouse over the timeline, detailed information about sessions in specific time shows up. Clicking on a username shows the User account detail page.
Selected date is shown above the timeline and could be changed to previous / next day simply by clicking on the left / right arrow next to it, while the Filter in the top right corner enables a selection of a specific date from a calendar.
Actions¶
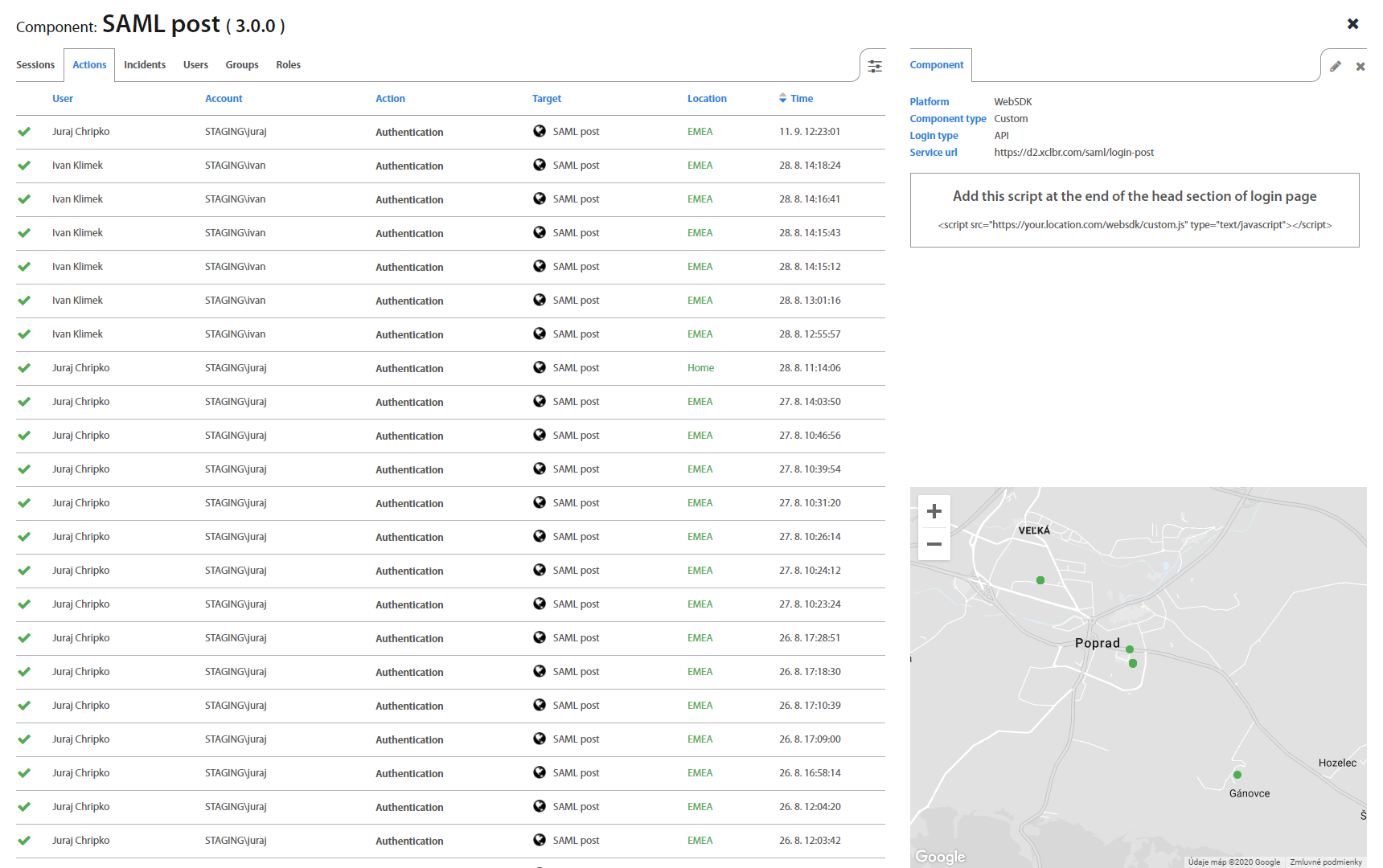
Actions page lists all actions took by every User, such as Authentication, Authorization, Verification, Registration, Factor reset, Tokenless Authentication, Show password and Set geofence. By clicking on an individual Action, detailed information shows up.
Registration¶
At first, User needs to register an account to perform any other action in Excalibur. Registration starts on a Client where User clicks “Register” on the Excalibur login screen and proceeds with self-registration following on-screen instructions. During registration User sets all authentication factors required by the security policy on his/hers Token, which initializes it.
Authentication¶
Authentication or Login is an intent-based action, and the only one in Excalibur which can operate in an online as well as offline mode. User performs his/hers intent by scanning a login QR code from a Client with his/hers Token. The login QR code is dynamically changing - by default Client generates a new one every 15 seconds with 90 seconds validity. Authentication factors are then verified based on the security policy and if it succeeds, in online mode the User is automatically logged into the Client, while in offline mode, on User’s Token is presented an OTP code, which user needs to enter on the Client’s Excalibur login screen to log in.
Authorization¶
Authorization or Action Confirmation is a push notification based action, for example VPN Login (in which a username needs to be entered) will trigger a push notification for a Token of a User specified by the username. On the Token the User is asked to confirm given action with exact specification of what is being confirmed. Authentication factors are then verified based on the security policy and if it succeeds, User’s action is authorized. RADIUS is currently the primary use-case of Authorization.
Factors Reset¶
Registered Users have an option to reset their authentication factors on their Tokens. Firstly, authentication factors are verified based on the security policy and if it succeeds, User proceeds to set new factors.
Verification¶
In case of verification a User with appropriate privileges, e.g. Manager (Verifier) using his/hers Token confirms another User's (Initiator) identity and action. Verification begins either directly by scanning a verification QR code from initiator’s Token, or by receiving a push notification, or via Dashboard. Verification can be configured in the security policy as a required action for any Basic Action or any policy violation. Basic Action’s flow is then modified to accommodate the Verification after the usual authentication factors verification succeeds on the Initiator’s side. If successful, the Verifier is prompted to confirm the action using his/hers authentication factors on his/hers Token. Also, every security policy change requires a verification of the change by the Administrator.
Tokenless Authentication¶
If a User forgets his/hers Token, or there’s any other reason a User cannot use or doesn’t have his/hers Token at the moment, there’s a backup option to utilize a Tokenless Authentication. In this case, User begins the process on Client’s Excalibur Login screen, selects “Forgotten phone”, inserts his/hers name, PIN and a reason why his/hers Token isn’t available at the moment. If entered name and pin are verified successfully, this request triggers a usual Verification process in which any verifier designated to verify this User based on the security policy, verifies the action either in person or remotely. Based on the user's policy, verifiers have the option to select a time interval on theirs tokens during which the user can login without further verification on a particular computer. For further tokenless login on this computer, User must type username, PIN and give the reason
Info
For instance Let’s say that User’s tokenless duration is set up to 8 hours. If user clicks on Tokenless button and types username, PIN and reason, verification QR code on CPUI screen will be shown. Verifier scans this QR and provides authentication factors and select duration to one hour on token. Now, User can make further Tokenless logins without verification on this computer. In this time interval, user will type username, PIN and the reason only.
Info
In case that login is verified by peers, the duration is set by peer who sets duration as the second in order.
Show Password¶
Registered Users have an option to display their password on their registered token. If Show Password is allowed by the company's security policy, then User can display own password. On the Show Password tab, all Show password actions are recorded.
Set geofence¶
Set geofence’s policy provides options to set rules to set new geofence or location. Each user who uses Excalibur has an option to set its own home or temporary location by token or dashboard. In the Set geofence tab, all changes of geofence and locations are recorded.
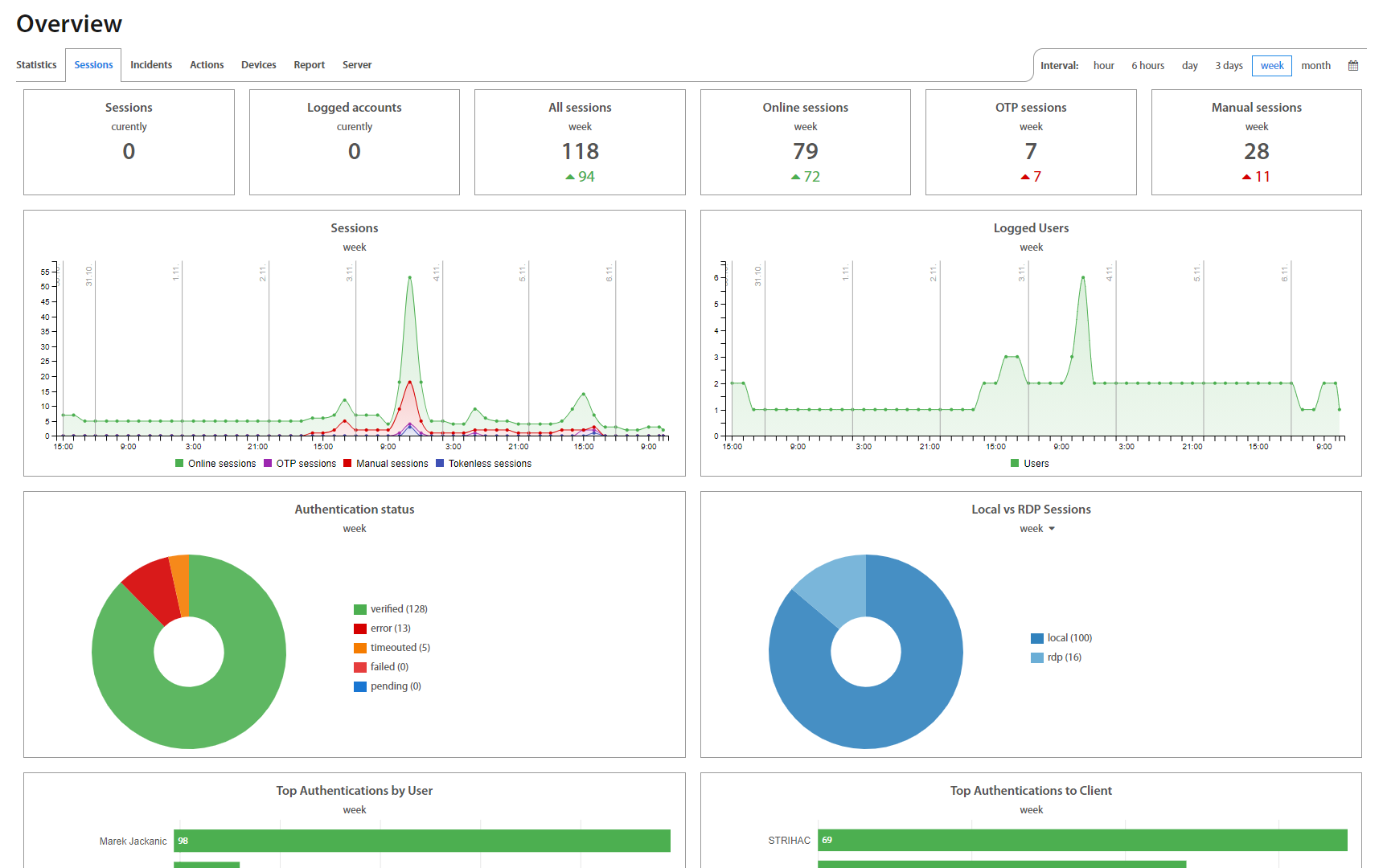
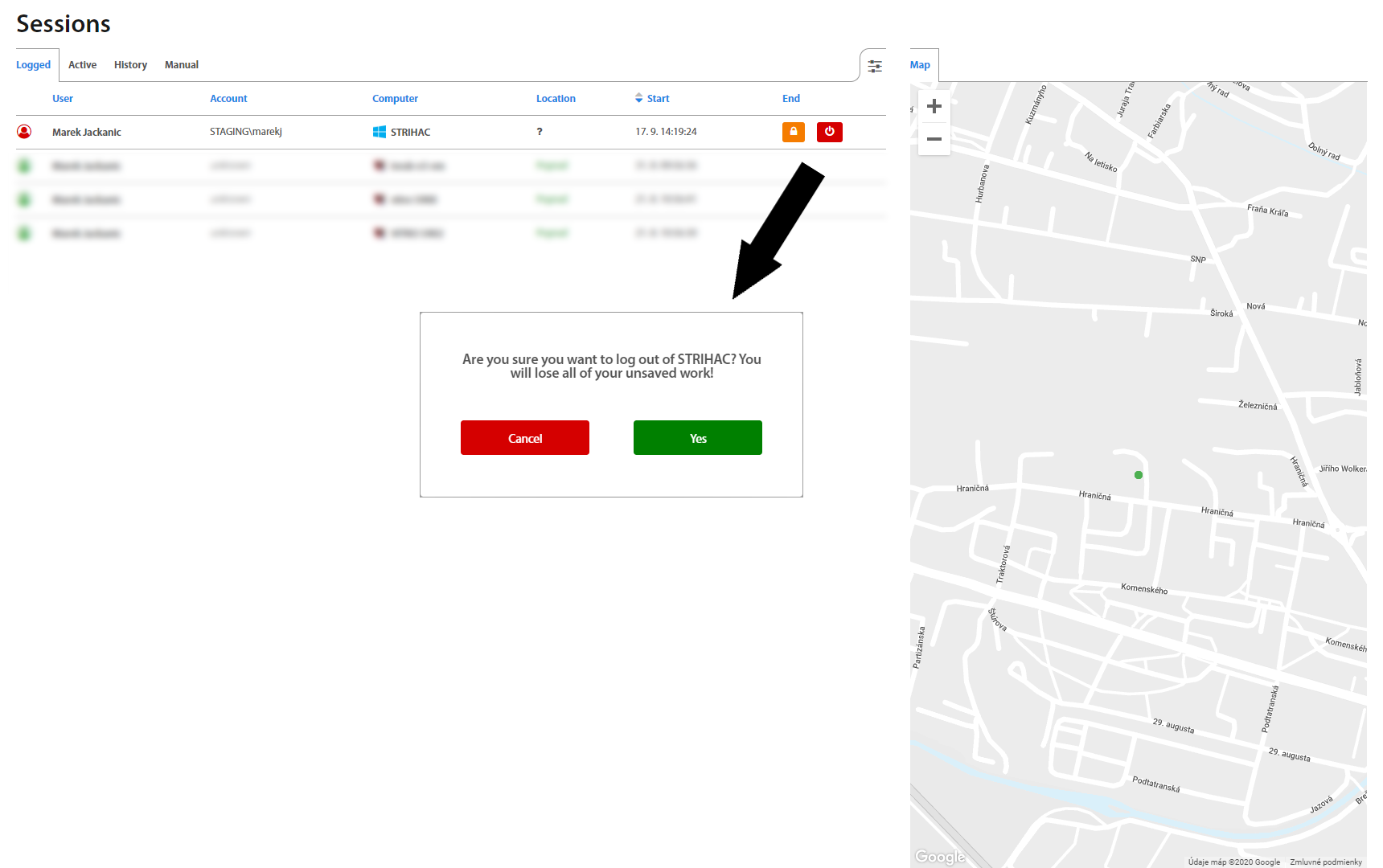
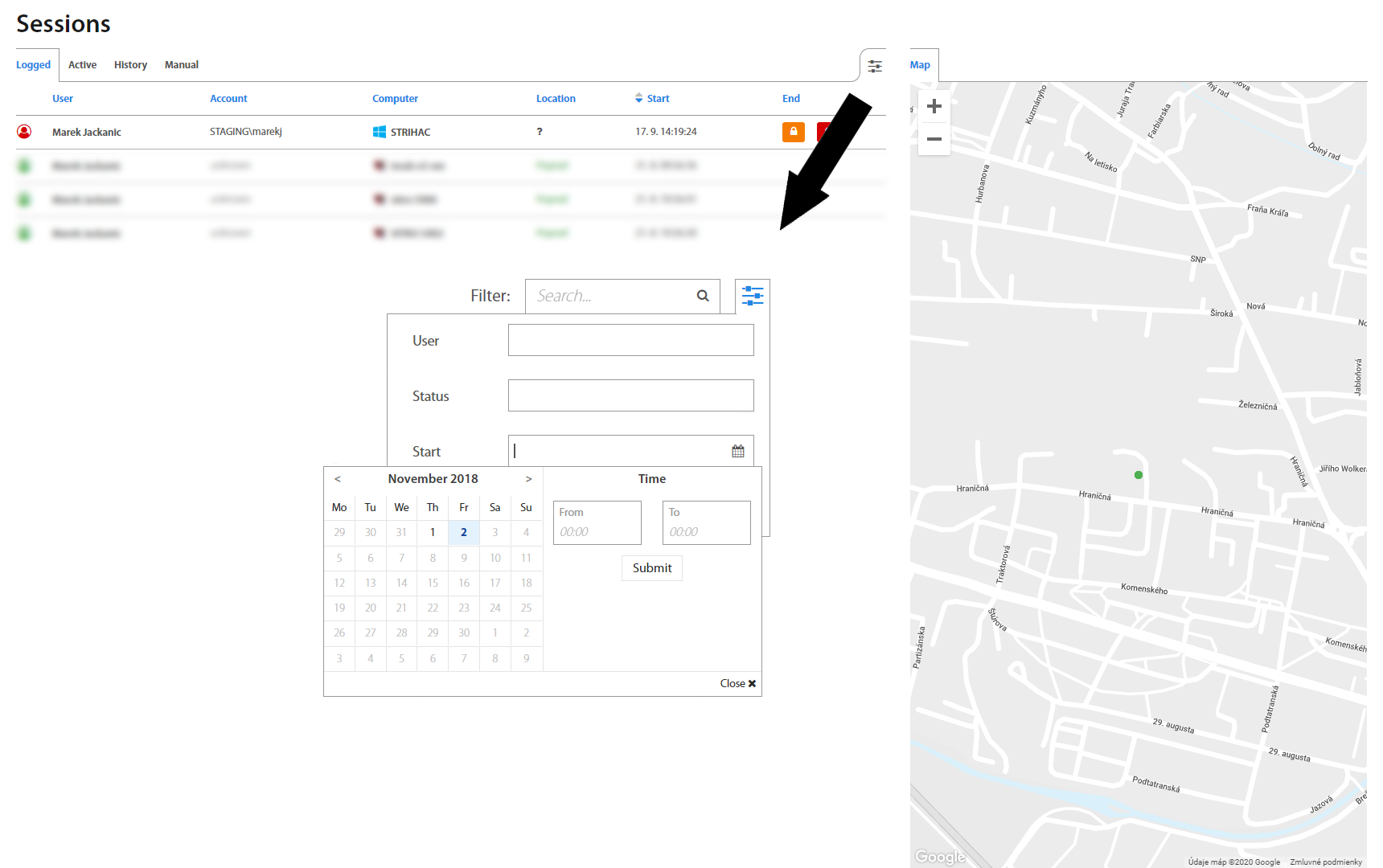
Sessions¶
In Sessions, all Logged, Active, and Manual sessions are located, as well as their History. If a session is still active, it’s possible to lock it or end it (log it out). Buttons for these actions show up by hovering the mouse over a session.
It’s also possible to search in Sessions by username or to filter them by date in the top right corner.
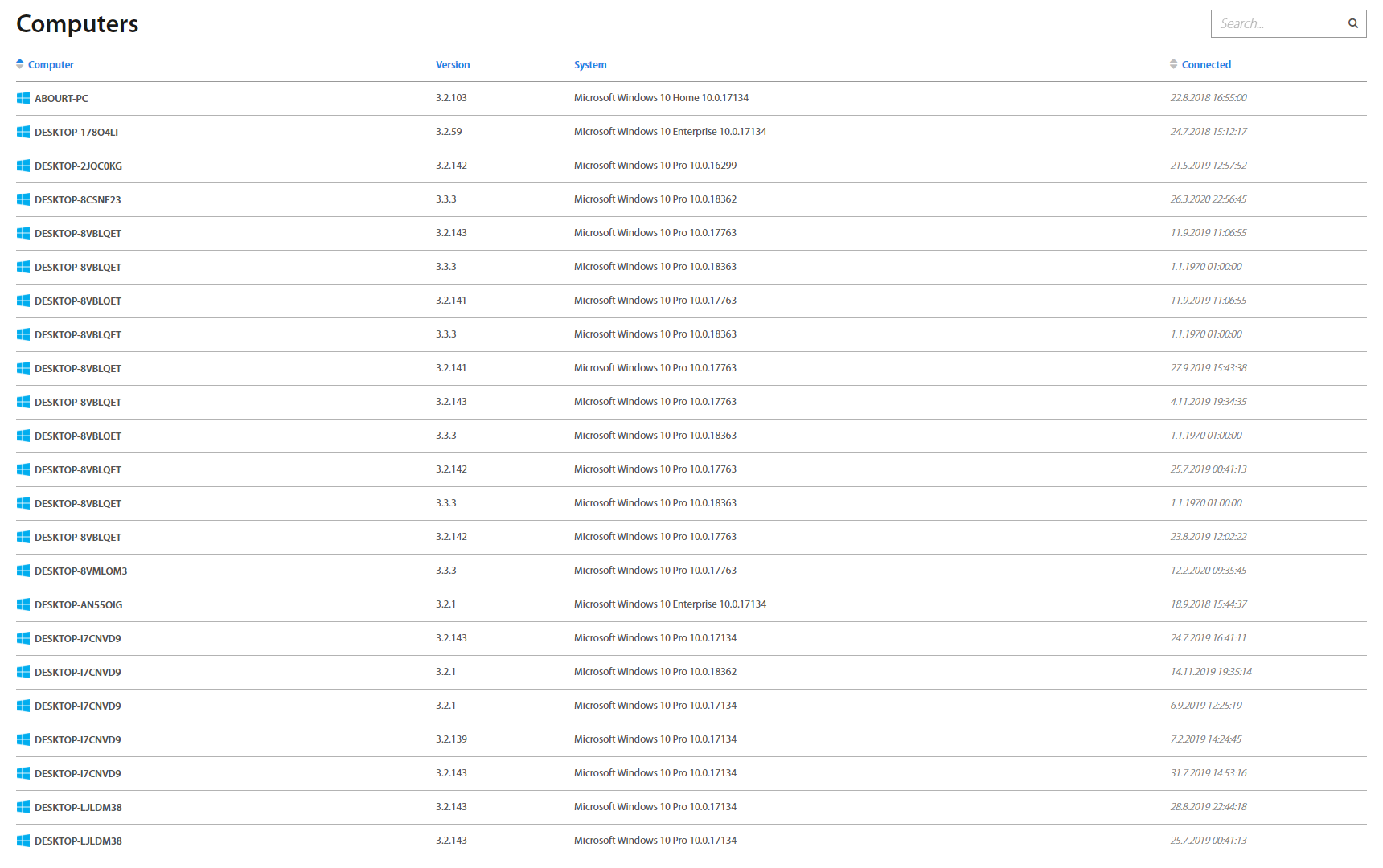
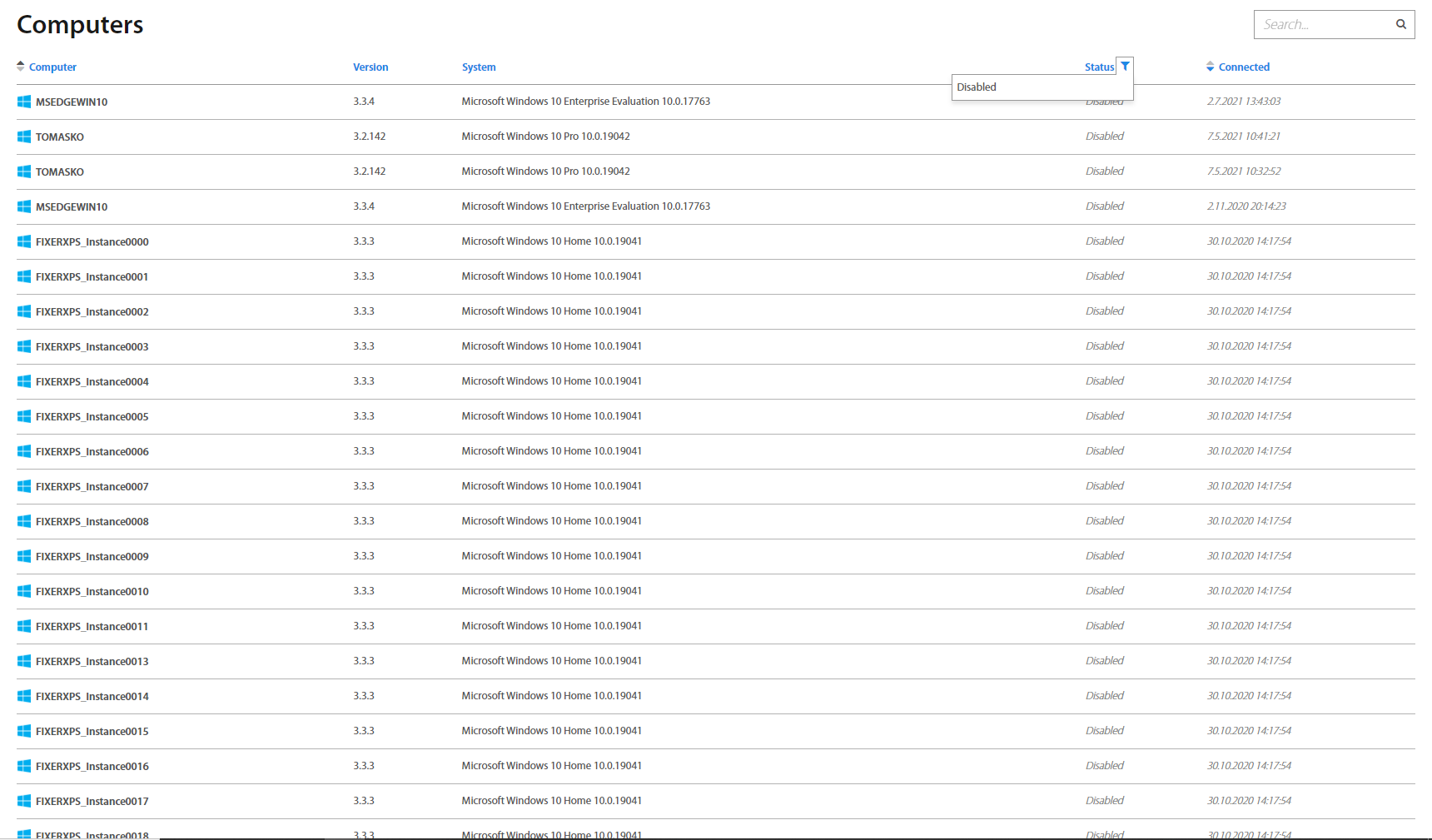
Computers¶
Computers page consists of all computers with their names, Excalibur version, OS and current status information. It’s possible to search for a computer by its name in the top right corner.
Clicking on the computer name shows detailed information, including all Sessions, Incidents, Users and Groups. The same as on the Sessions page, hovering over the session shows buttons to lock or end a session.
Incidents tab lists all Incidents associated with a chosen computer. By clicking on Incident, detailed information shows up.
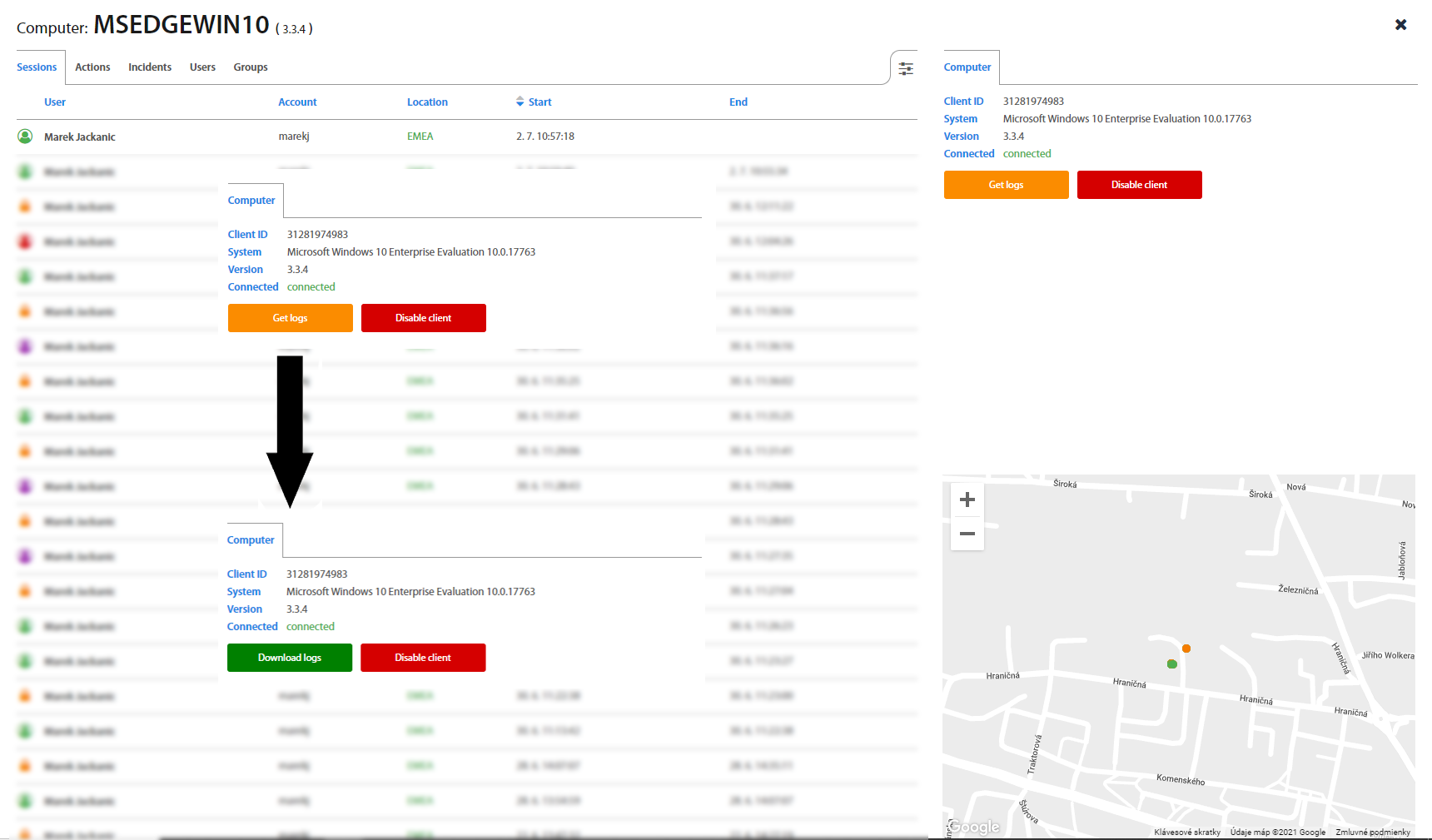
Get computer logs¶
Excalibur dashboard provides option for administrators to download logs from any connected computer remotely. If it is necessary to get logs from the computer, find the selected computer, click on computer and click on Get Logs button on the right side. Logs will be packaged and downloaded by clicking on the Download logs button to administrator’s computer.
Attention
Computer has to be connected /online/ and supported version of Excalibur client application has to be installed on selected computer to download logs.
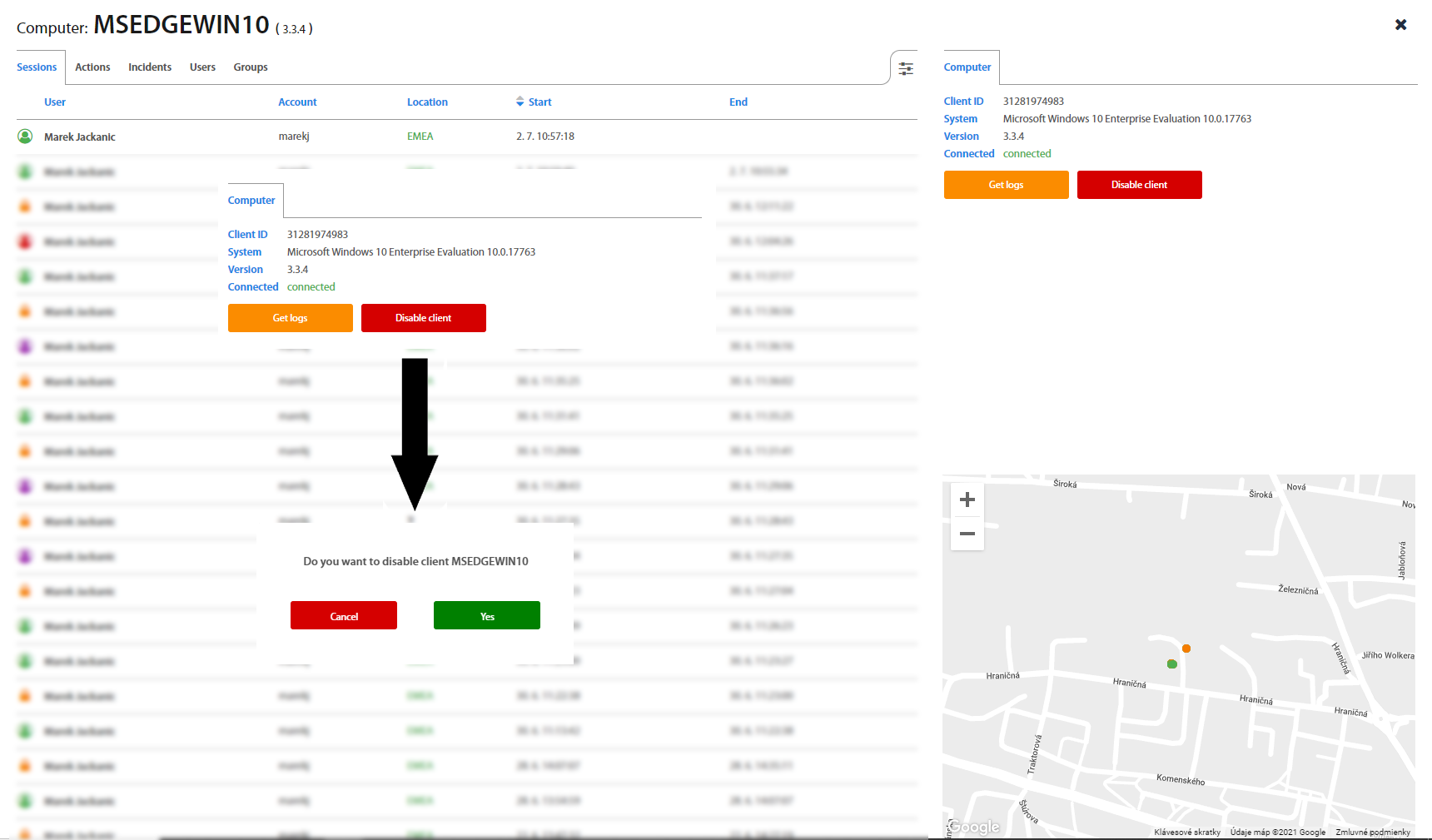
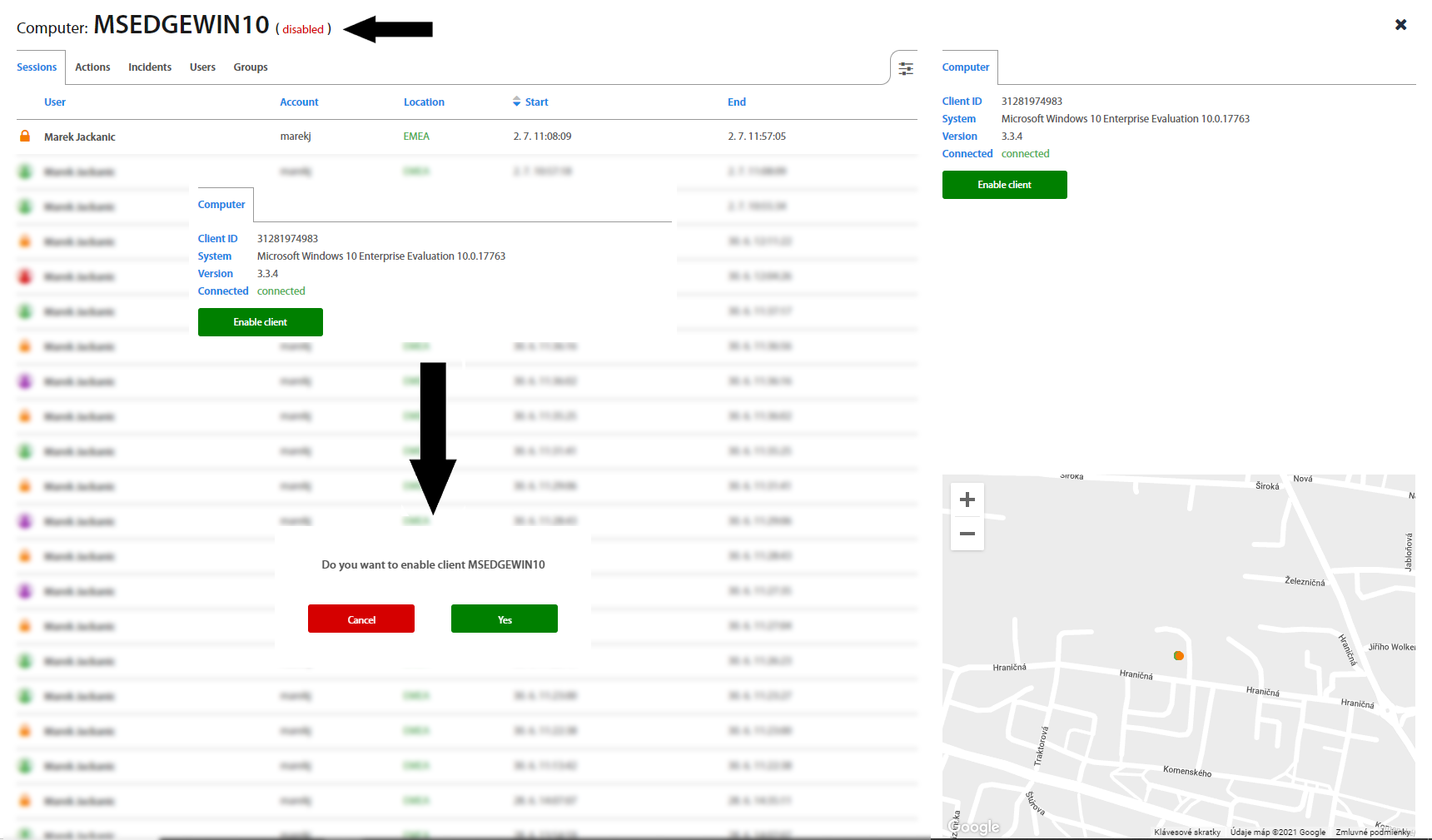
Disable/Enable computers¶
Excalibur automatically disables computers which were not logged more than 90 days. Administrator has option to to disable computer manually. To disable client, click on the Disable client button and confirm your action. To display disabled computers select the Status in the Computer list and set it to Disabled. In case that you need to enable computer, select it from the list and click on Enabled client button.
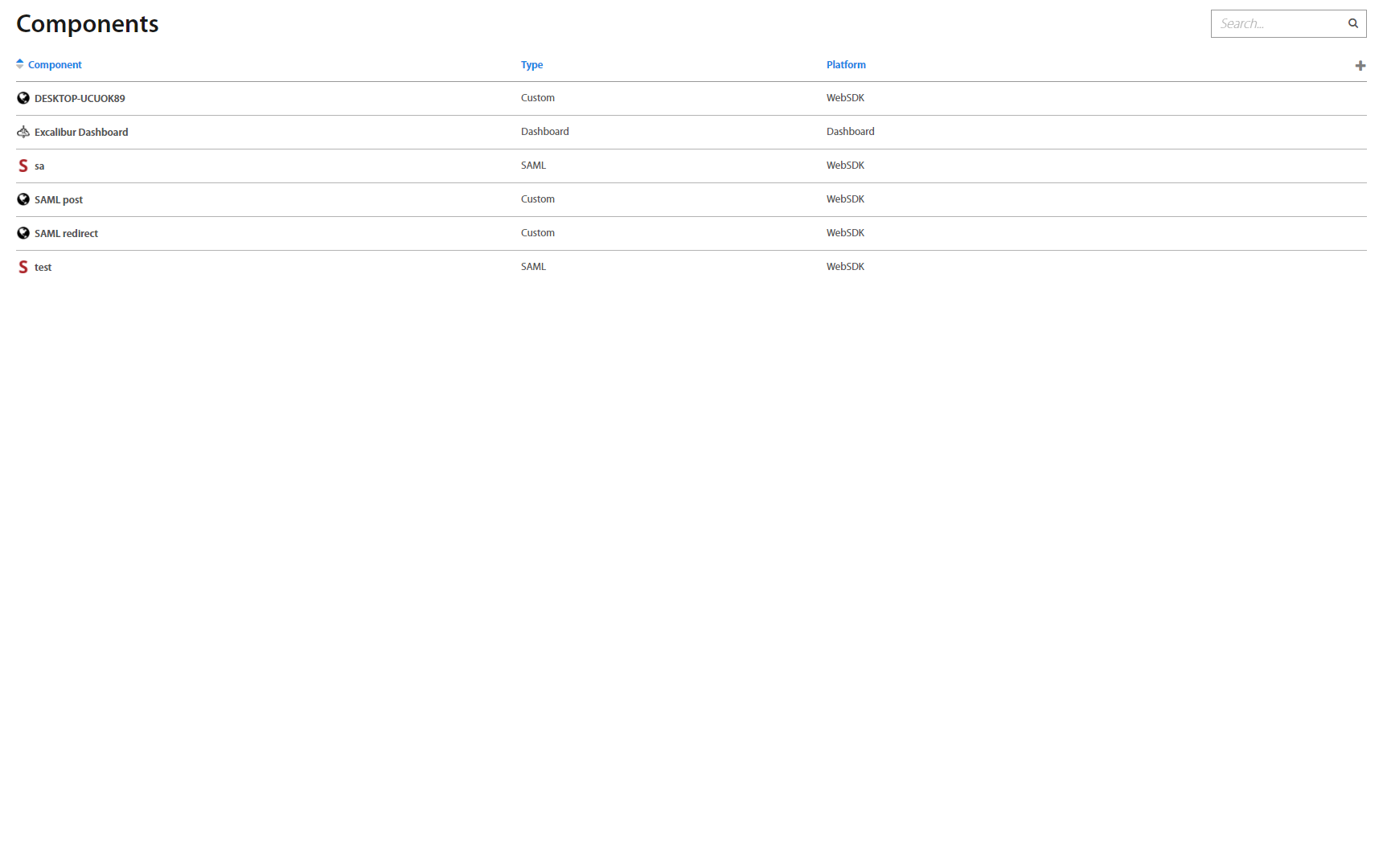
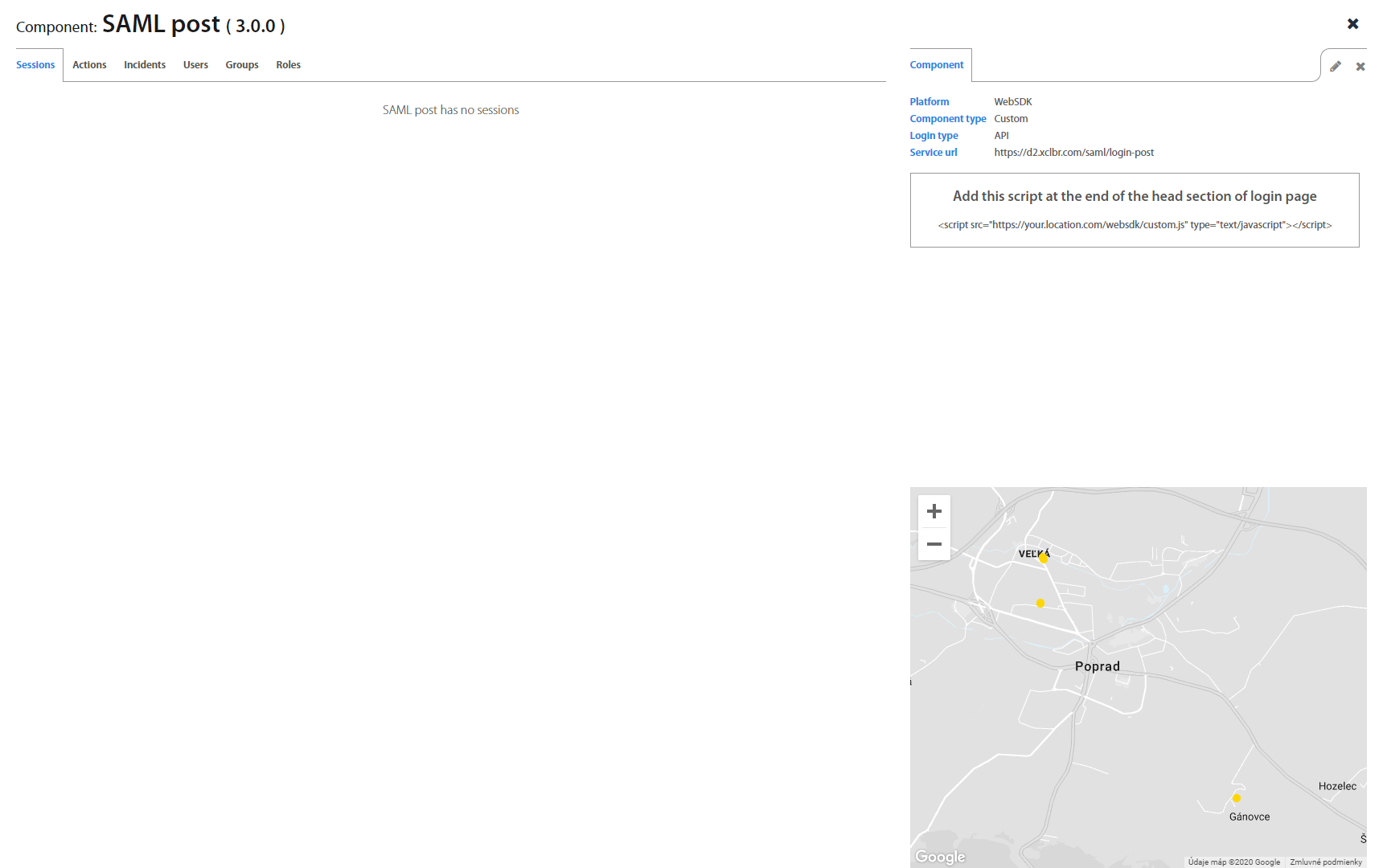
Components¶
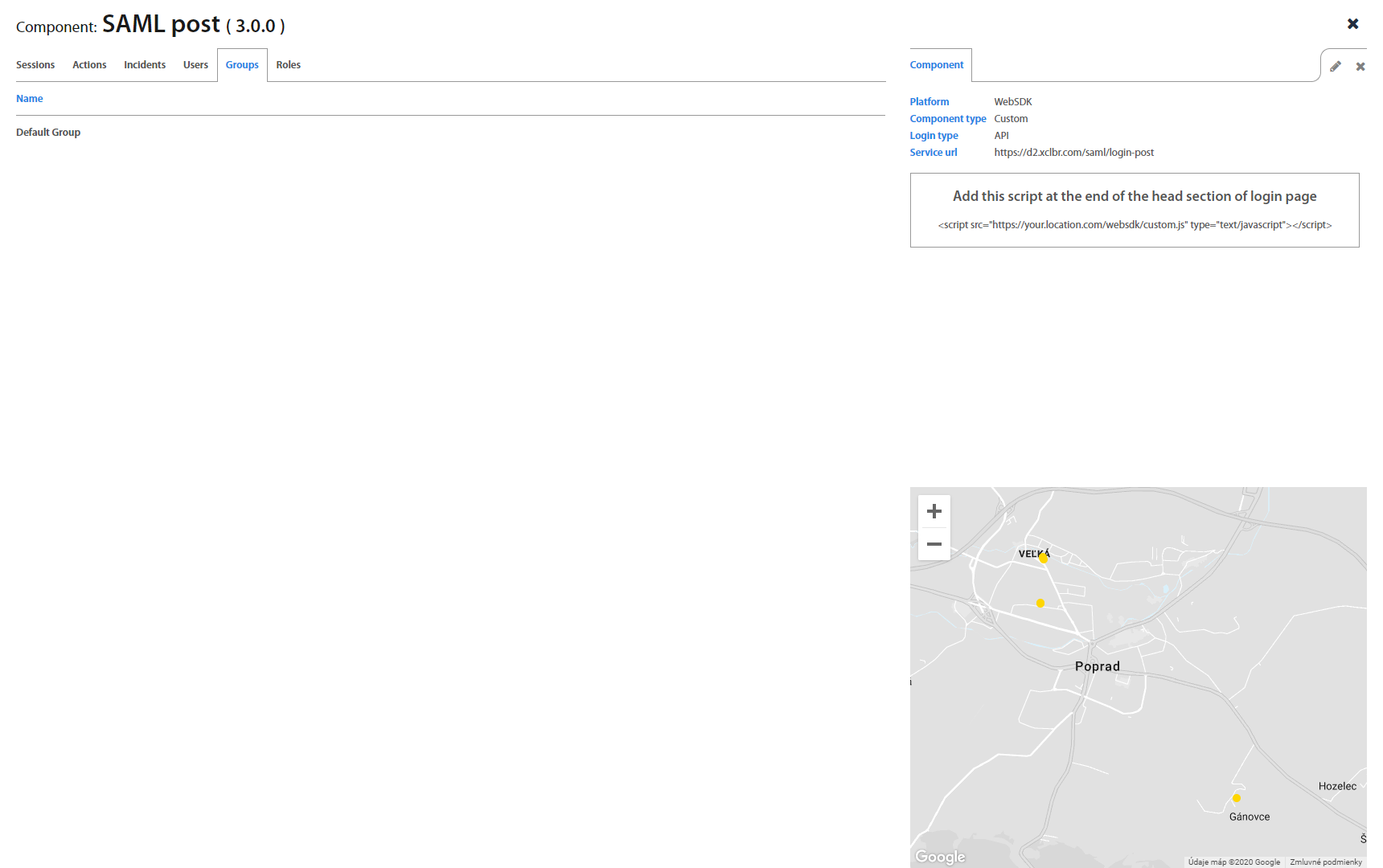
Components folder lists all currently deployed Excalibur components and most importantly their versions. By clicking on individual component detailed information about component shows up.
It’s possible to search for a component by its name in the top right corner.
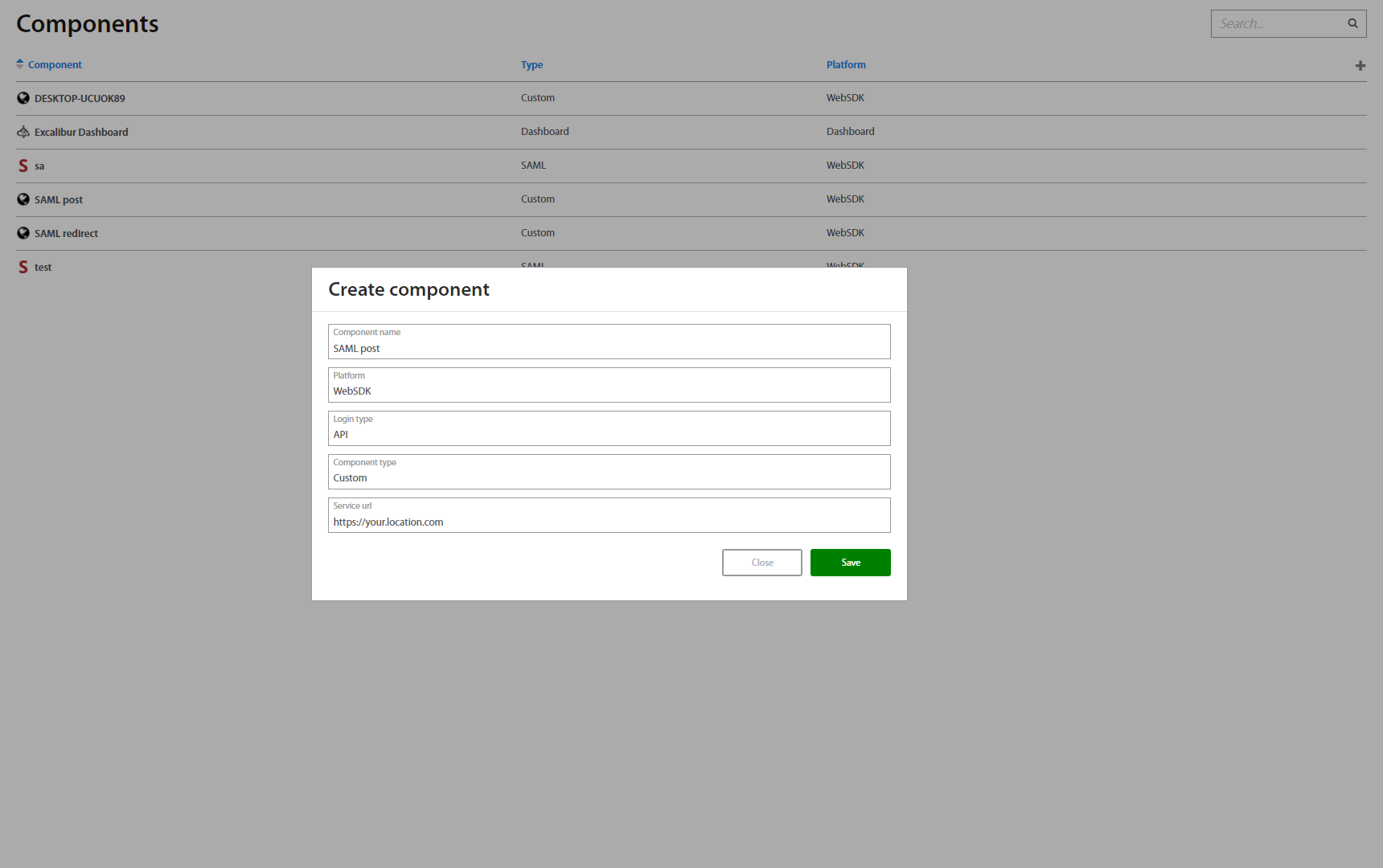
To add a new component, click on the “+” button on the top of the Components list. New window with component settings will open. Creating a new component requires a new component name, platform (WebSDK or RADIUS), component type and service URL.
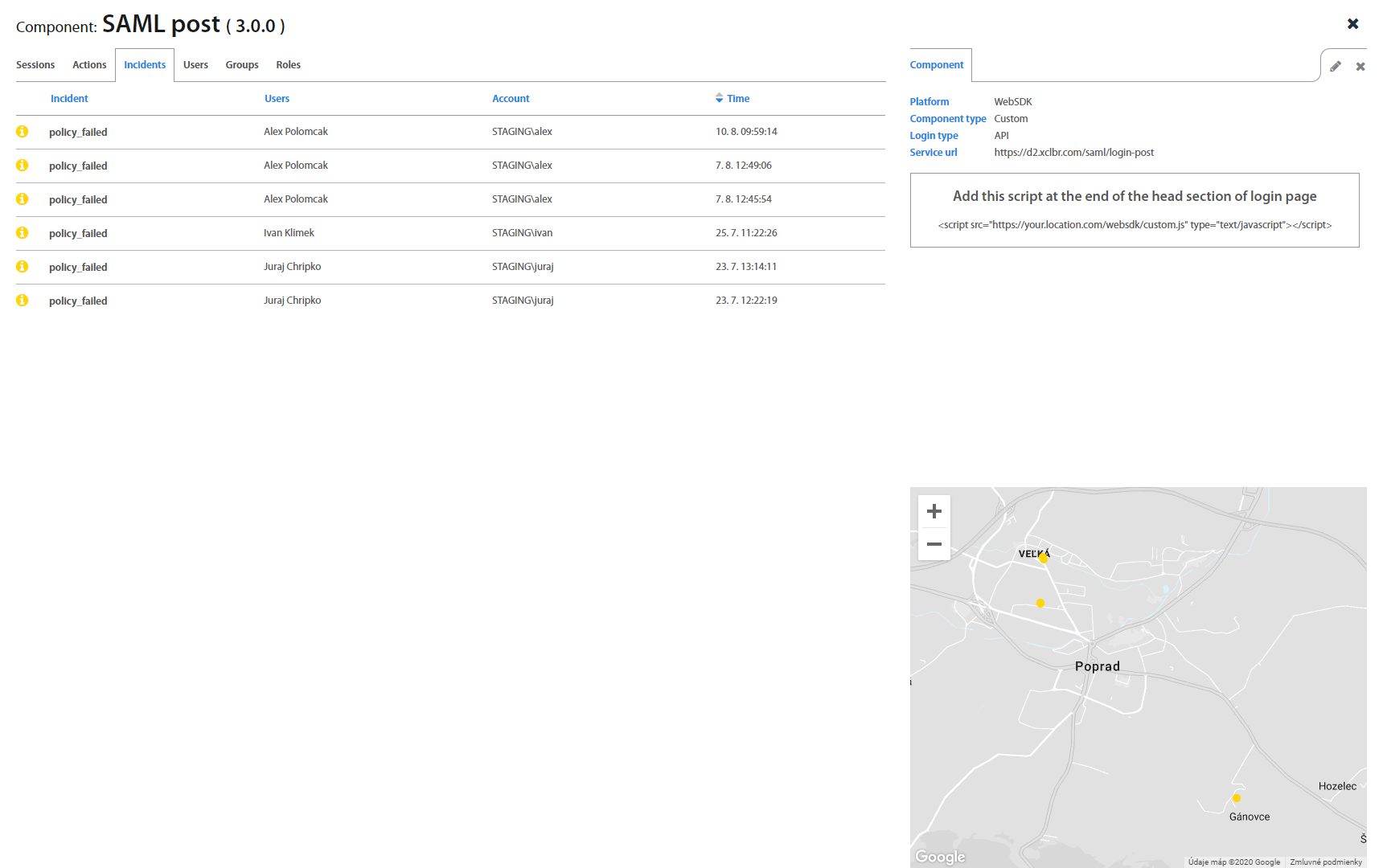
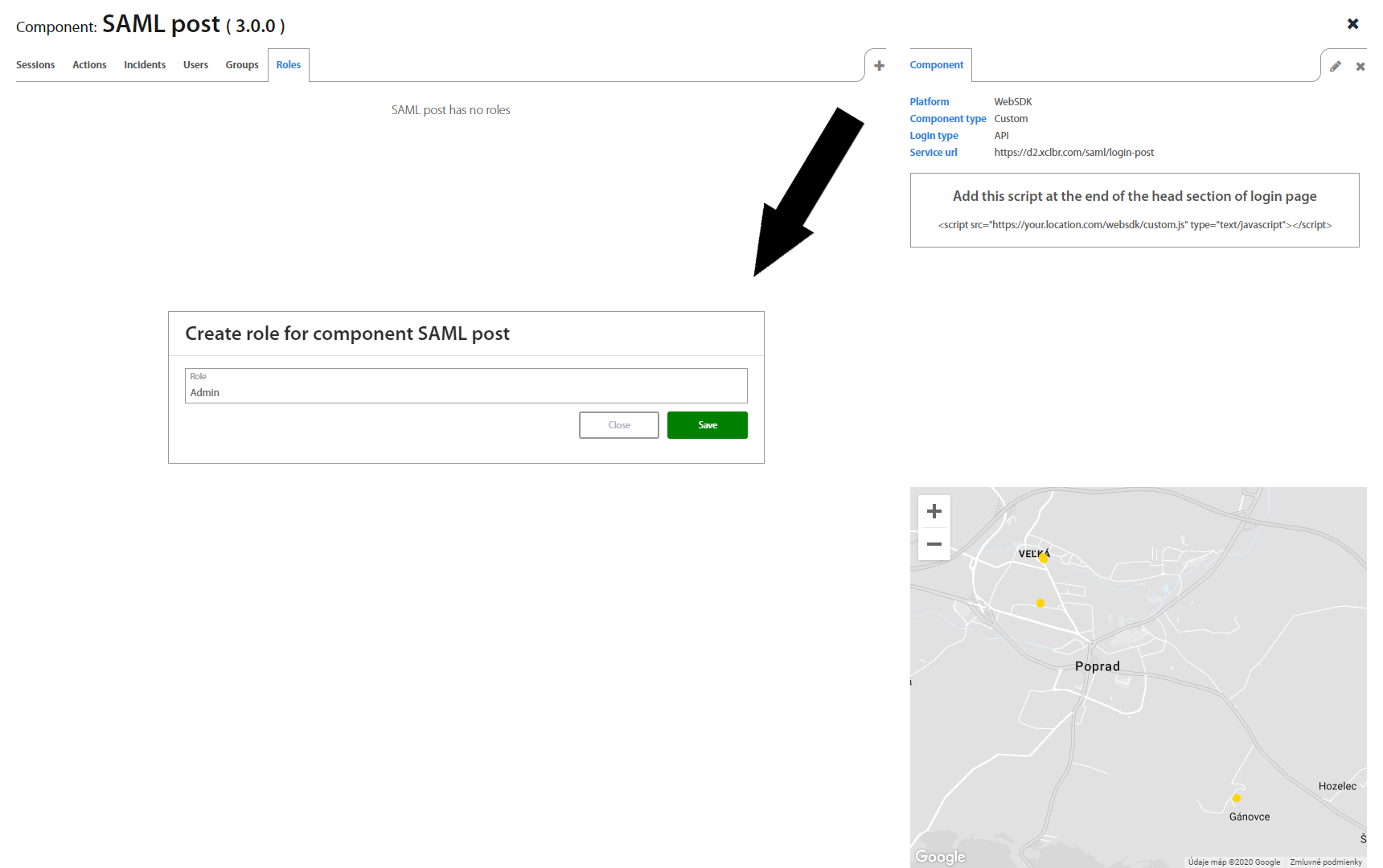
By clicking on specific component detail of component shows up. You can switch between Action, Sessions, Incidents, Users, Groups and Roles tab as well as create a Role and add group to role.
PAM¶
PAM - provides web-based access to Enterprise resources – either directly acting as a HTML5 to other protocols proxy server (RDP, SSH, Telnet, VNC or even Browser access) or via dynamic port-forwarding that enables native clients such as RDP to access resources on the internal network via port forwarding on Excalibur PAM.
Excalibur PAM considers all sessions “privileged” and by default recorded. Every action taken by the user is cryptographically signed to certify it was performed by the authenticated user. The effect of this is that there is continuous matching of every user action (as every user action and user PAM session is recorded and cryptographically signed) to strongly multi-factor authenticated identity. With no way to delegate access or claim it was some other user.
For detailed information about PAM please see Excalibur PAM Manual.
Resources¶
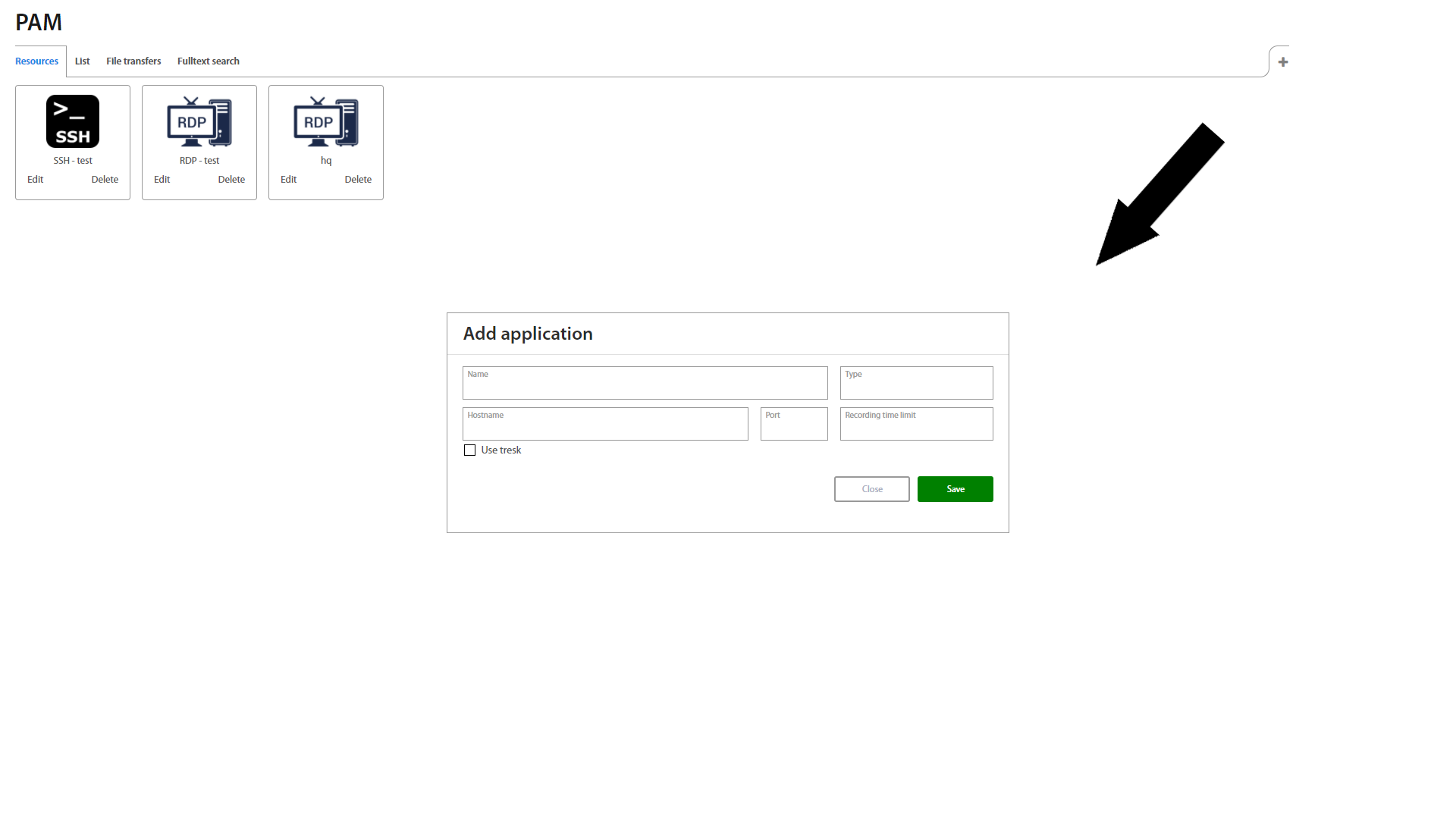
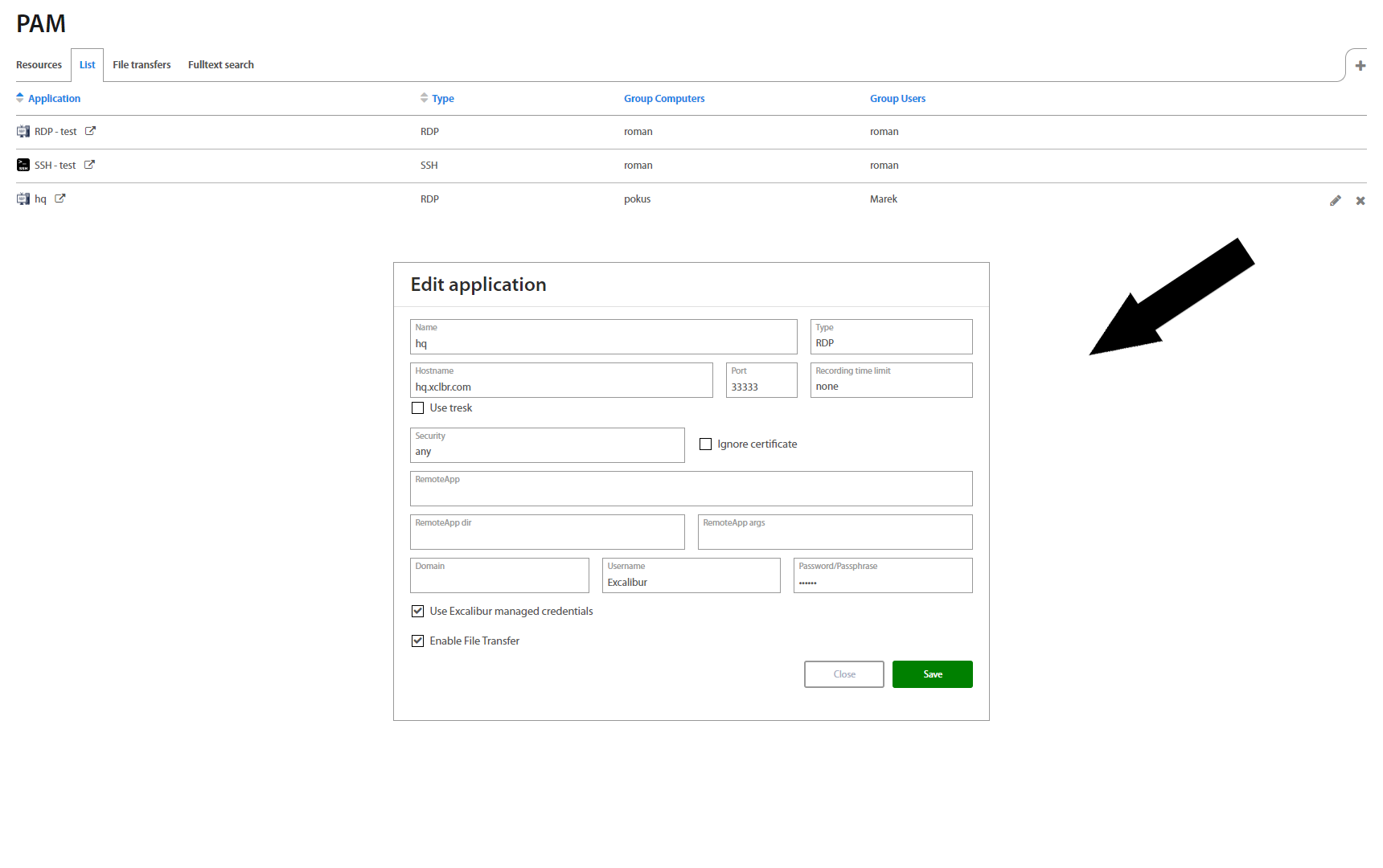
Resources tab - shows all Applications which are assigned to the user's account. By clicking on the desired icon, the selected connection will be opened in a new tab. It's also possible to add, edit or delete PAM resource.
By clicking on the + button on the top right corner, Administrator can create PAM resources. Fill and select all fields and save application
| Field | Description |
|---|---|
| Name | Name of application |
| Type | SSH/RDP/VNC |
| Hostname | IP or hostname |
| Port | Range 0 - 65535 |
| Recording time limit | Duration how long the session has to be stored |
| Tresk | Select Tresk if you wish to create secure tunnel |
For detailed information about PAM resources please see Excalibur PAM Manual. For detailed information about Tresk please see Excalibur Tresk Whitepaper
List¶
List tab - shows all assigned resources and their type. If user clicks on button, the connection will be established. By clicking on a specific application, further details will be shown (see section Application Details).
If is needed to edit resource, go with mouse cursor over the row and button shows up. Click on the button and create changes. If it is needed to delete a PAM resource, click on the x button. To create new PAM resource, click on the + button.
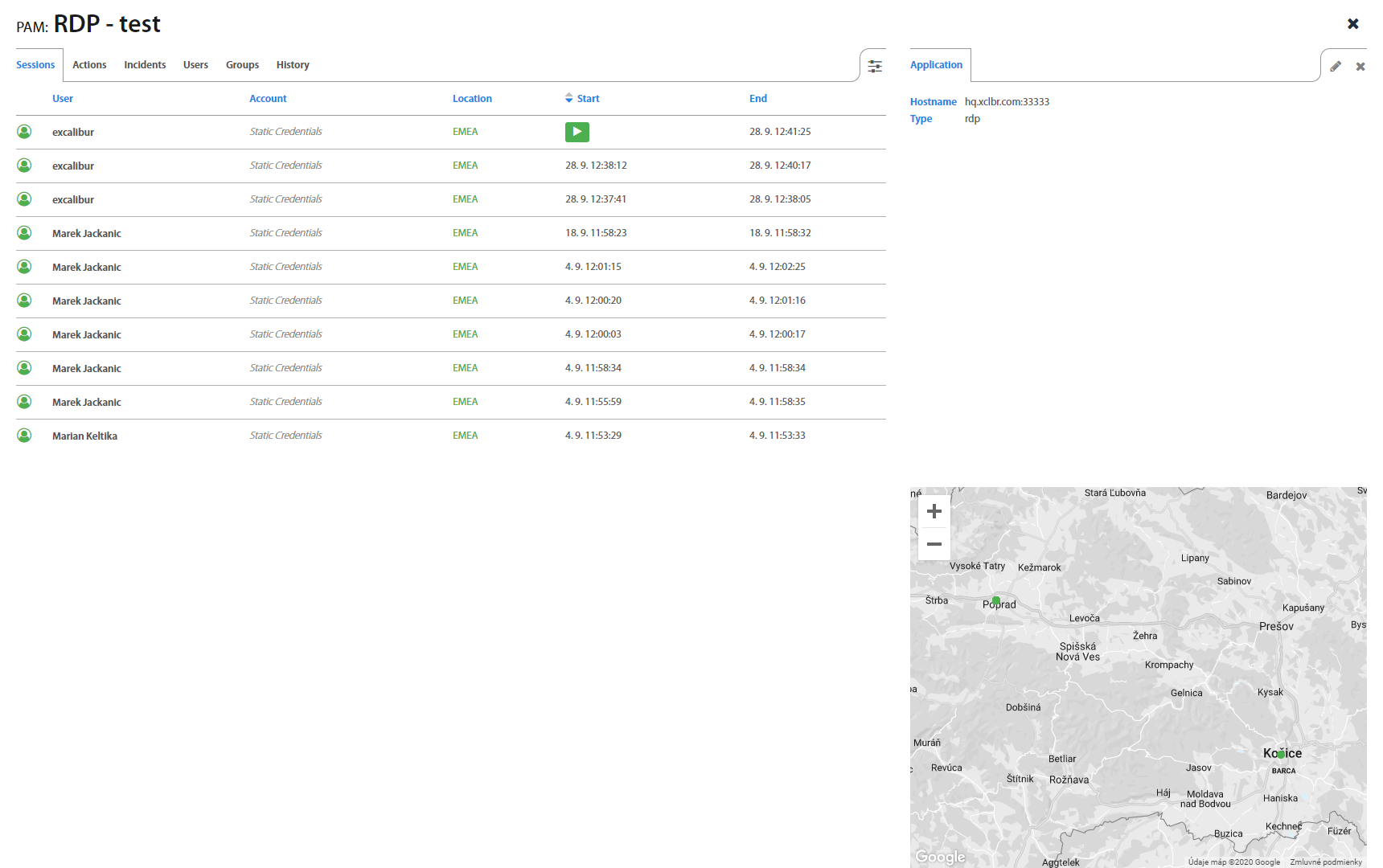
List: Sessions¶
Sessions tab lists all the past and active user sessions as well as their start / end time. All PAM sessions are by default recorded. By hovering over specified session, the button shows up. Click on to play the session. For SSH connections, it is also possible to download typescript and typescript timing information by clicking on the or  button. If another user has active PAM connection, administrator may see activity of this user by clicking on button.
button. If another user has active PAM connection, administrator may see activity of this user by clicking on button.
On the right hand are informations about connection of PAM application
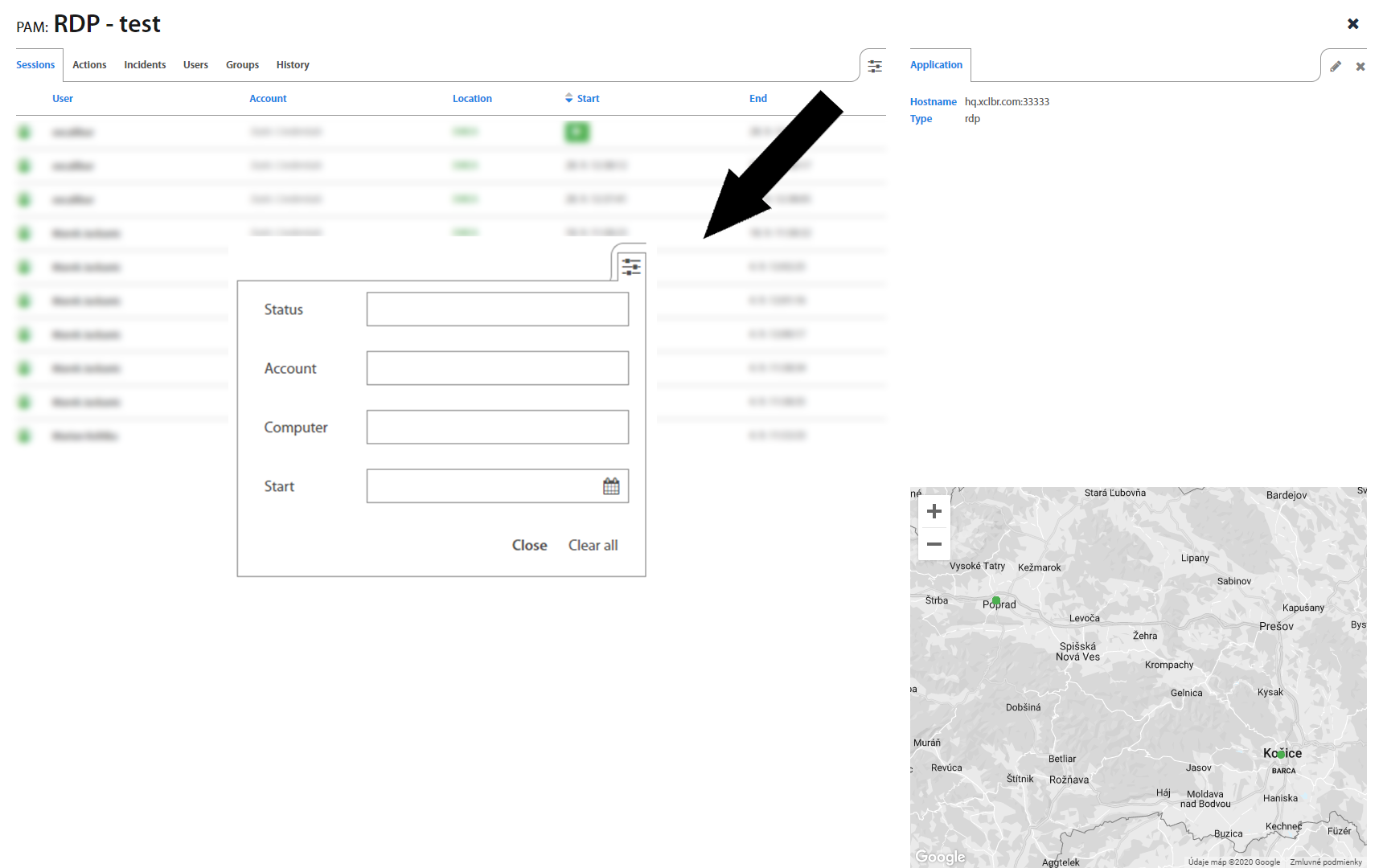
It’s also possible to filter Sessions by Account, Computer, Status or Start time in the top right corner.
List: Actions & Incidents¶
Actions tab lists all actions if the PAM resource requires some actions. By clicking on the action, the action details show up.
Incidents tab lists all incidents which occurred during opening the PAM application. By clicking on the incident, the incident details show up.
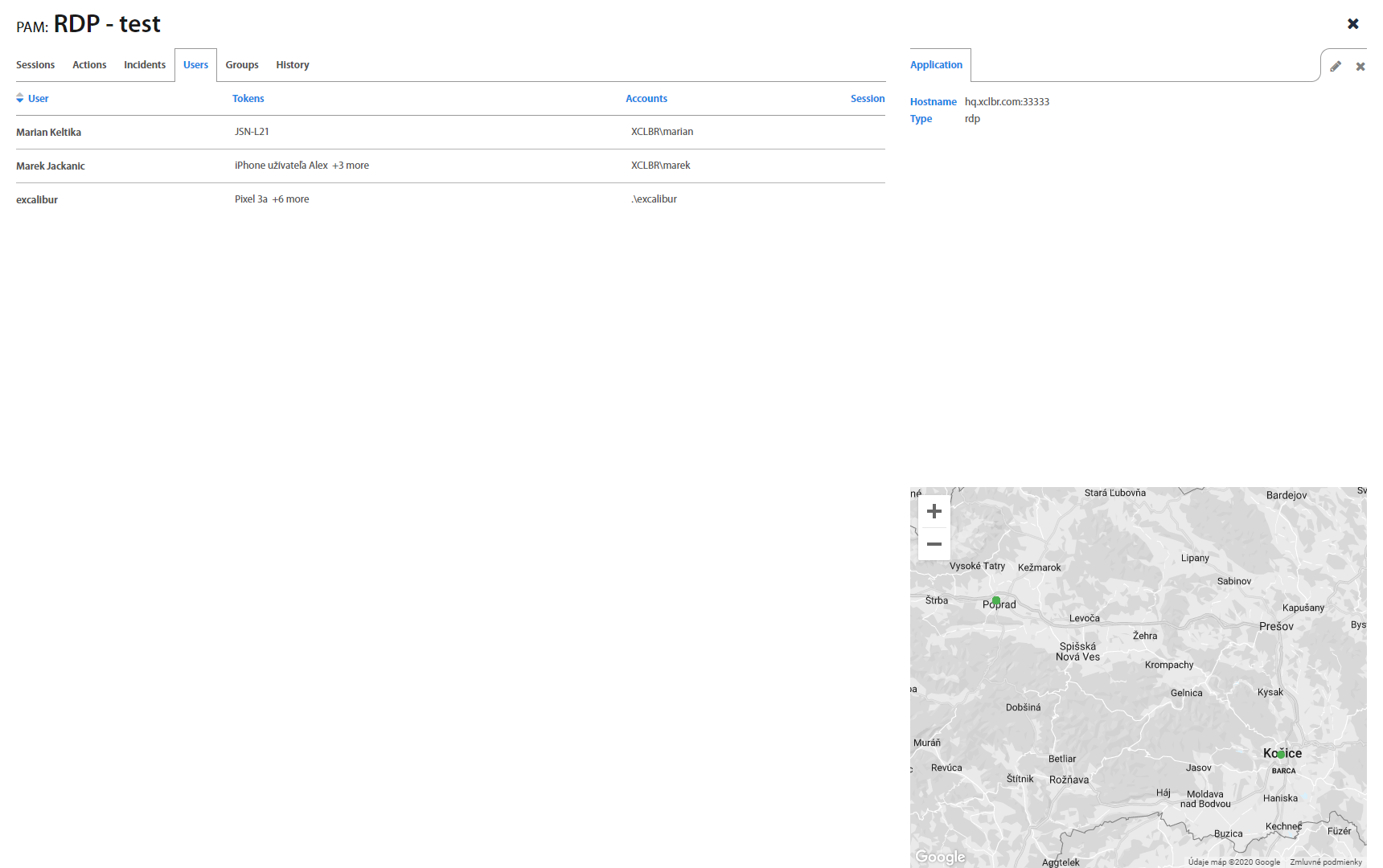
List: Users¶
Users tab lists all user's details who use the PAM application. By clicking on the user, the user's details show up. By clicking on the token, the token's details show up. By clicking on the account, the account's details show up. If the PAM session is active, then the session column shows the duration of session.
List: Groups¶
Group tab lists groups where the PAM resource is assigned. By clicking on the group, the group details show up.
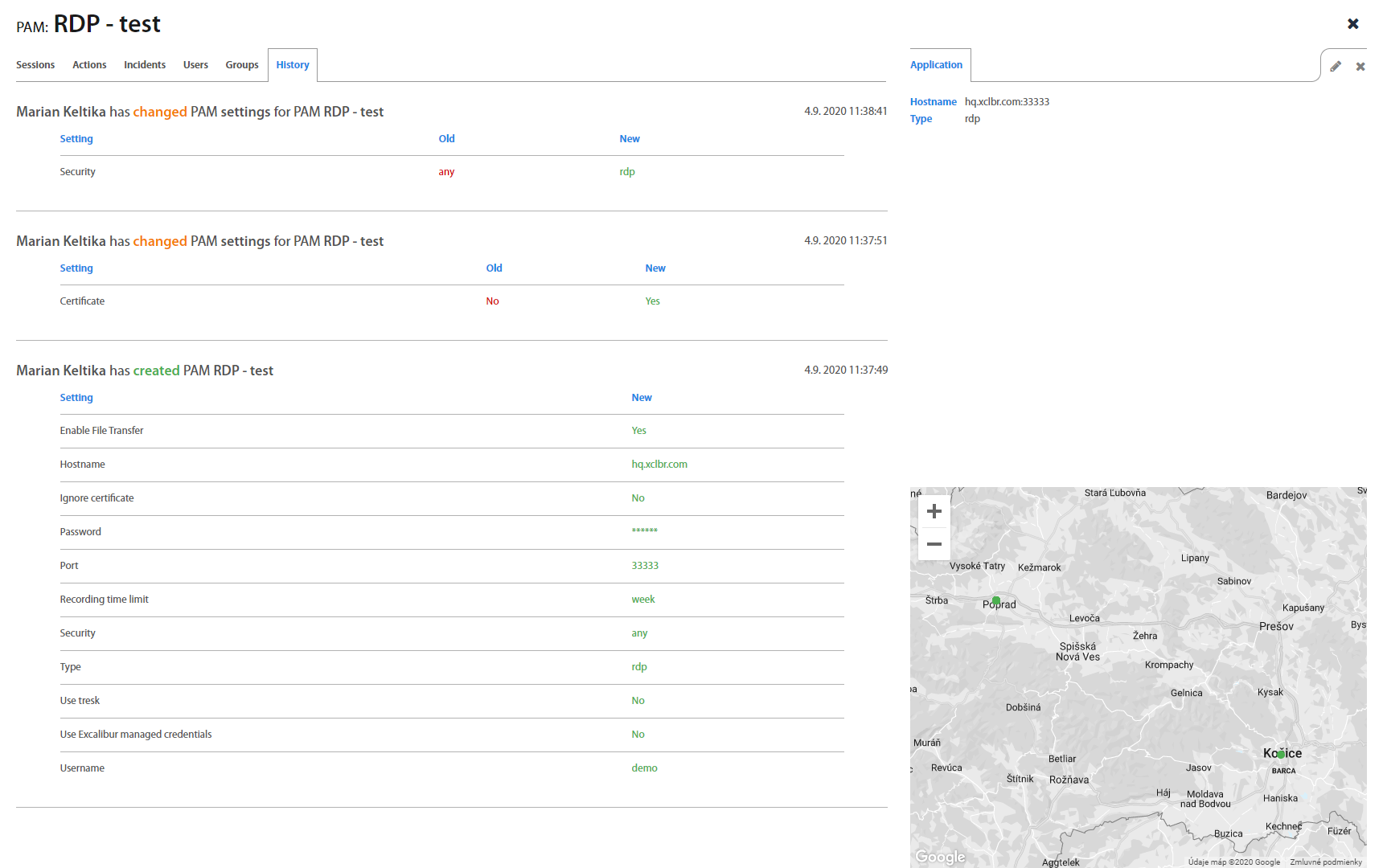
List: History¶
History tab shows all changes of PAM application which were performed
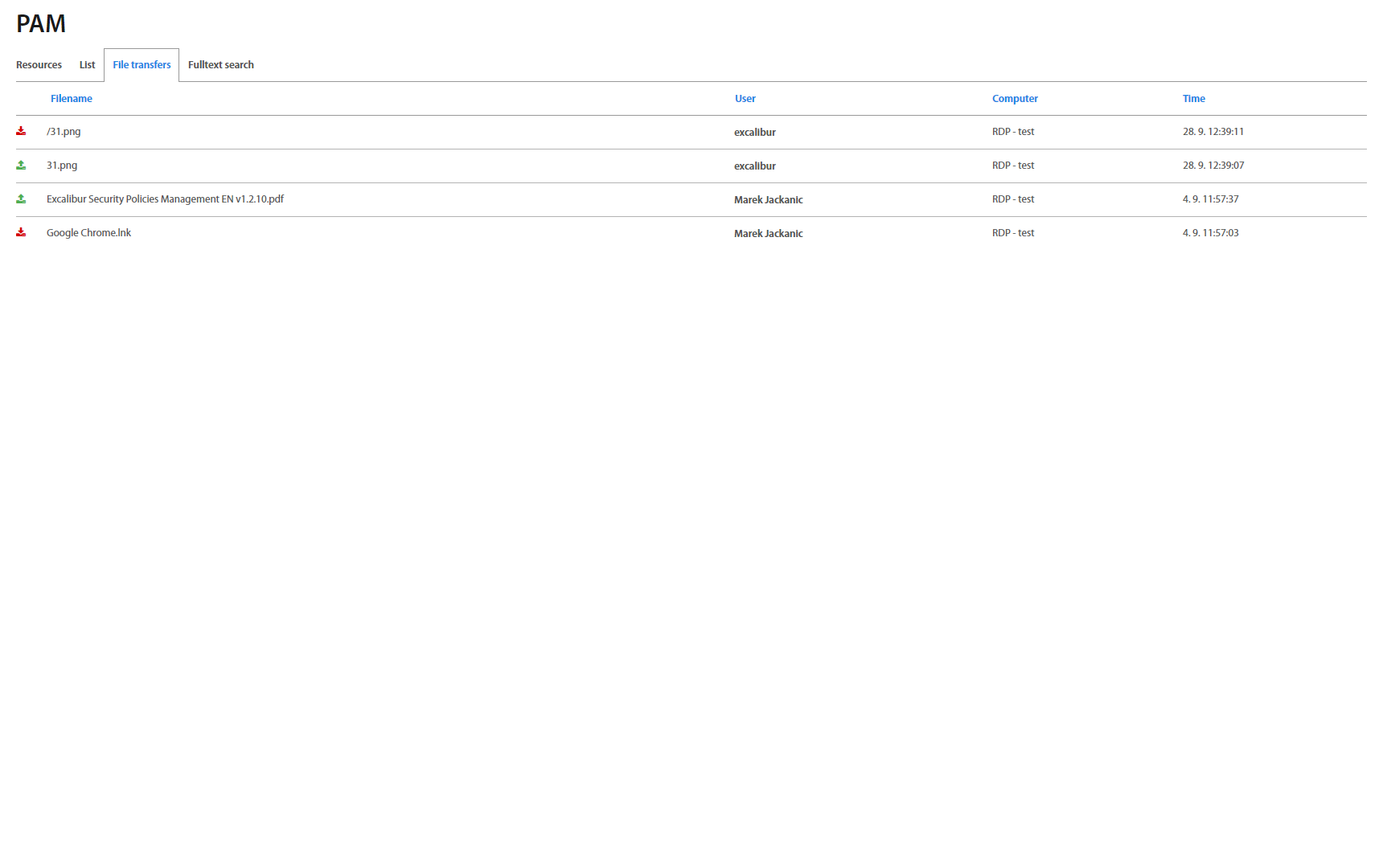
File transfers¶
Excalibur PAM displays all files which are transferred by users in PAM sessions. Each role has presetted rules to show transferred files. Administrators, Service desks and Auditors see all files which were transferred, managers have access to their own and subordinate’s files. Users have access to their own files only. By clicking on the specific file or / button, file is downloaded immediately. By clicking on the user name or client, further information are shown.
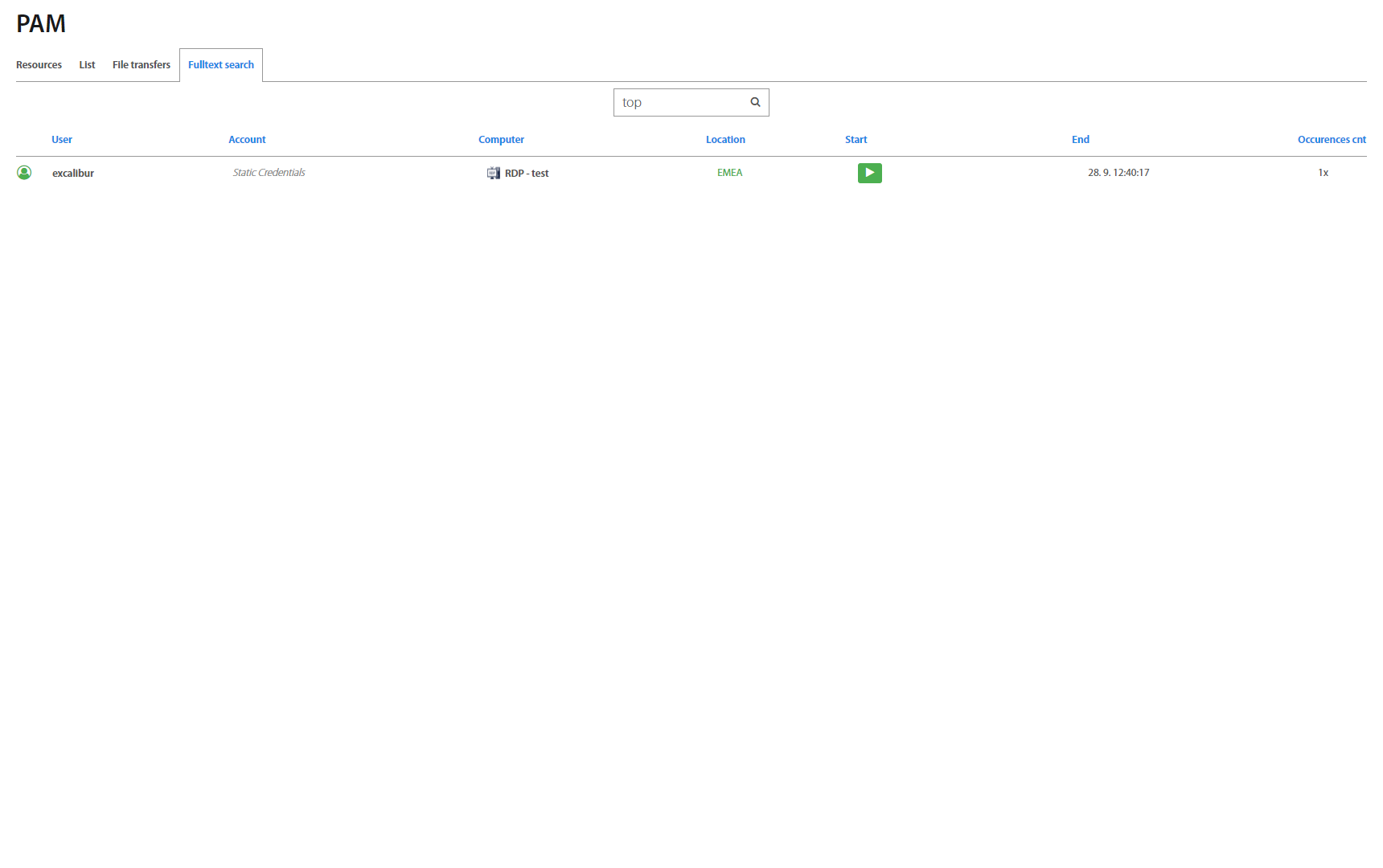
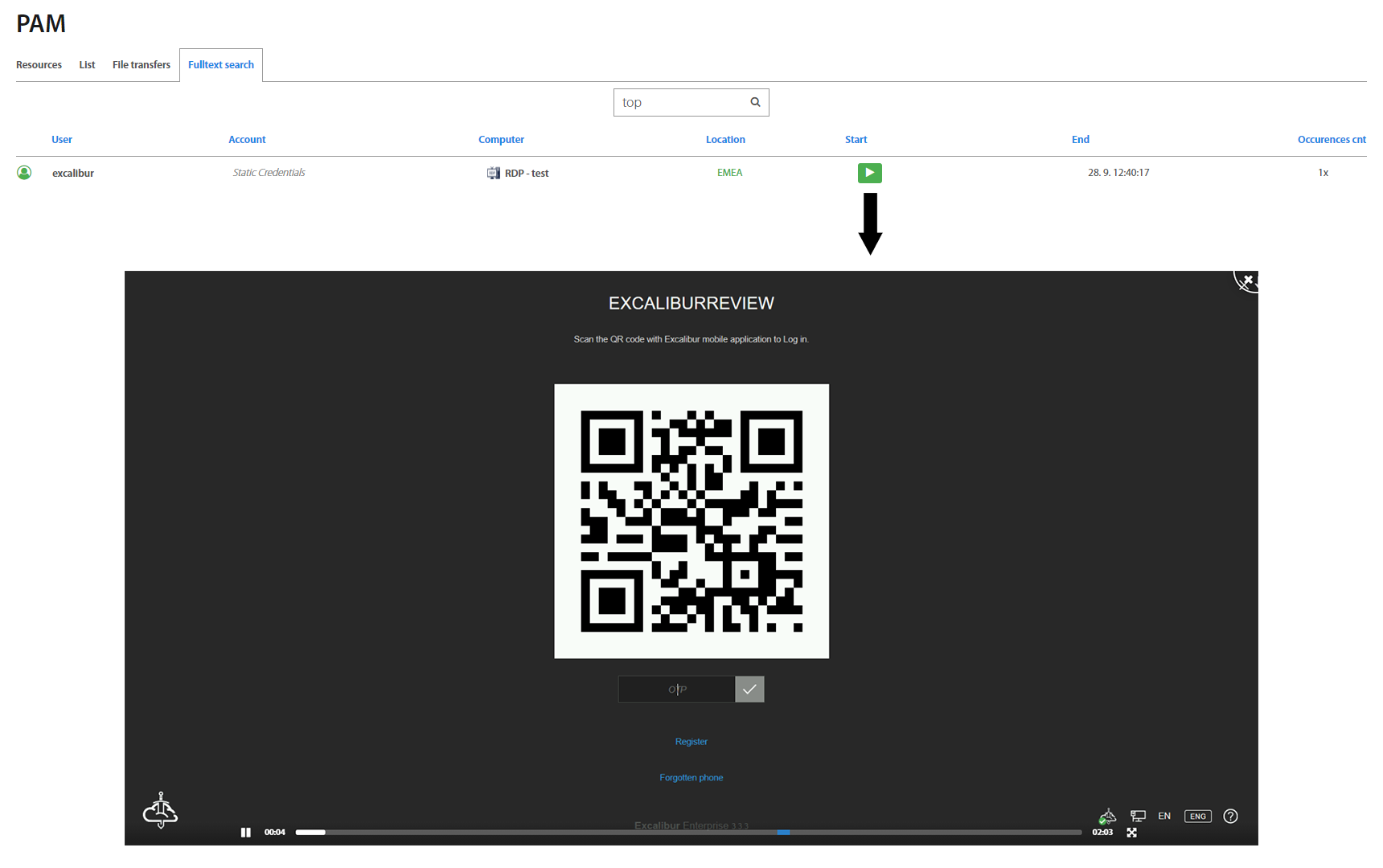
Fulltext search¶
Excalibur PAM allows you to find a full word which is inserted by the user during the PAM session. Each role has presetted rules of searching. Administrators, Service desks and Auditors can search words in all PAM sessions, managers can search in their own and subordinate’s PAM sessions. Users can search in their own sessions only.
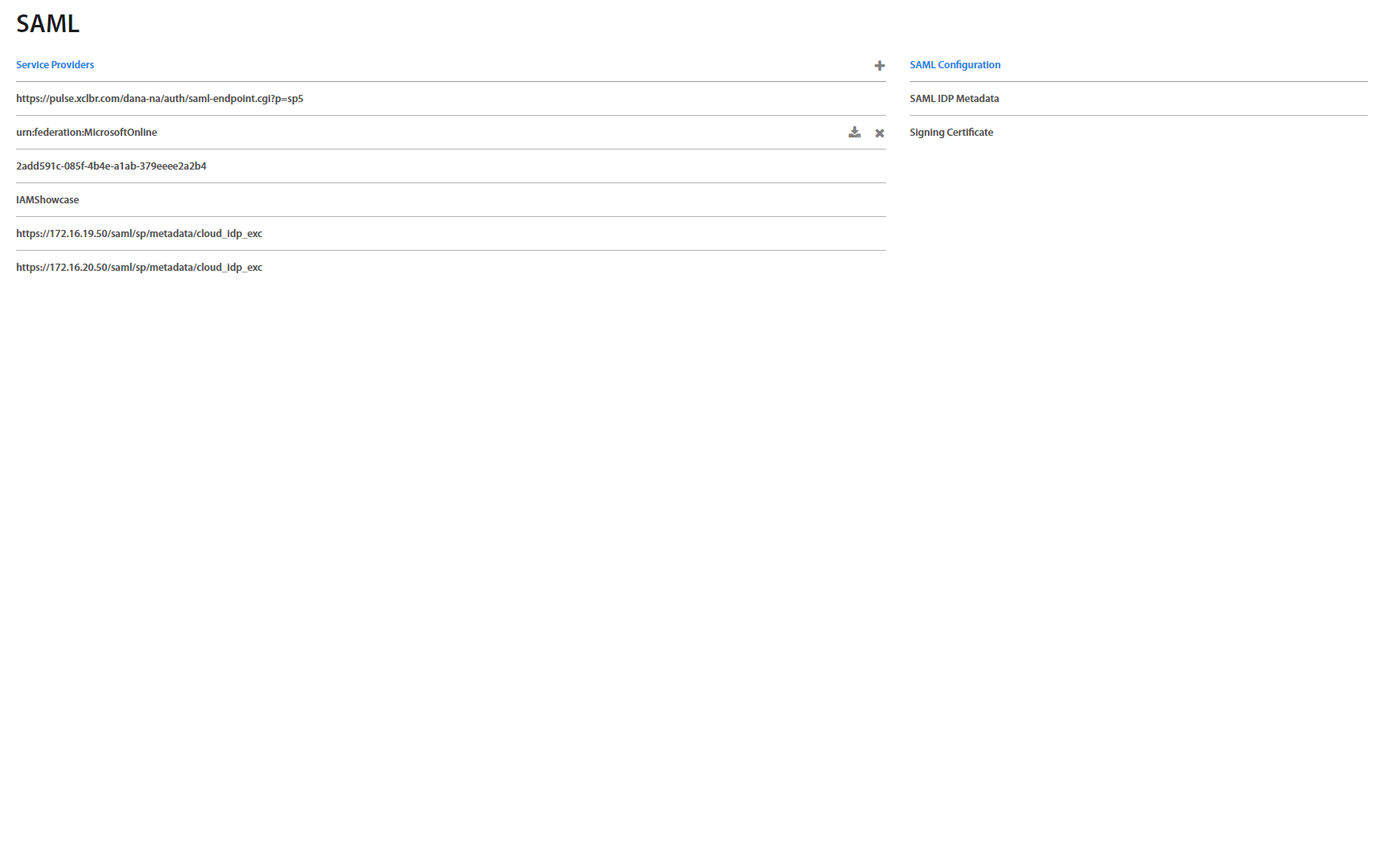
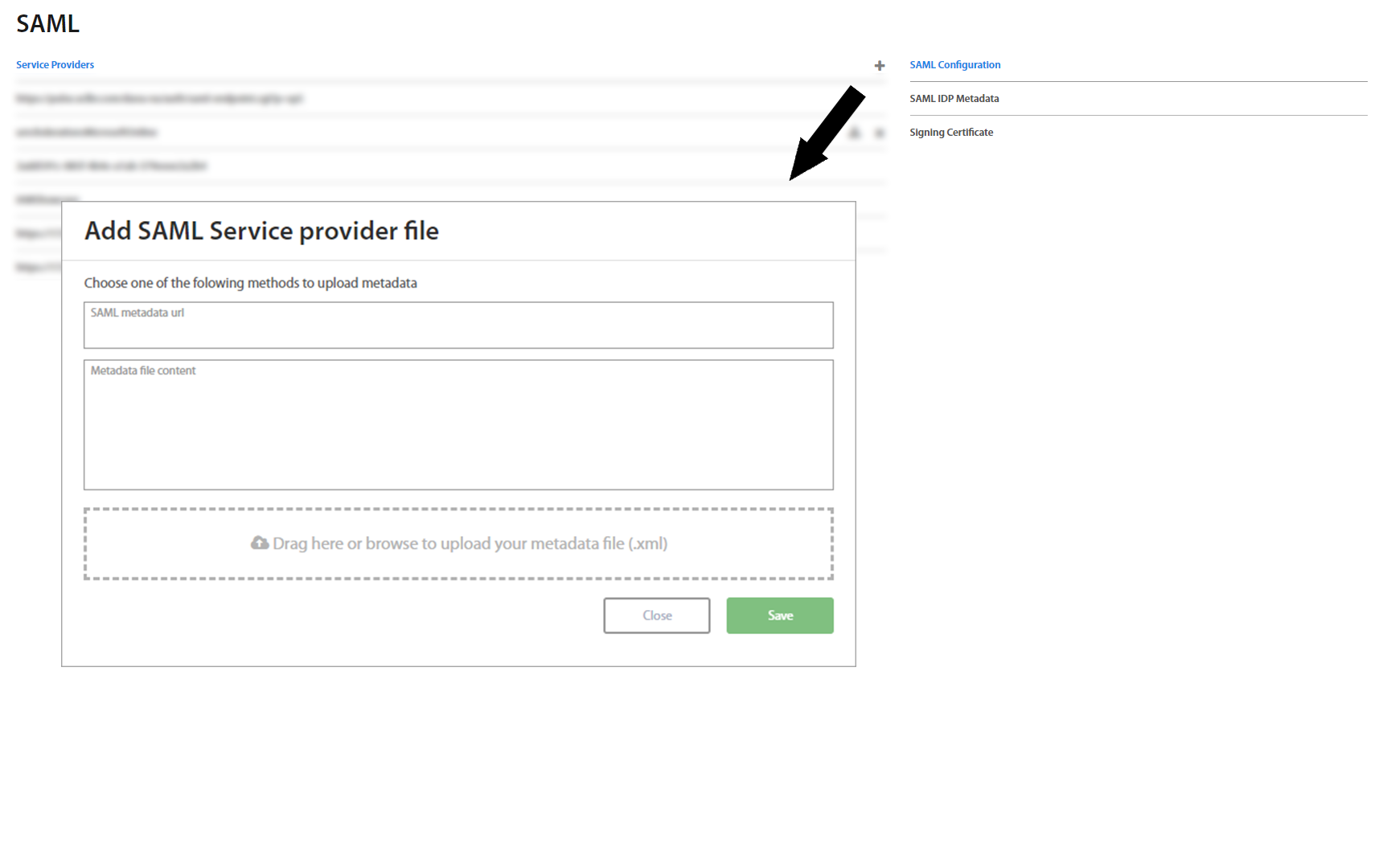
SAML Service Providers¶
SAML Service Provider page allows to upload and manage SAML certificates. Hovering over a specific row, the buttons show up. By clicking on the + button you can upload the SAML file. By clicking on the x button you can delete the SAML file. By clicking on the button the SAML file is downloaded immediately. On the right side is SAML Configuration. By clicking on the button the SAML configuration file is downloaded immediately.
Groups¶
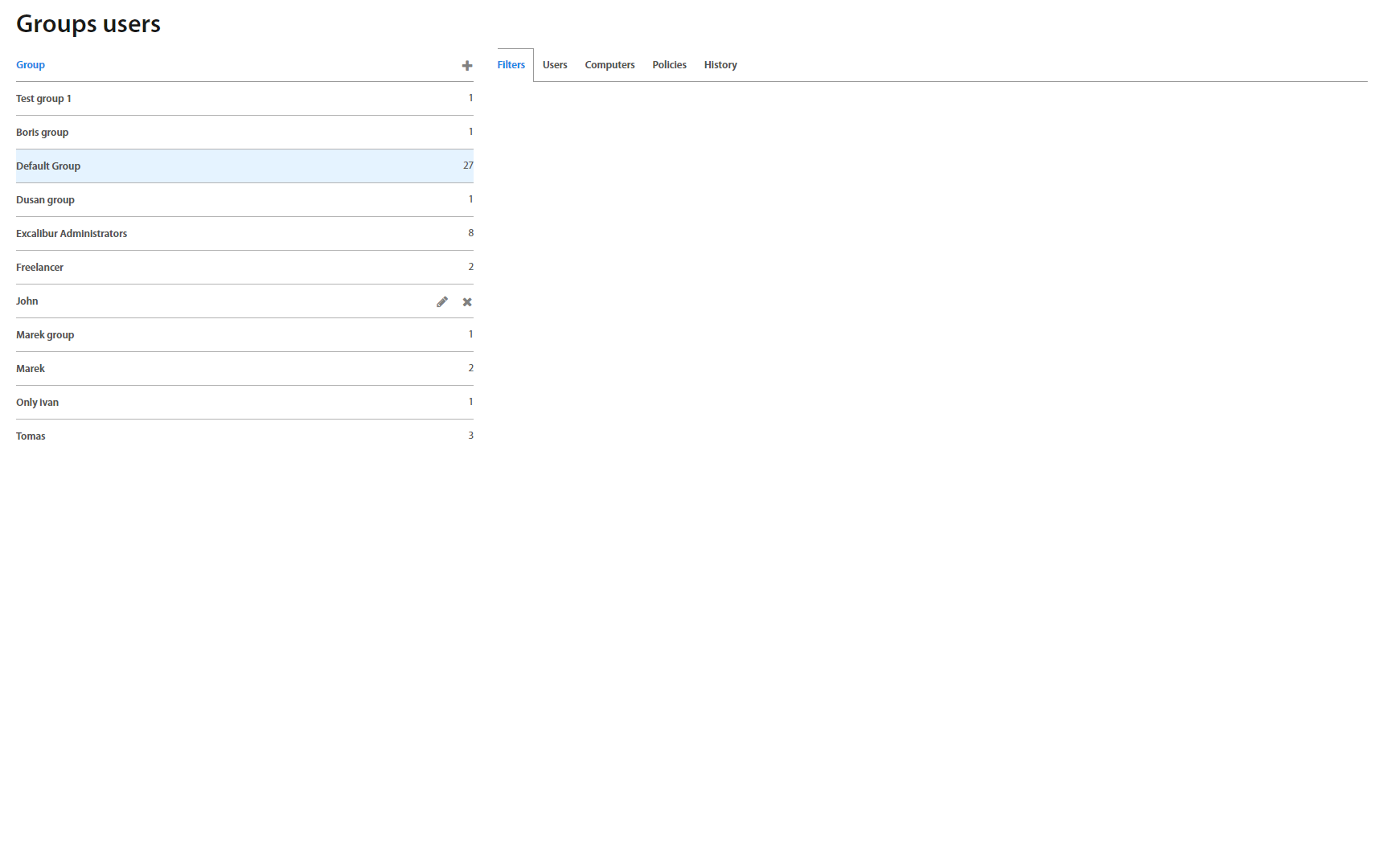
Groups: Users¶
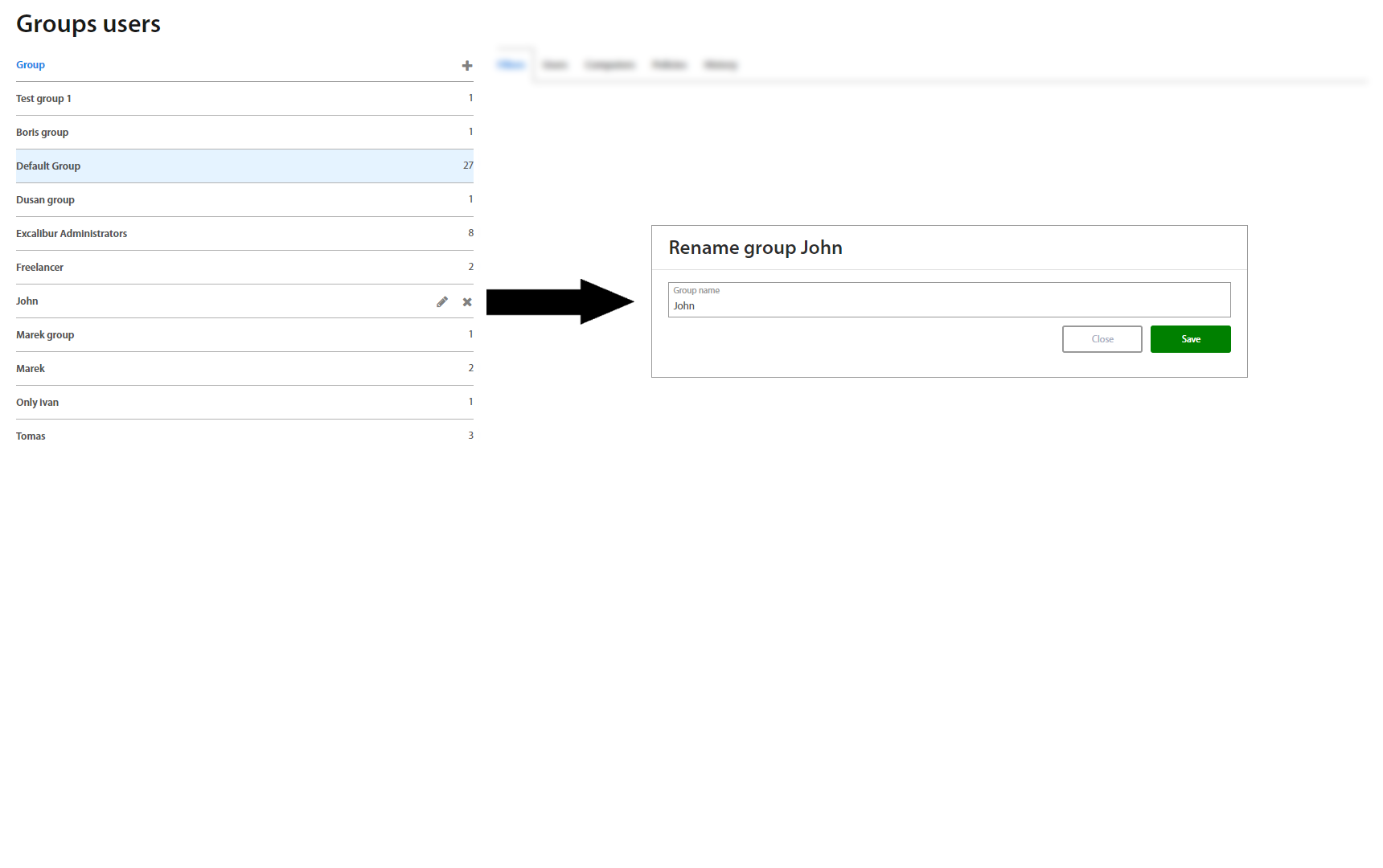
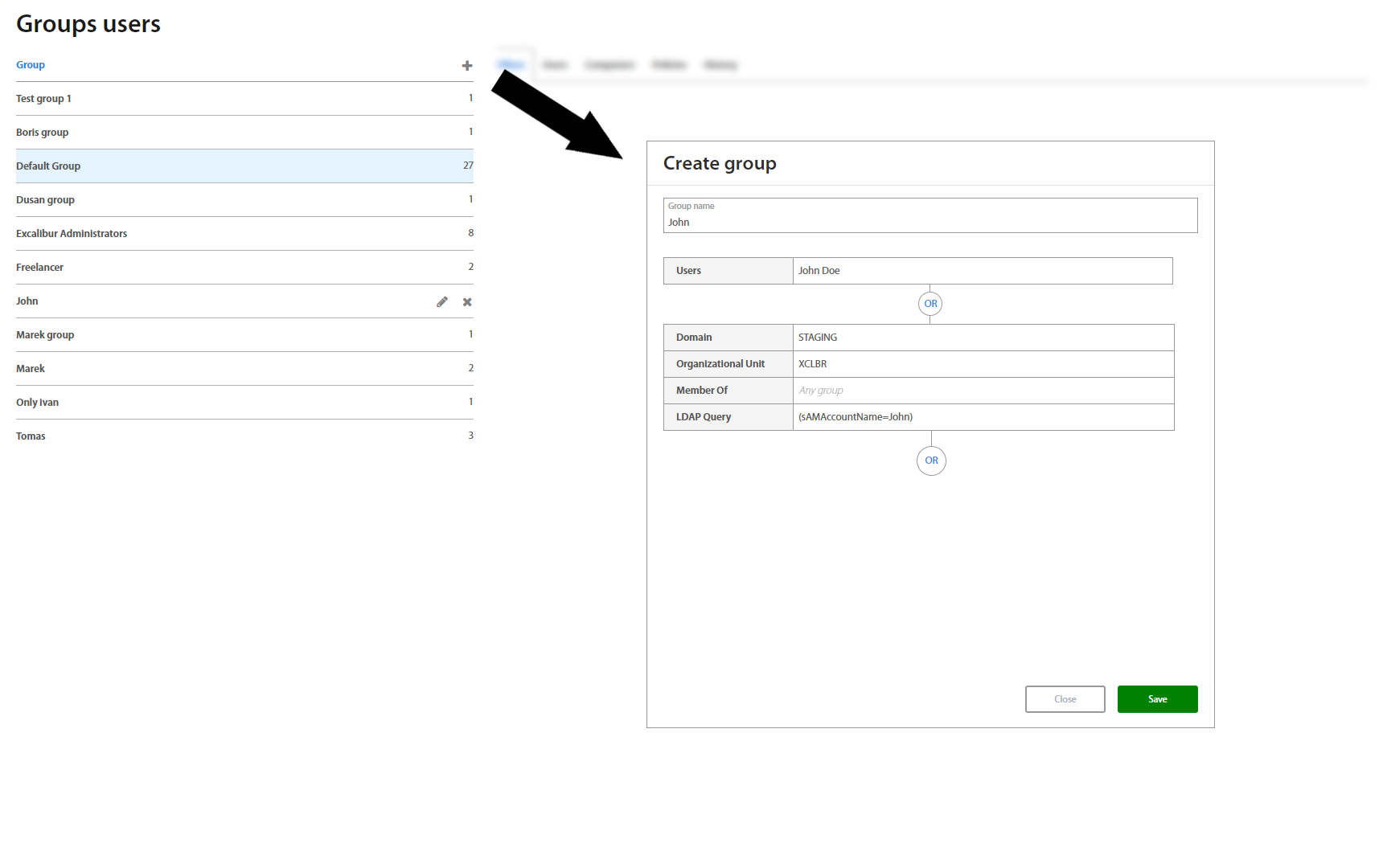
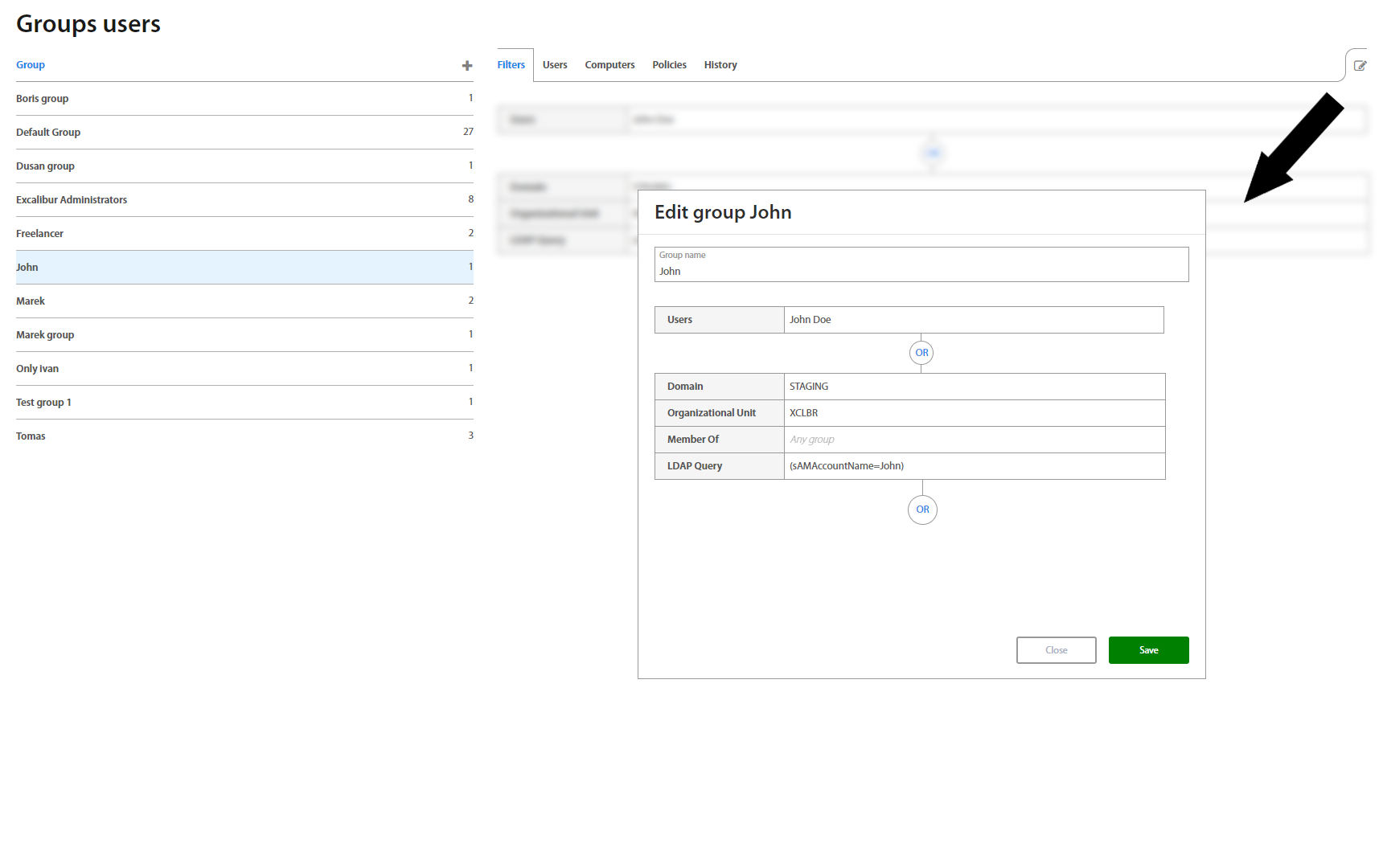
This page lists all Groups of Users created in Excalibur. To add a new group, click on the “+” plus button on top of the Groups list. To edit an existing group, click on an individual group name in the list and in the top right corner of the Group details, click on the edit button. By default, every registered user is assigned to the Default group which is predefined and is impossible to change it.
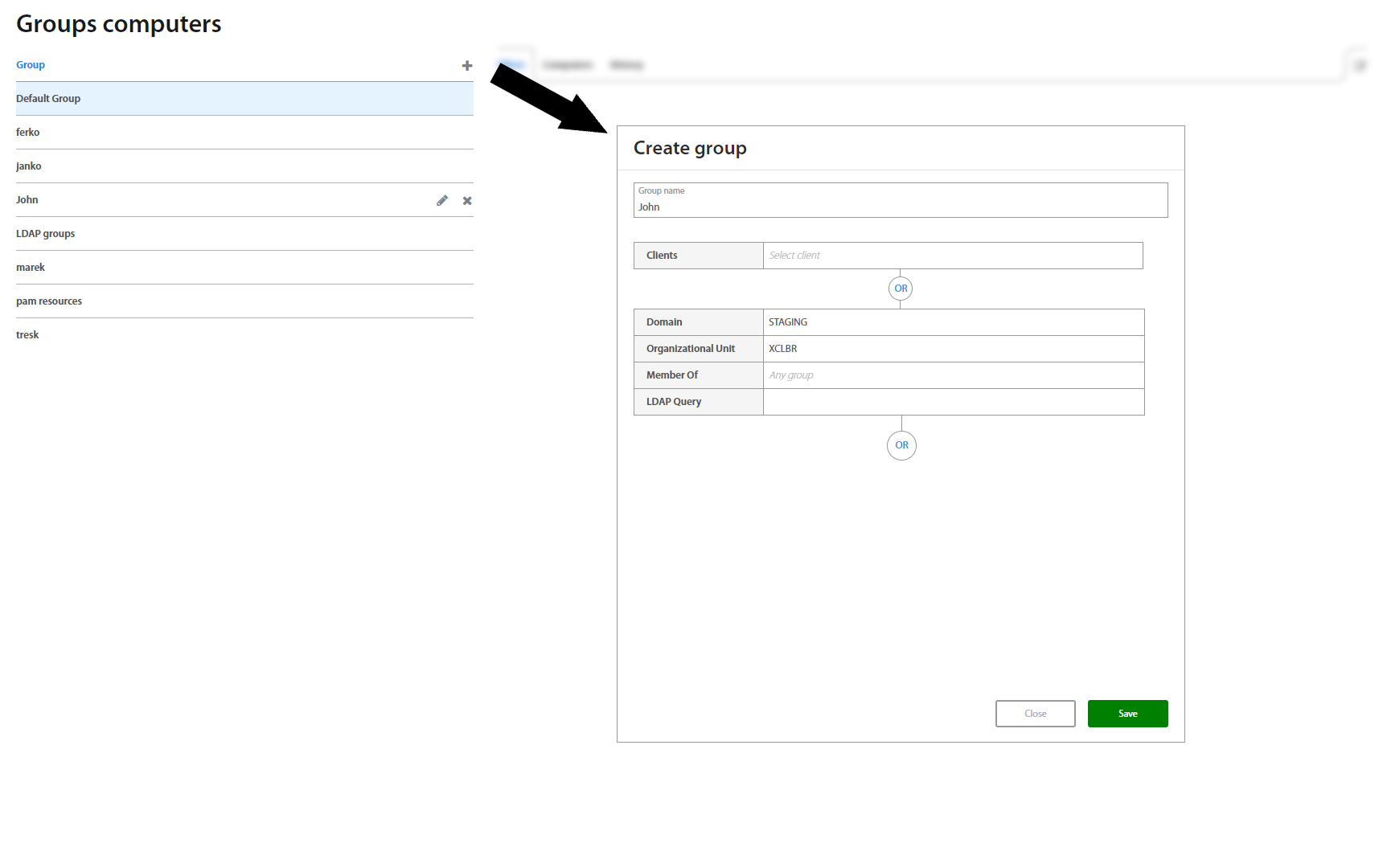
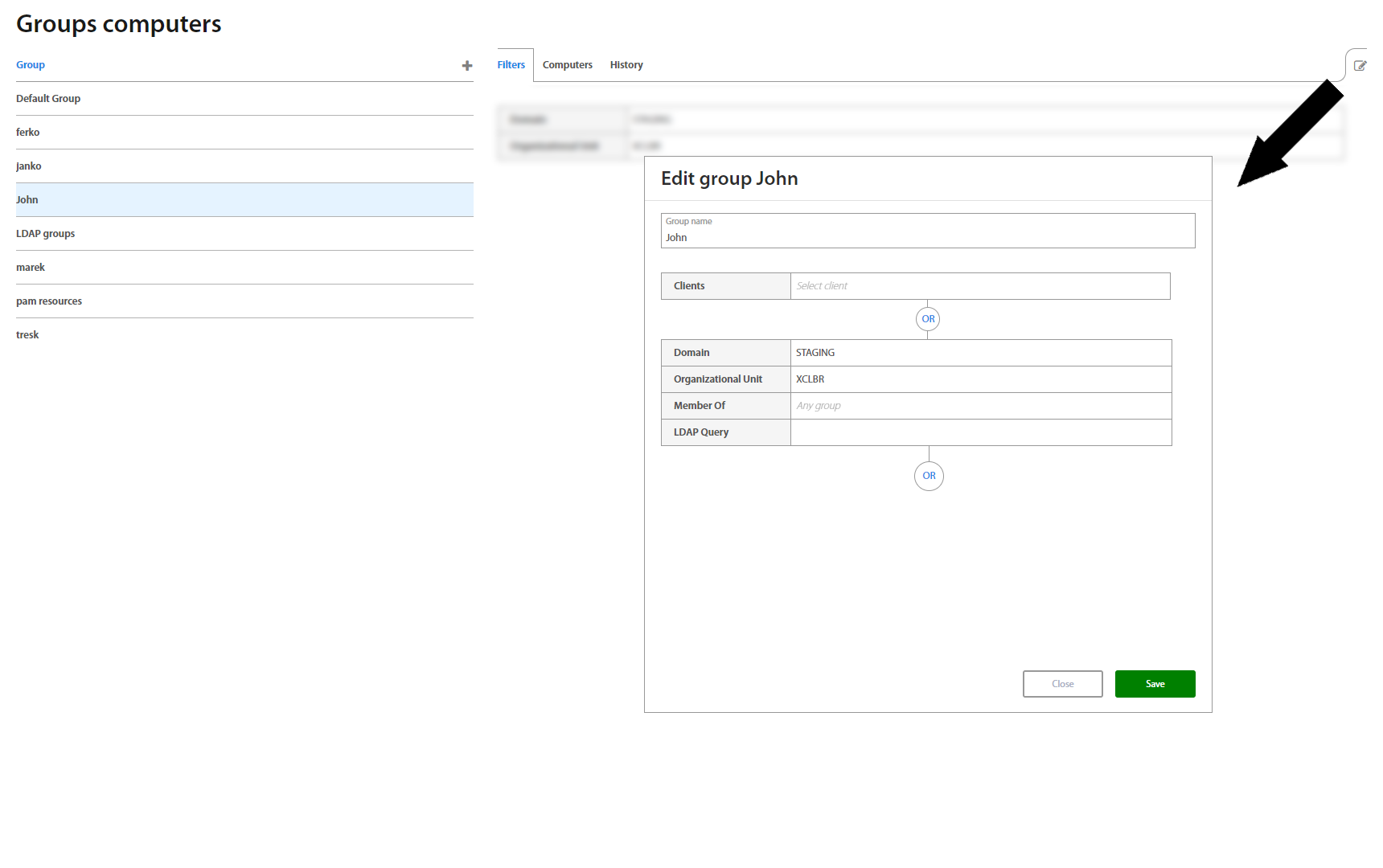
Creating a new group requires a new group name and at least one associated Organizational Unit, Group membership and (optionally) / or just an LDAP Query. To assign / combine multiple of them, use the “OR” button.
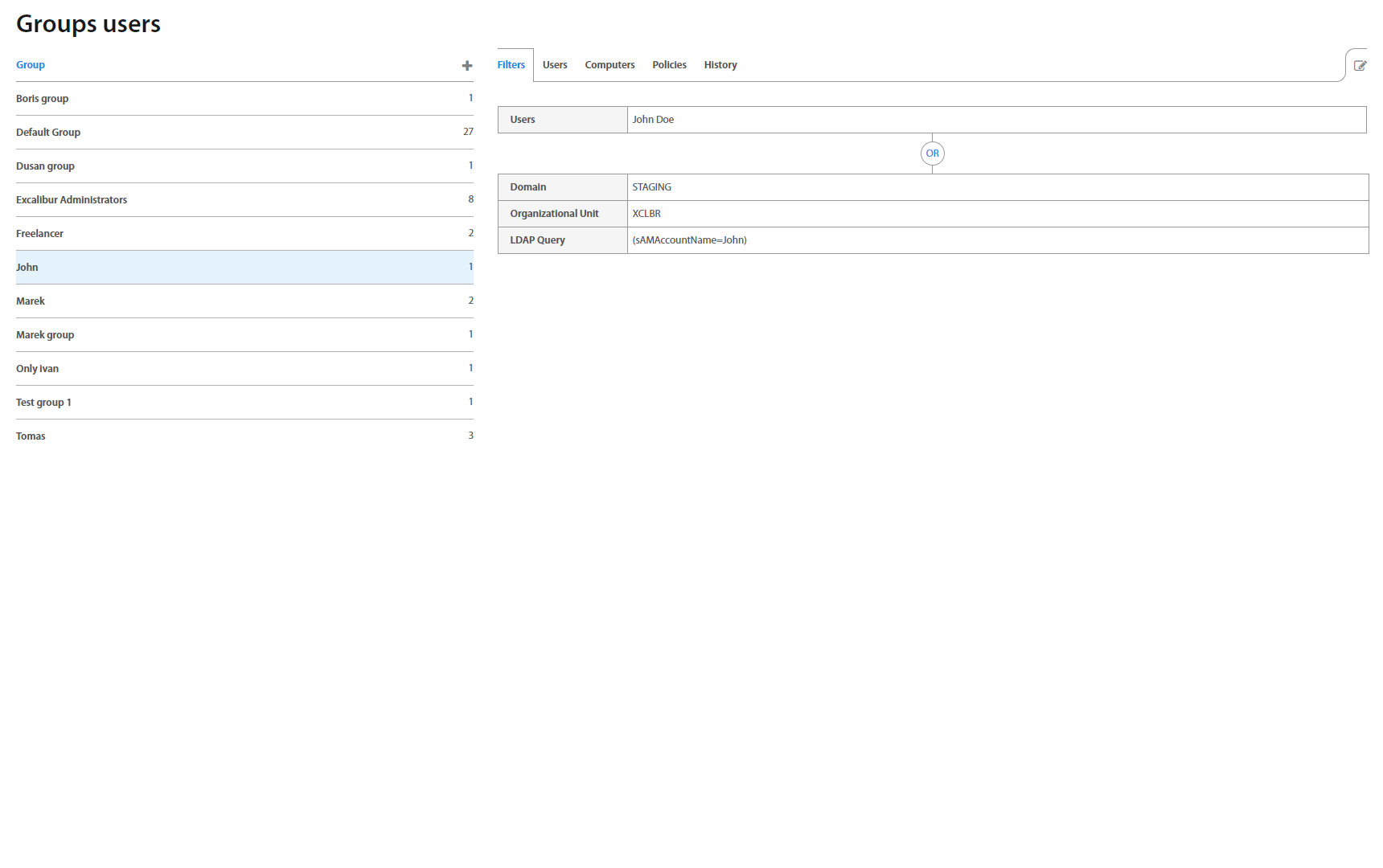
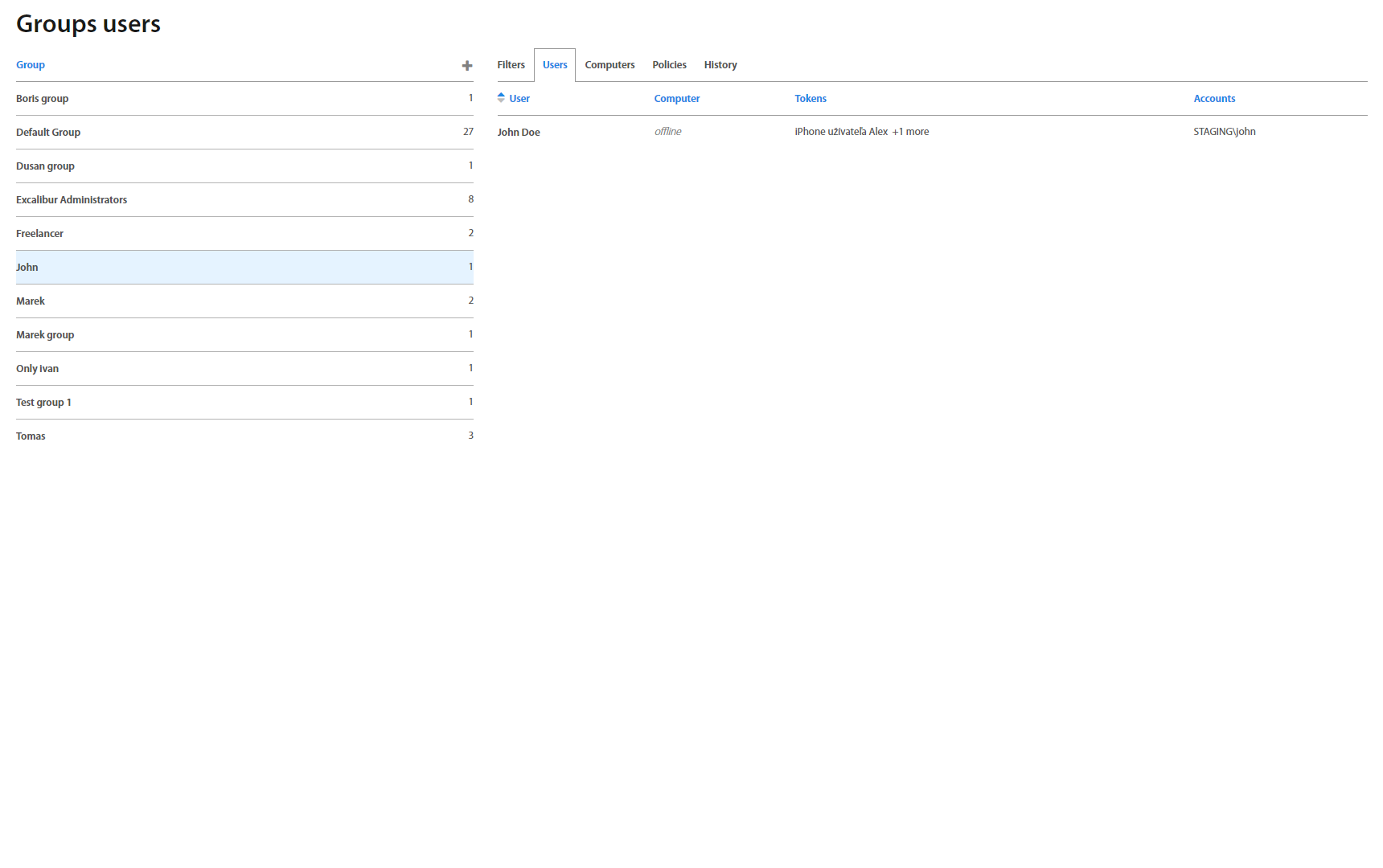
Group Detail also includes a view with all Users assigned to the group under the Users tab. By default, every registered user is assigned to the Default group. Clicking on the username shows the User account detail page.
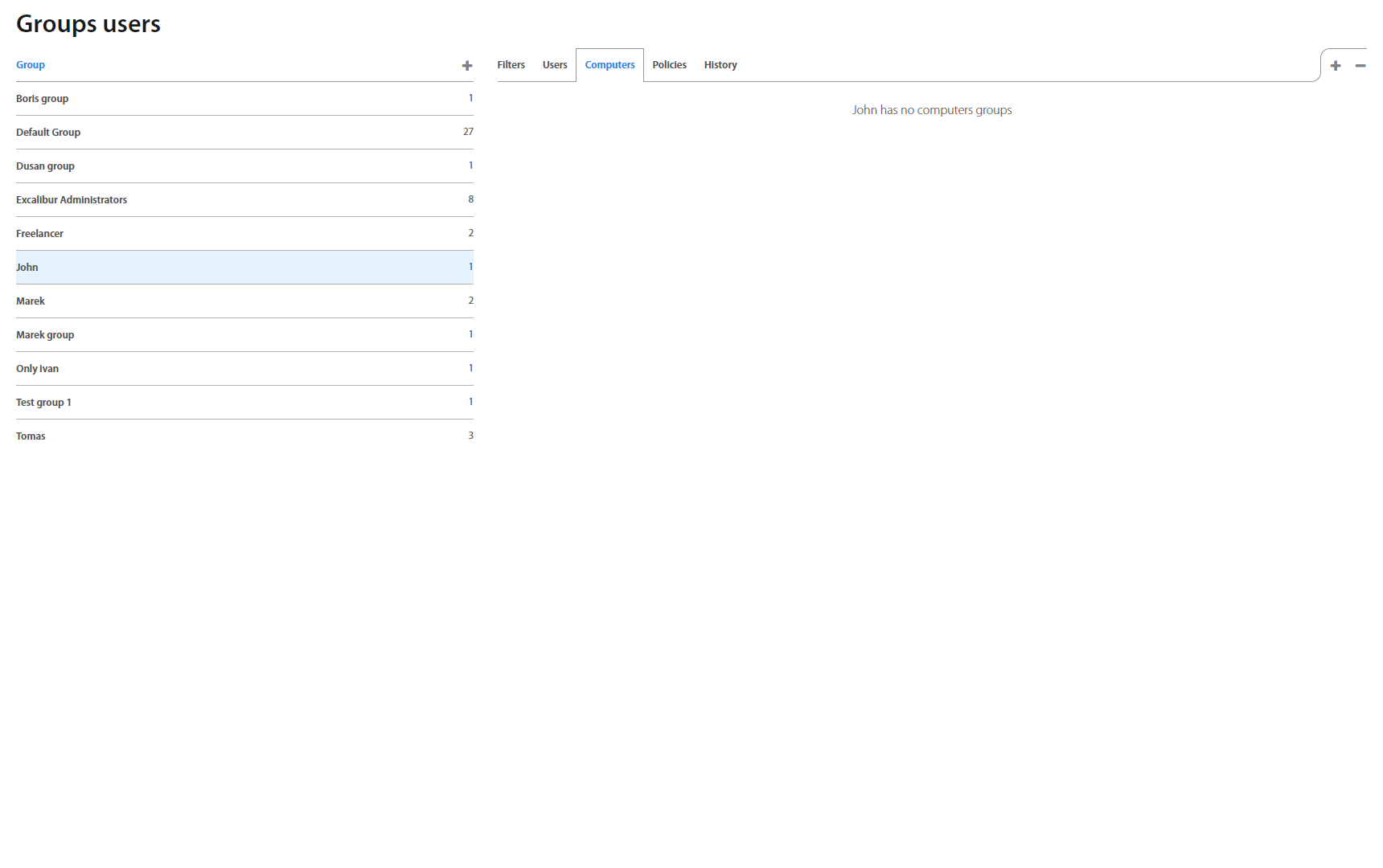
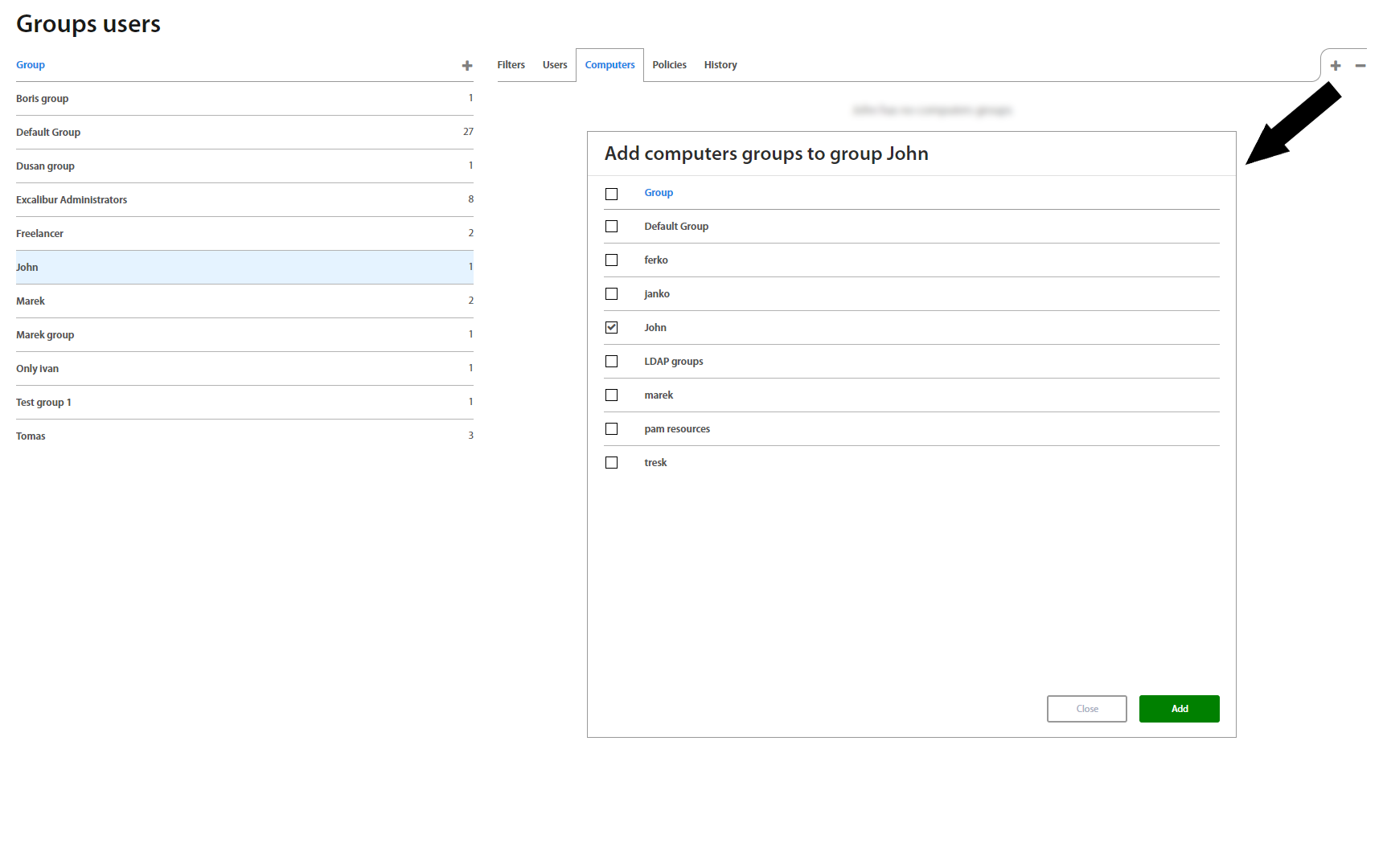
Group Detail also includes a view with all Computer groups assigned to the group under the Computers tab. Click on the "+" or "-" button do Add/remove Computer group from the User group.
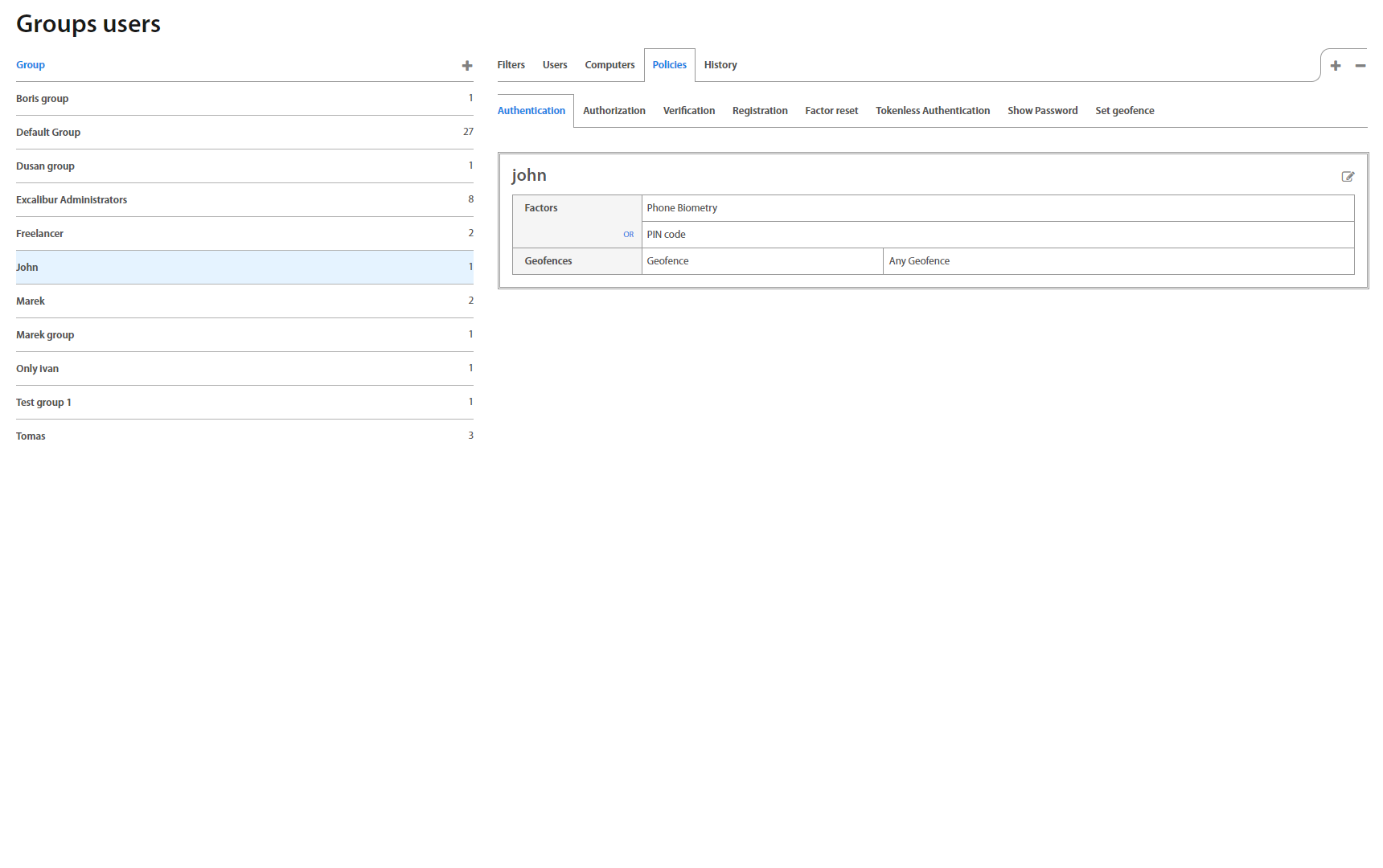
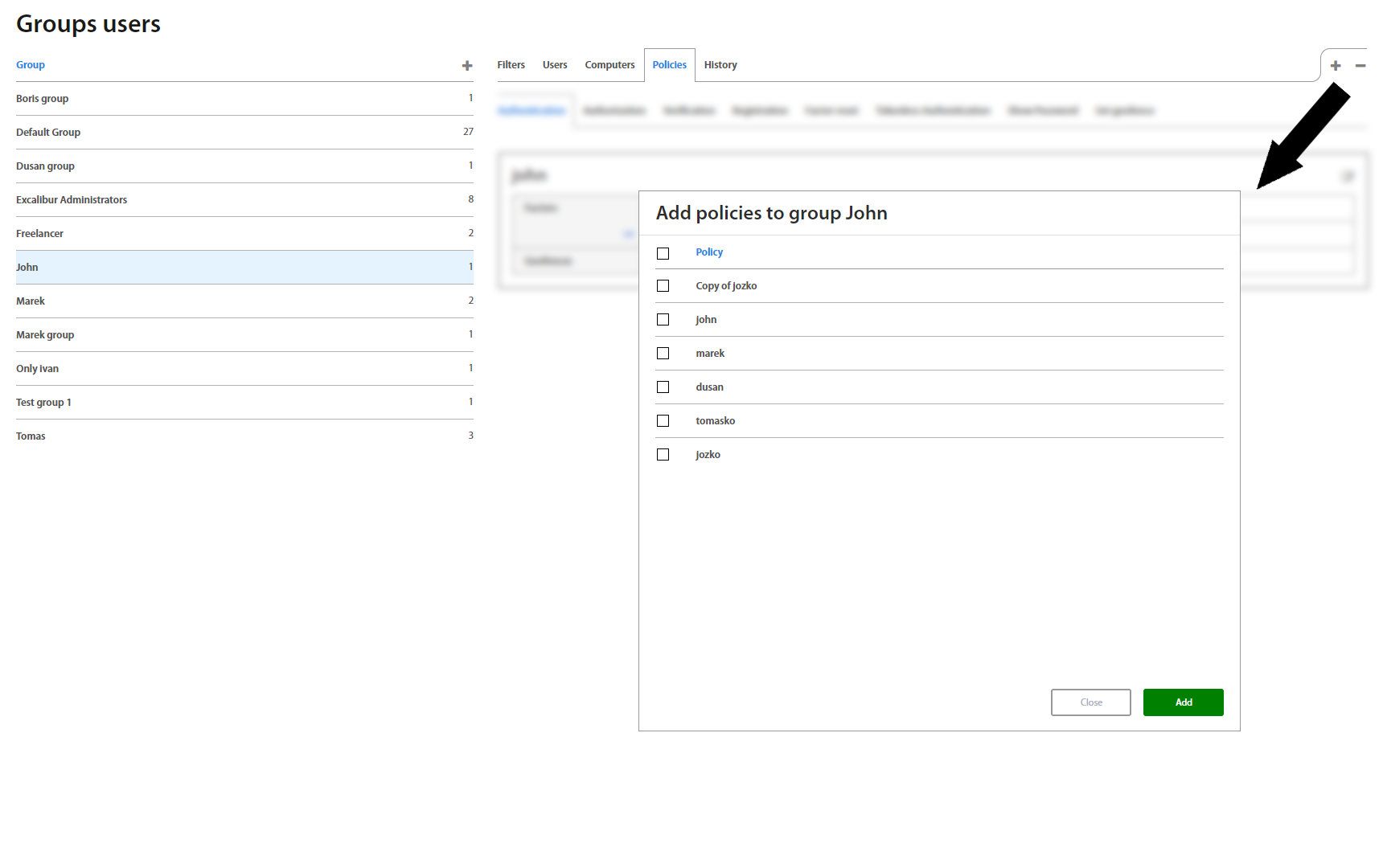
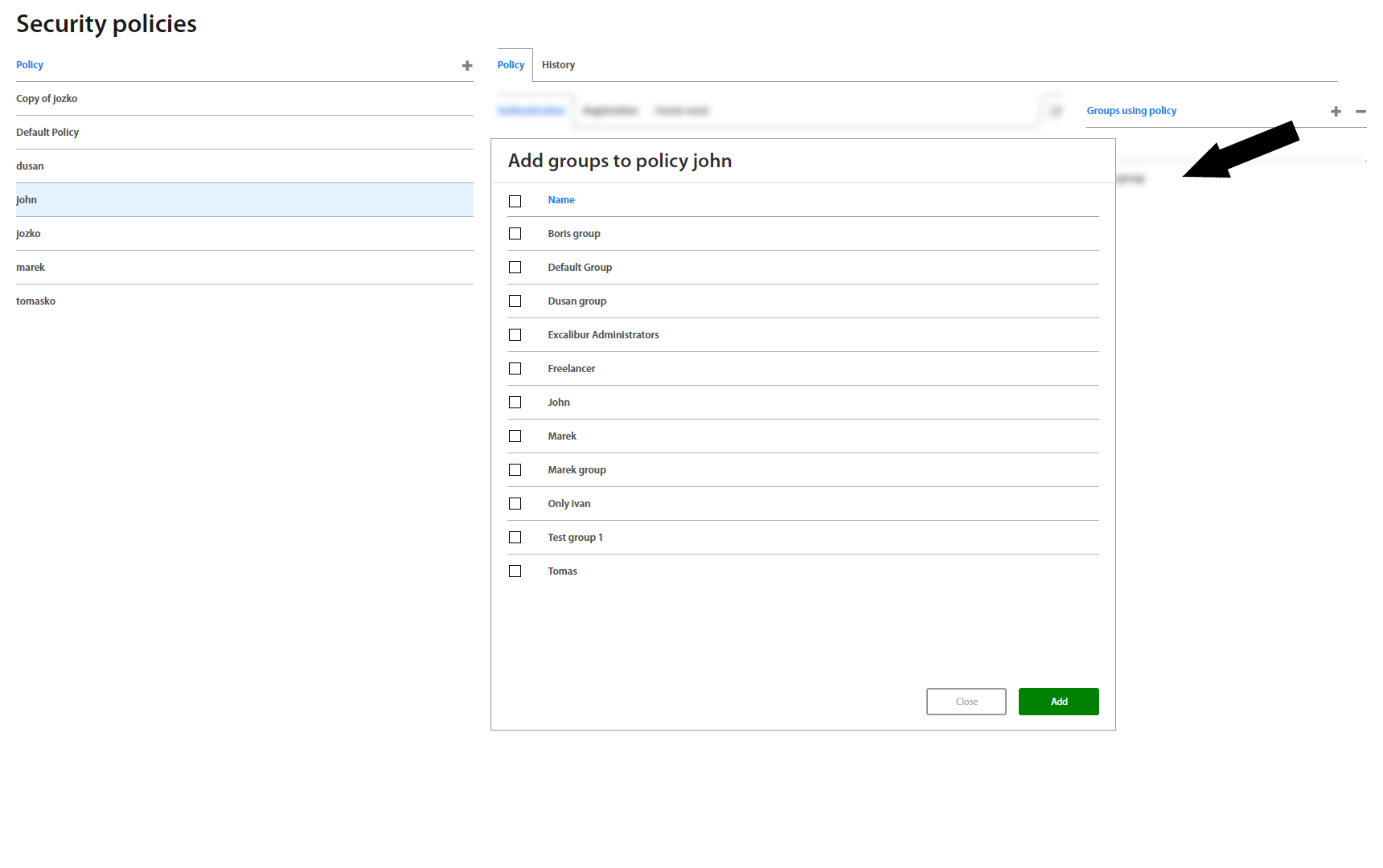
Policies tab shows Security policies assigned to the group separately for Authentication, Authorization, Verification, Registration and Factor Reset. To add a new policy (multiple policies allowed) to the group or to remove an assigned one, just click “+” or “-” button on the top right corner under the Policies tab.
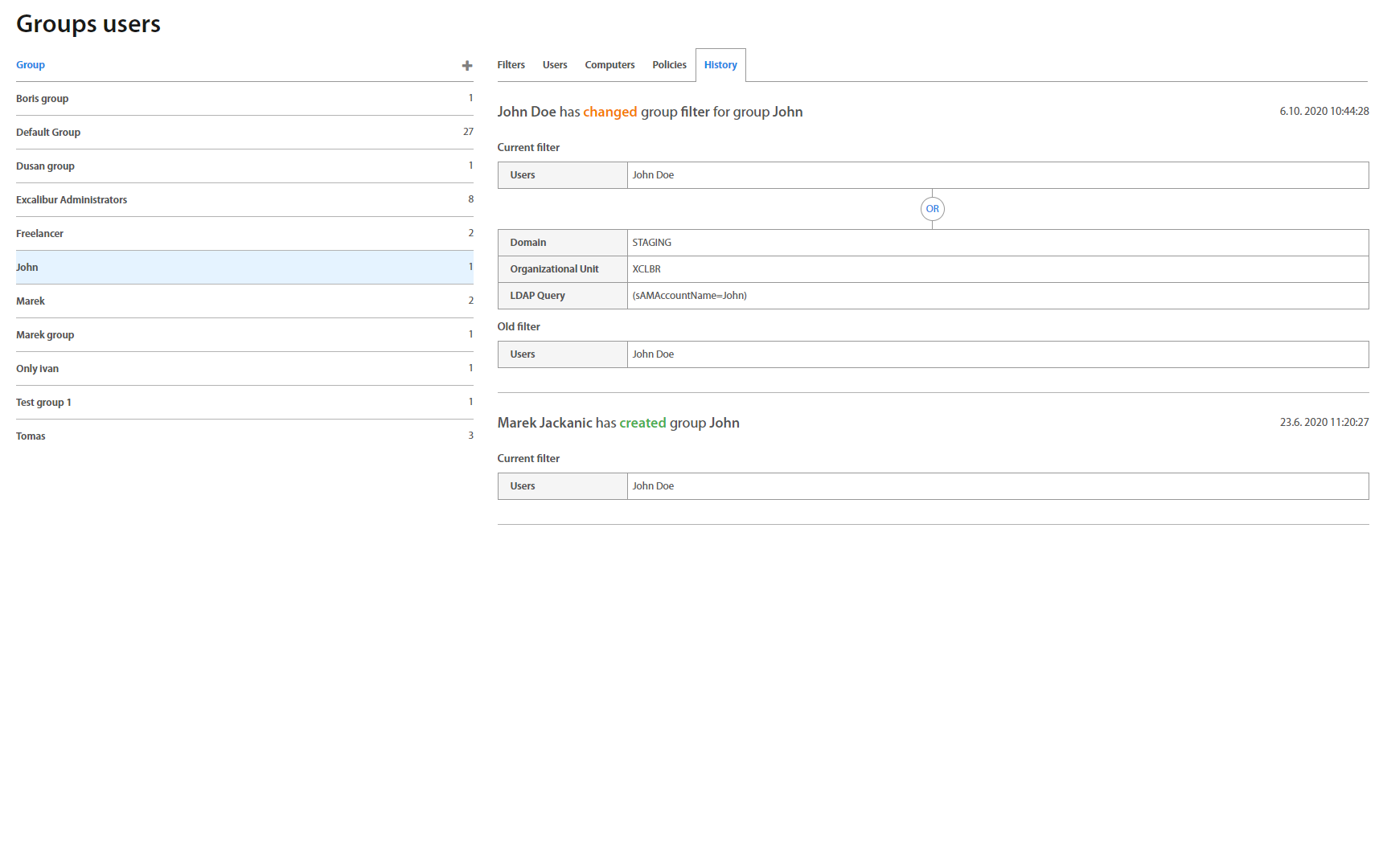
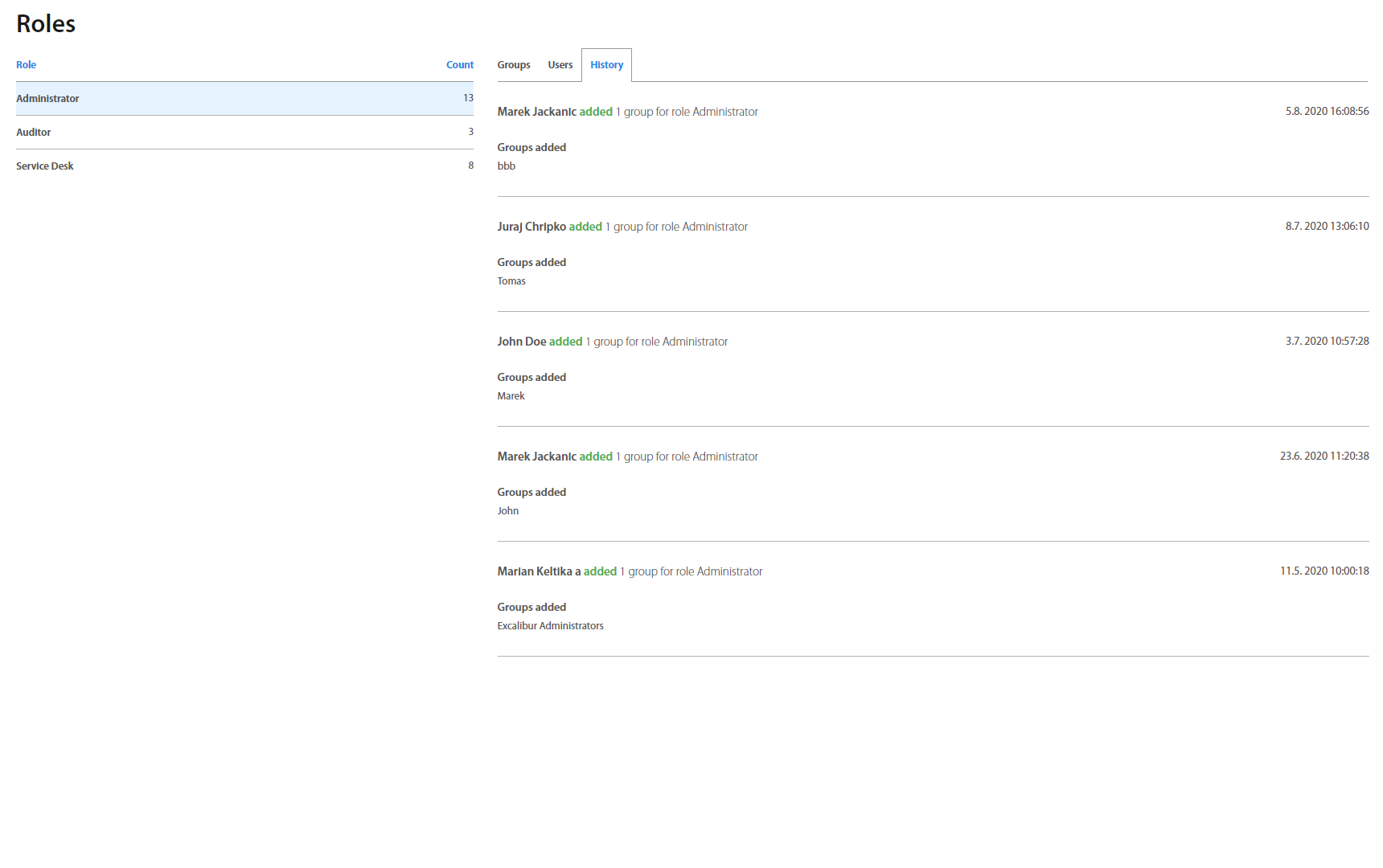
History tab shows changes which were made in the group. It is designed as a list of actions. On the top of the list is the last change which was made.
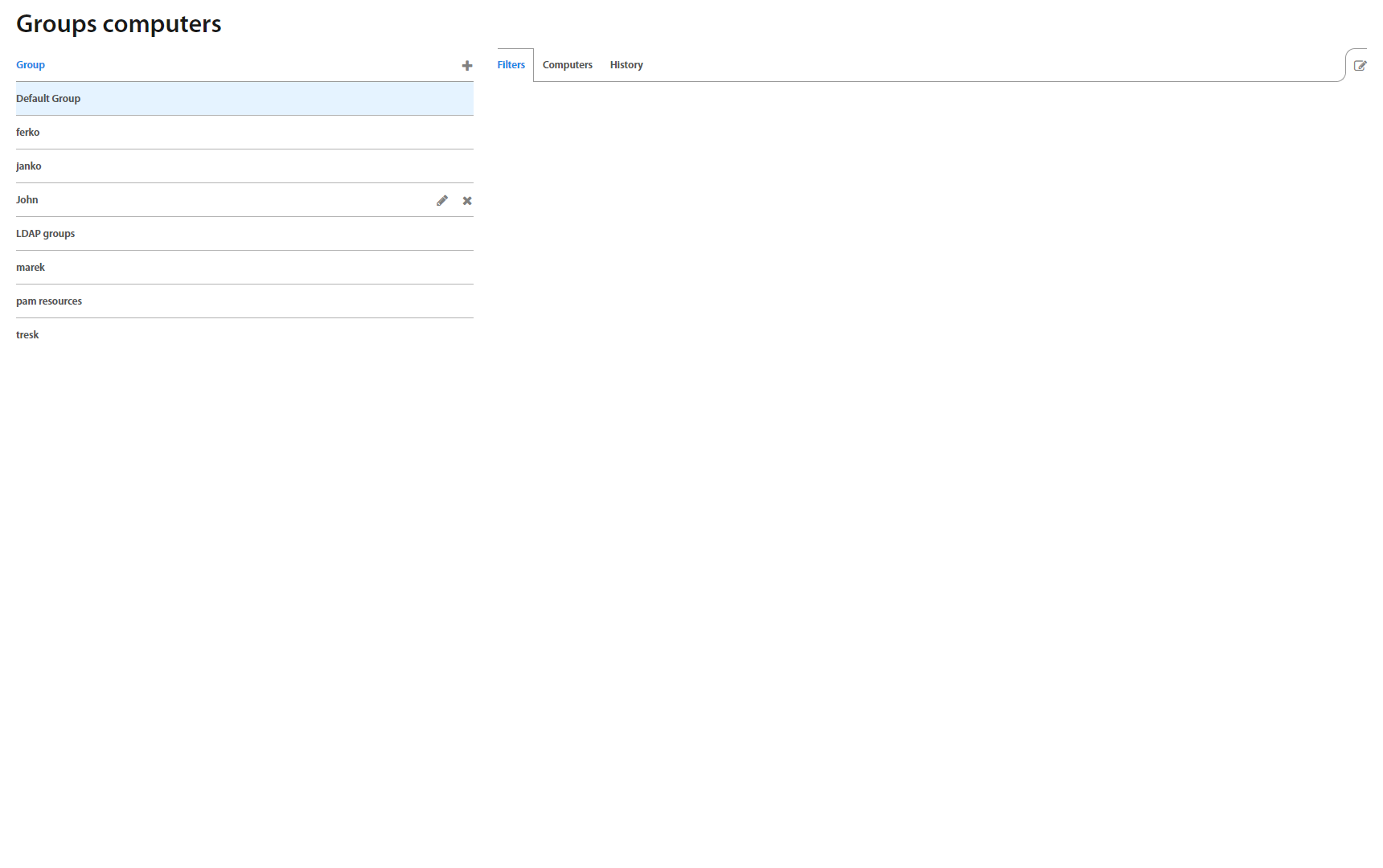
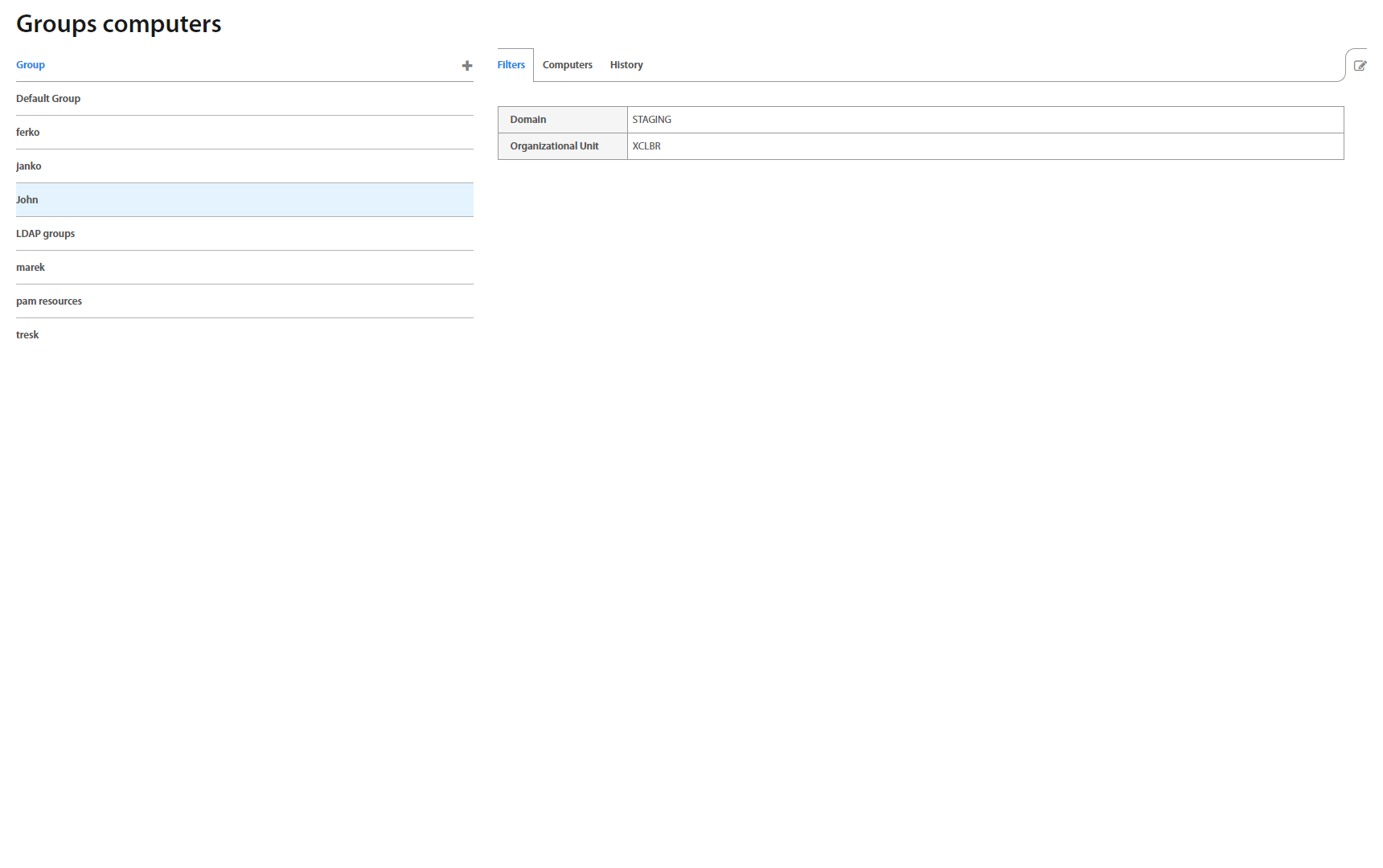
Groups: Computers¶
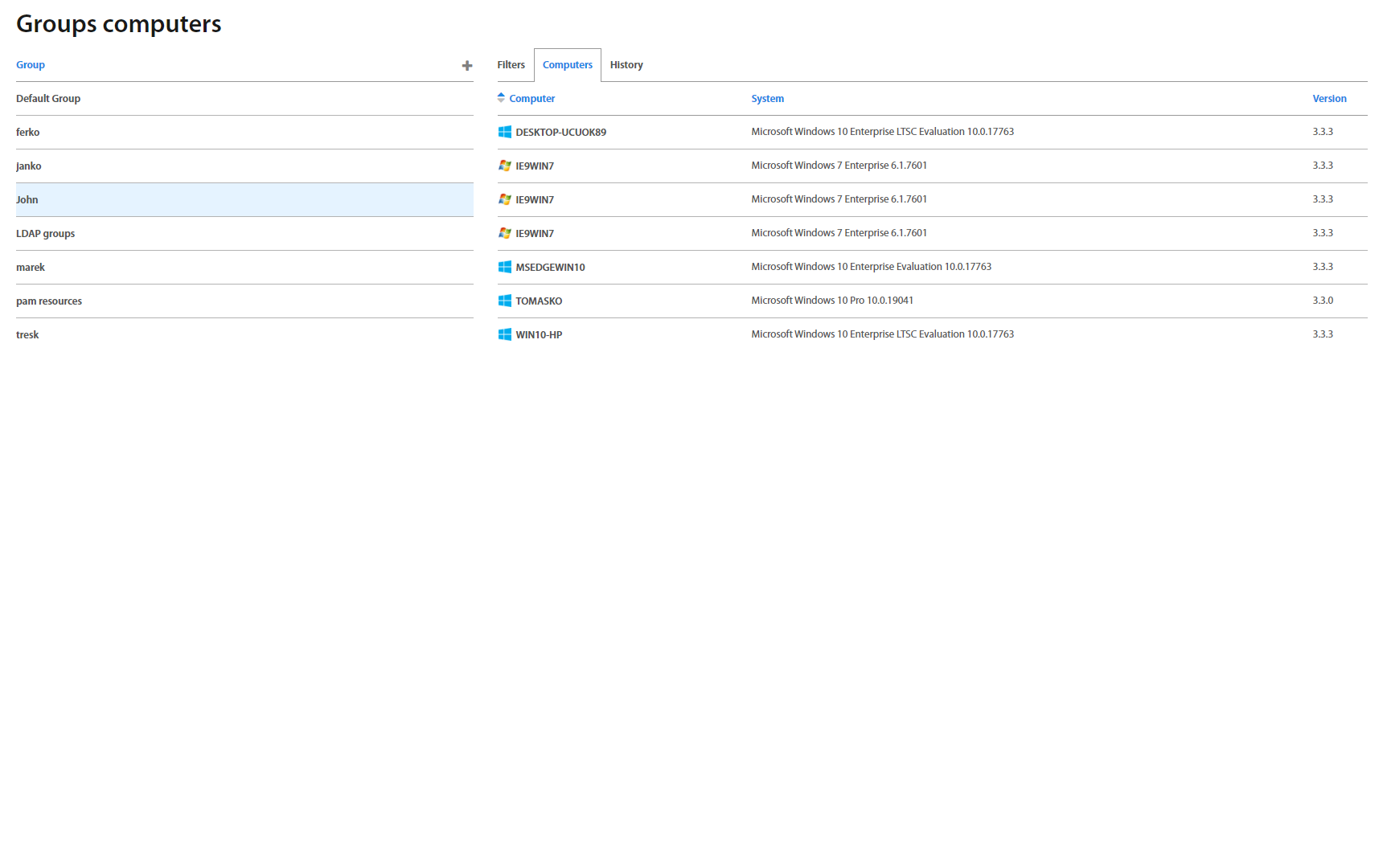
This page lists all computer’s groups created in Excalibur. Clicking on an individual group in the list, group details view shows up. The view consists of Filters and Computers tabs. The first one shows an Organizational Unit the chosen computers group is associated with, while the second one lists all computers this group consists of.
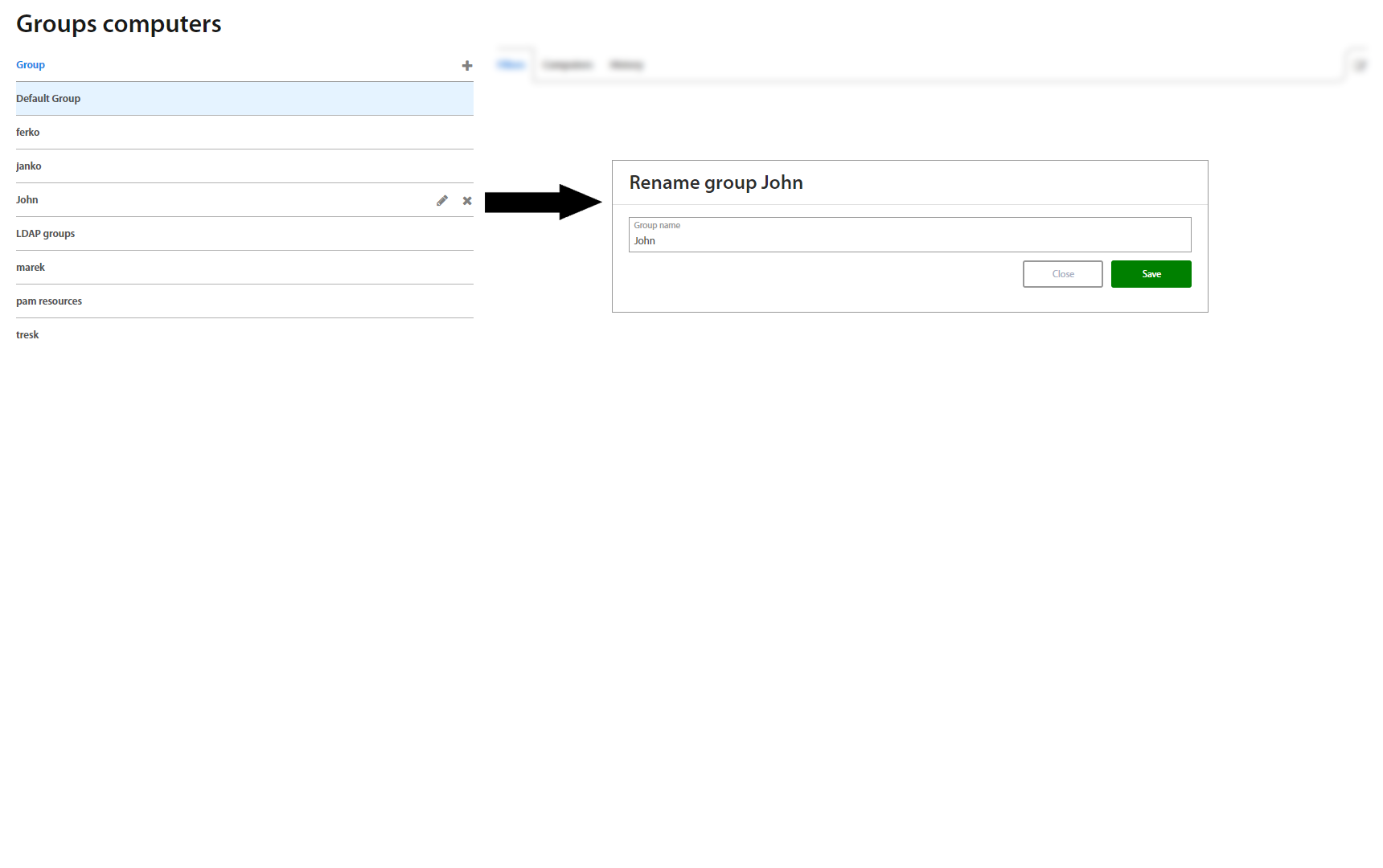
To add a new group, click the “+” button on the top of the Groups list, and to edit the chosen one, click edit in the top right corner of the Group detail..
Computer tab shows list of computers or PAM resources which are assigned to the Computer group.
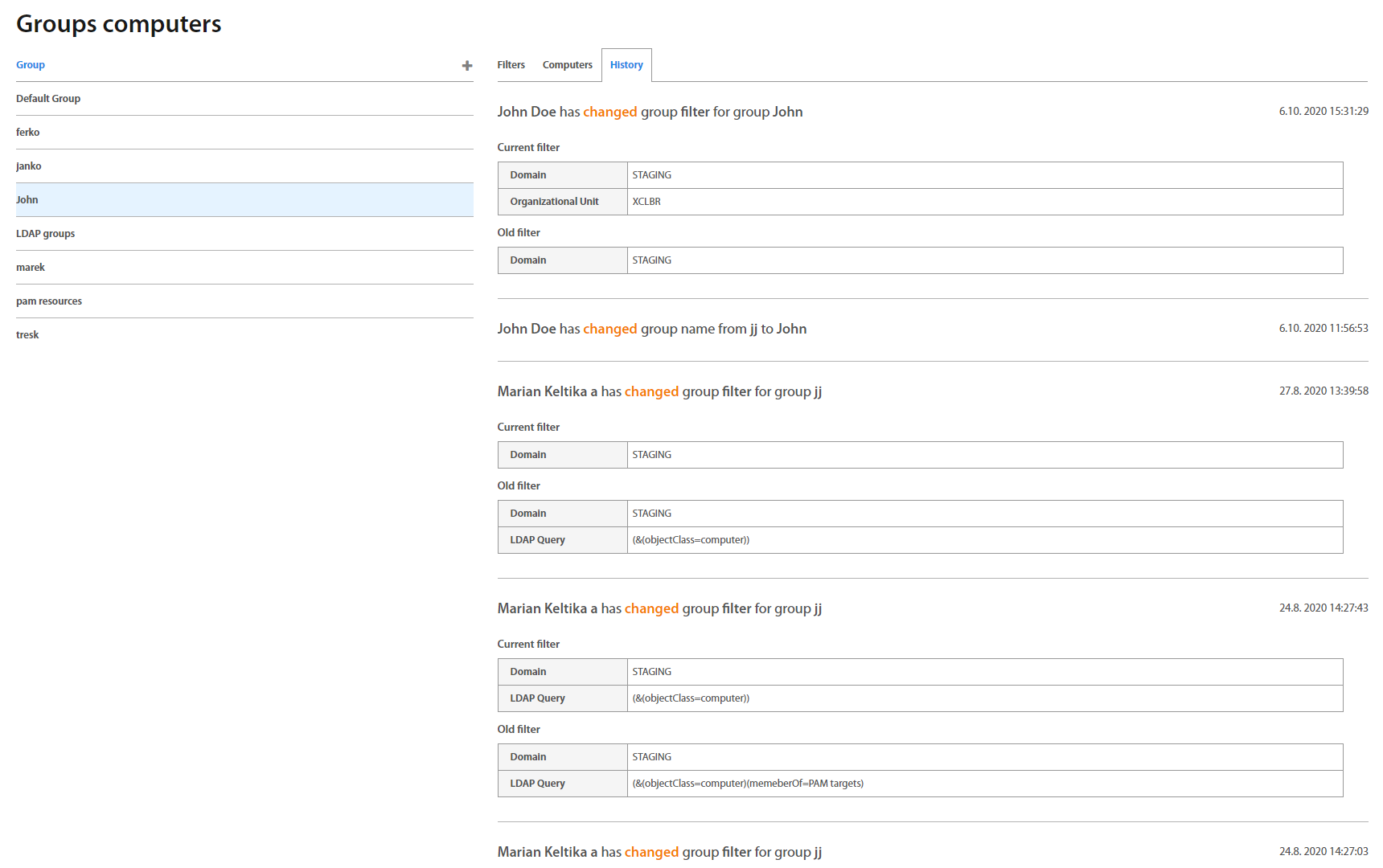
History tab shows changes which were made in the group. It is designed as a list of actions. On the top of the list is the last change which was made.
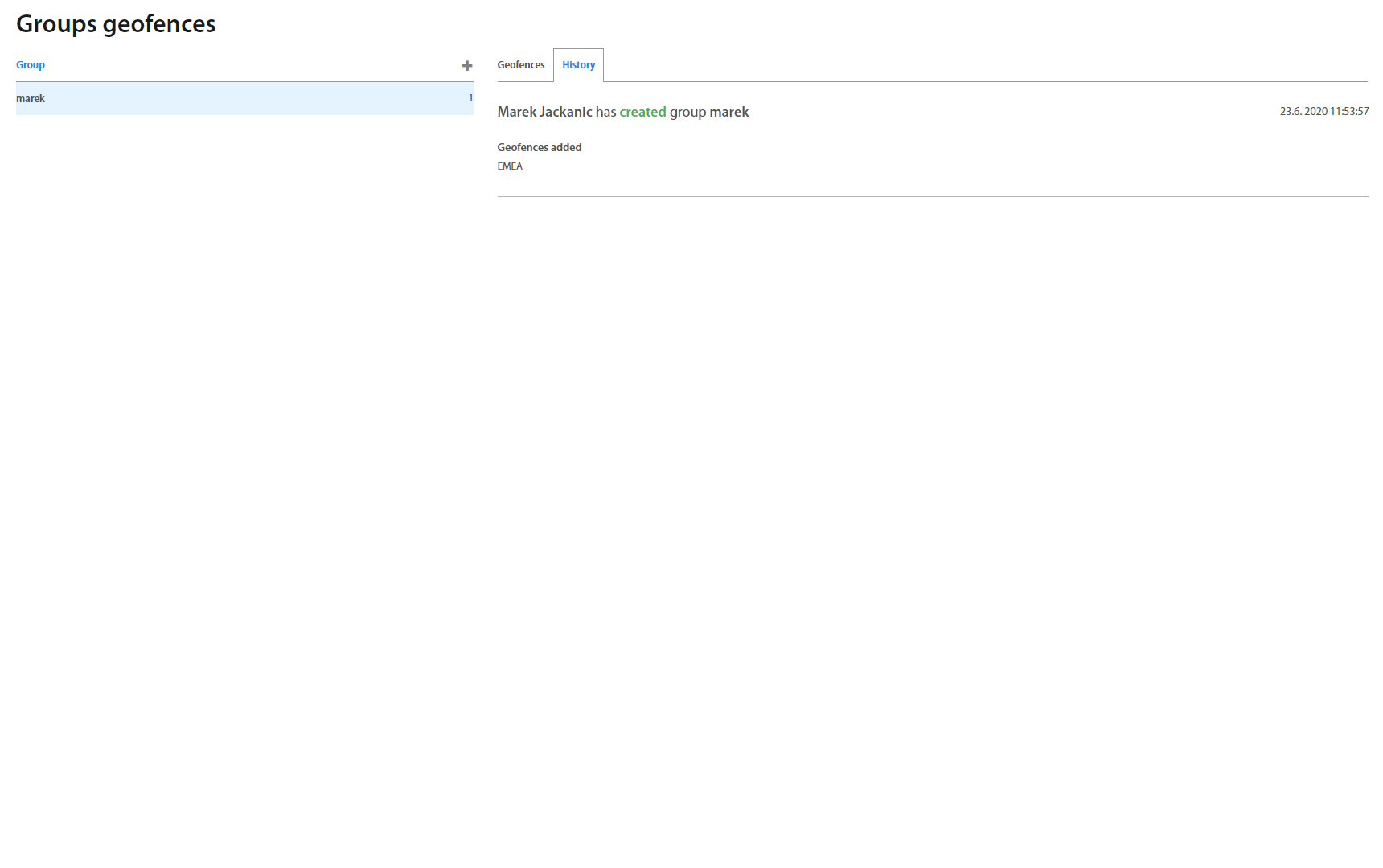
Groups: Geofences¶
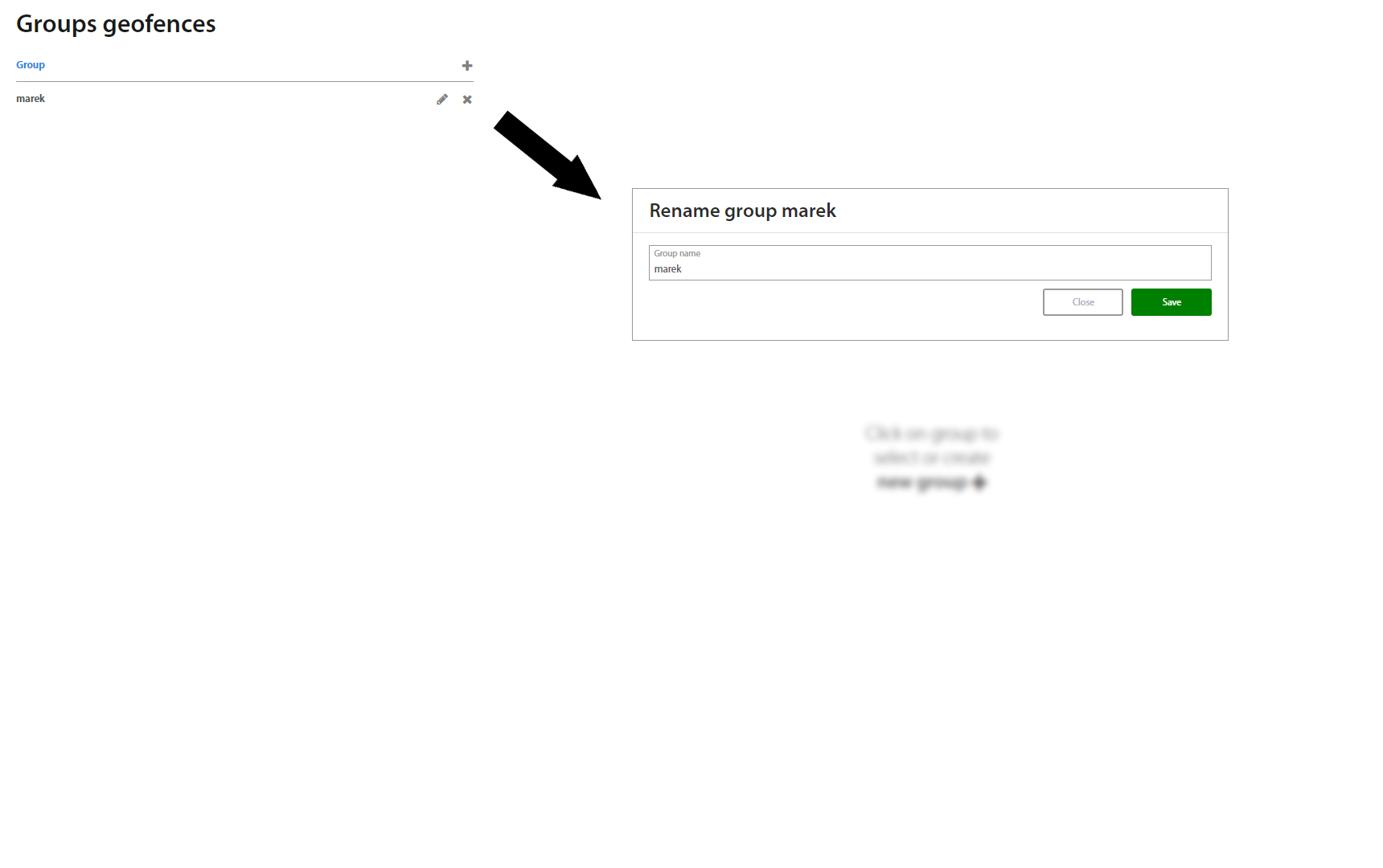
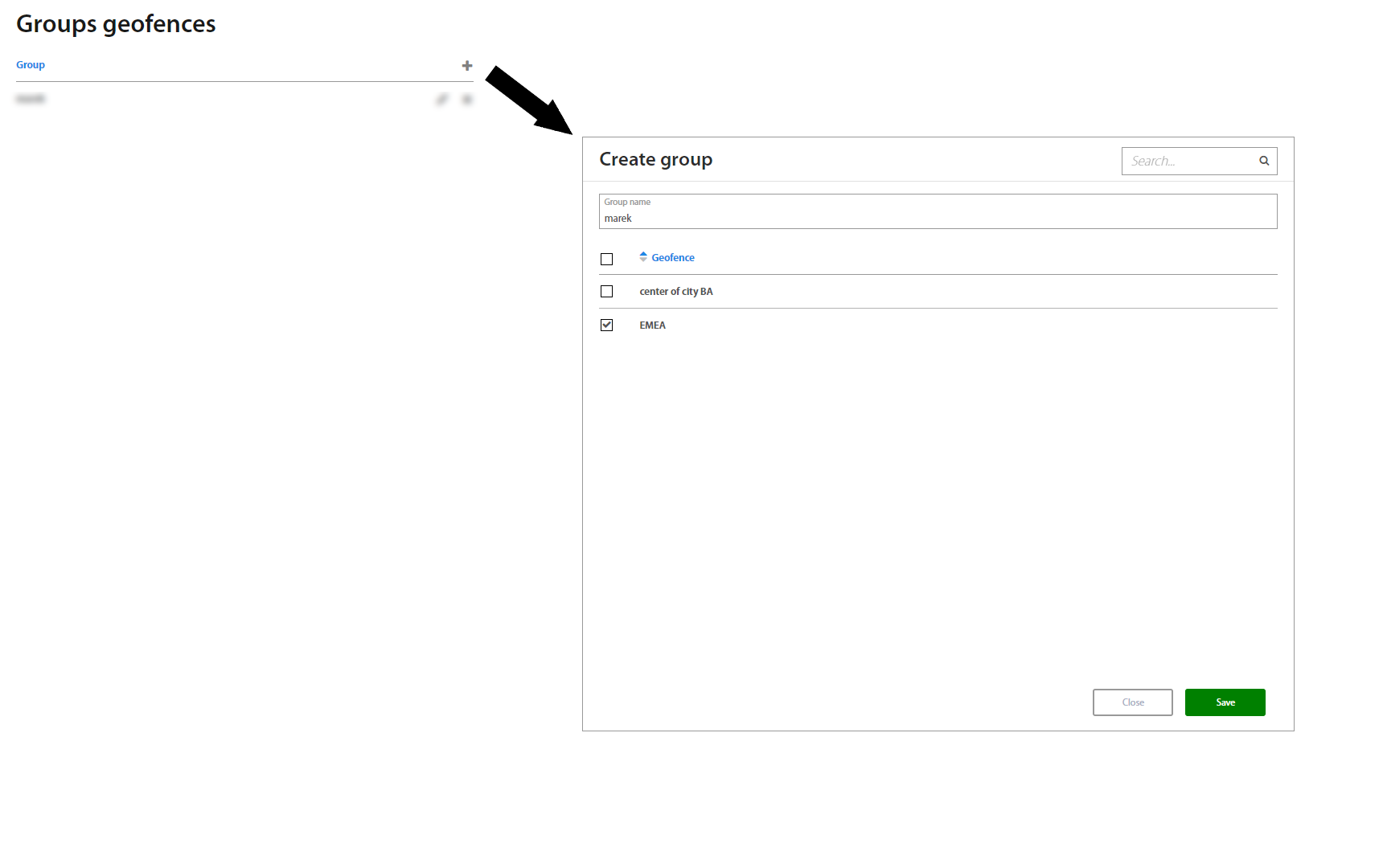
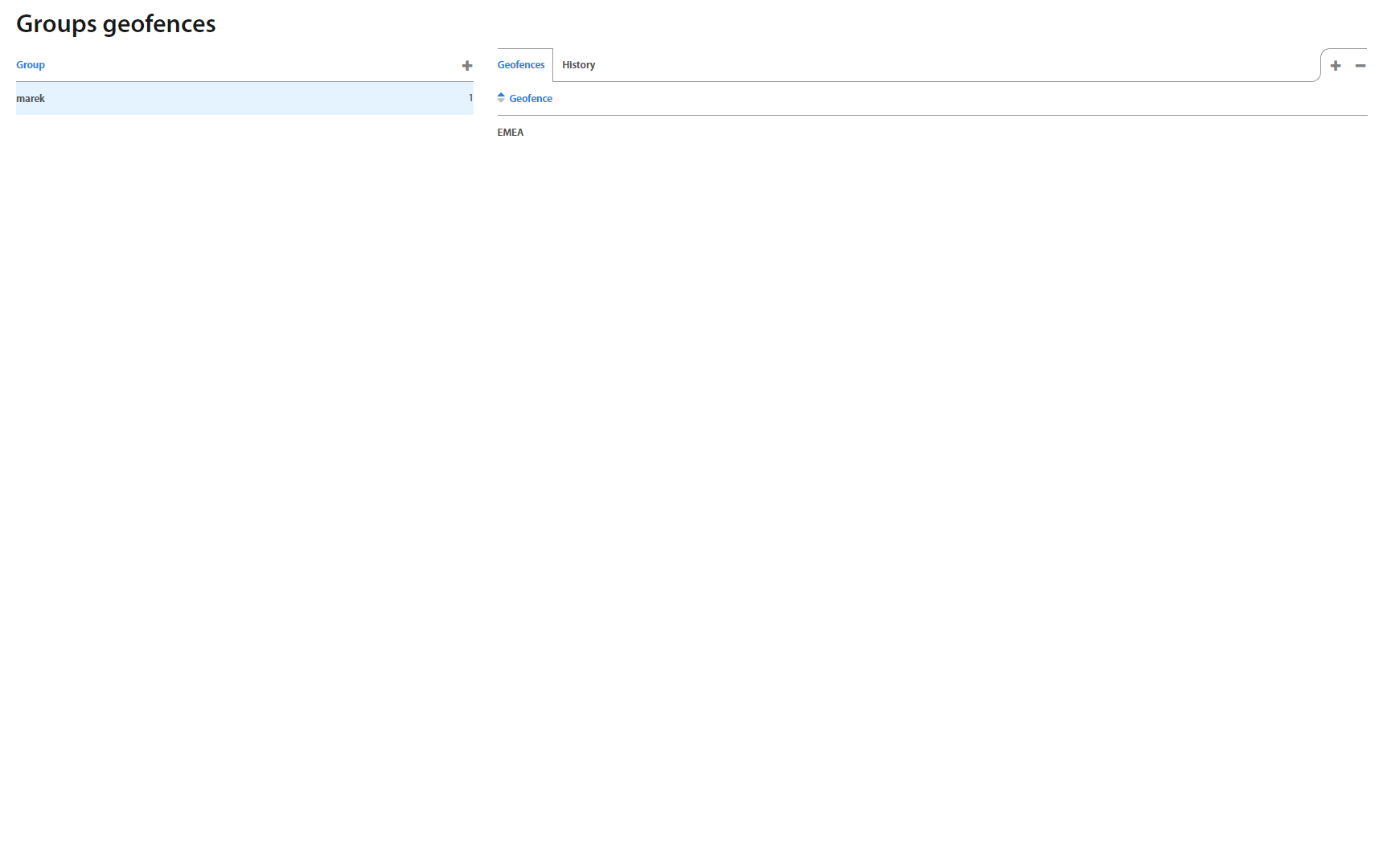
This page lists all Groups of geofences created in Excalibur. To add a new group, click the “+” button on the top of the Groups list. Under an individual selected group, adding and removing geofences from the group is available.
Click on specific group to show group's details.
Security¶
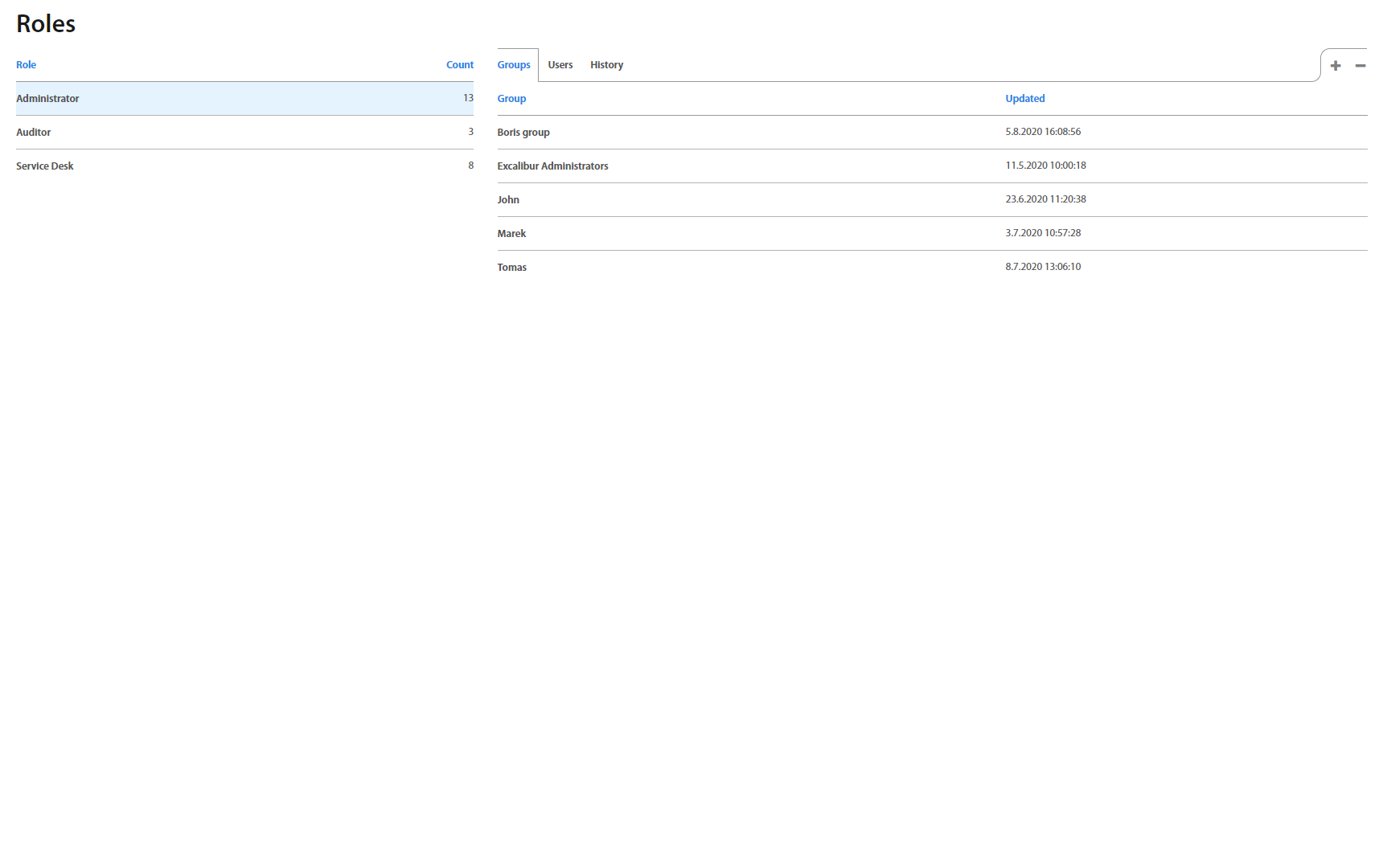
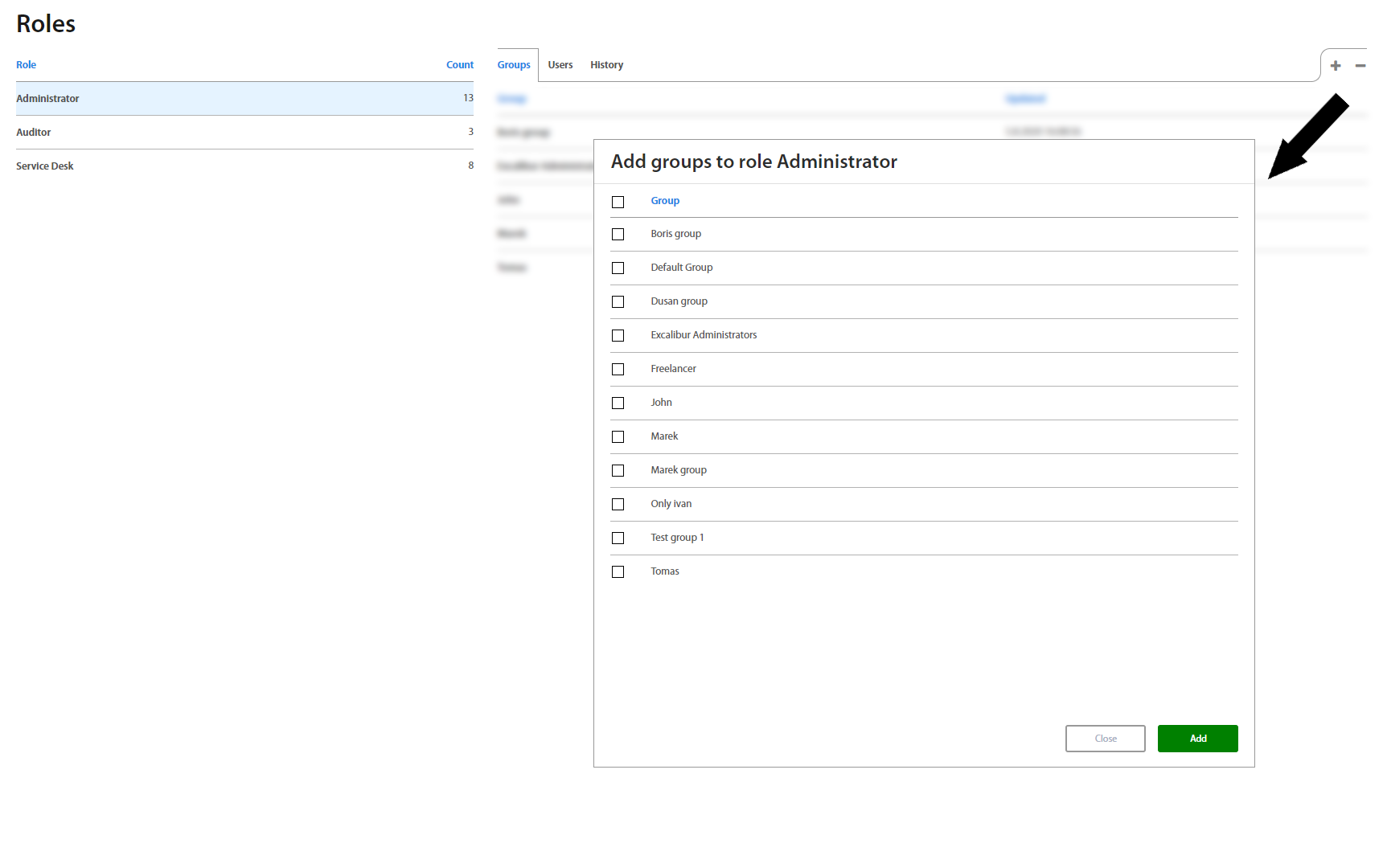
Roles¶
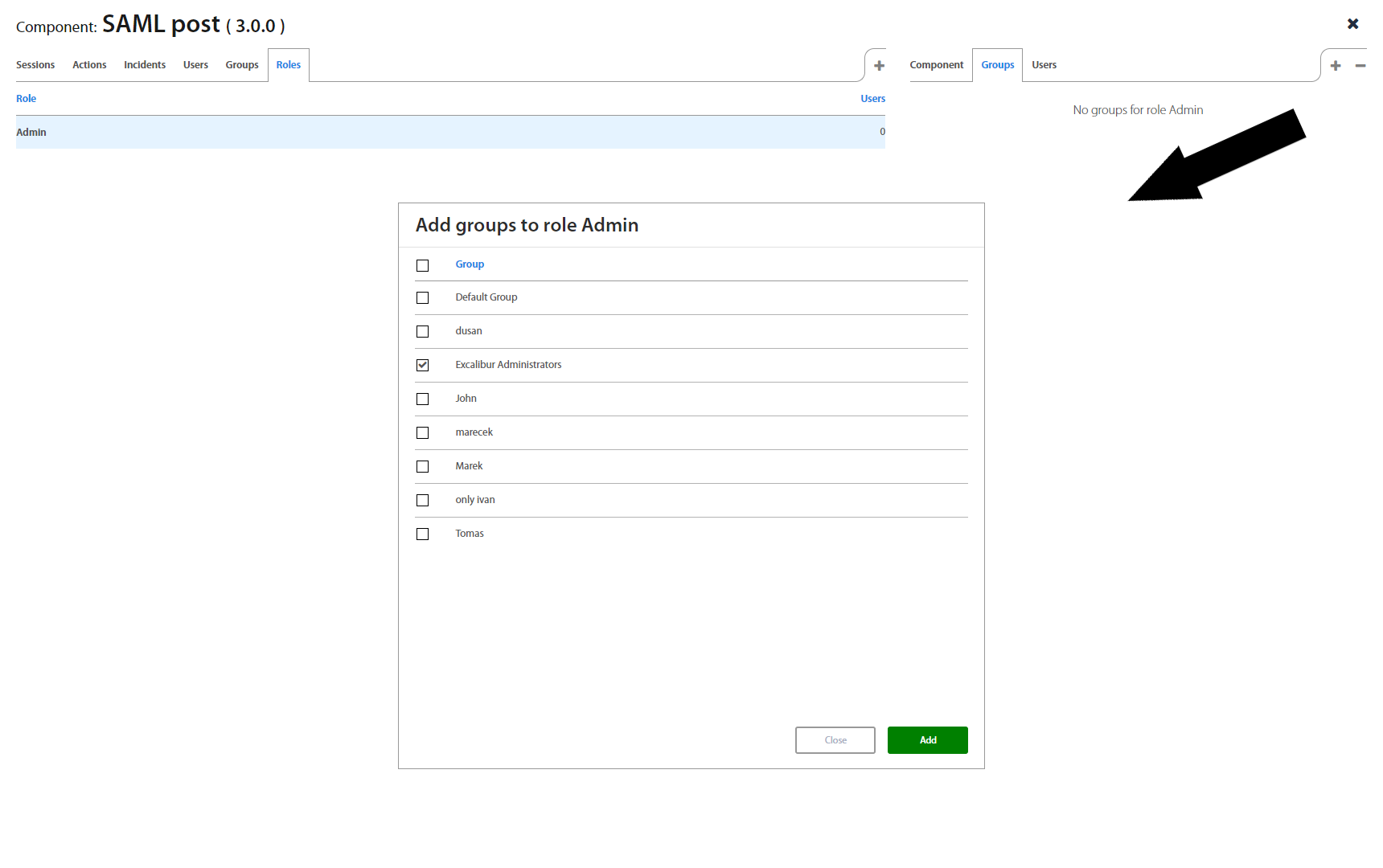
Roles page lists all roles from the Company's Active Directory. By clicking on an individual role, it’s possible to assign Excalibur Groups to the role, as well as to see all registered users having this role.
Security policies¶
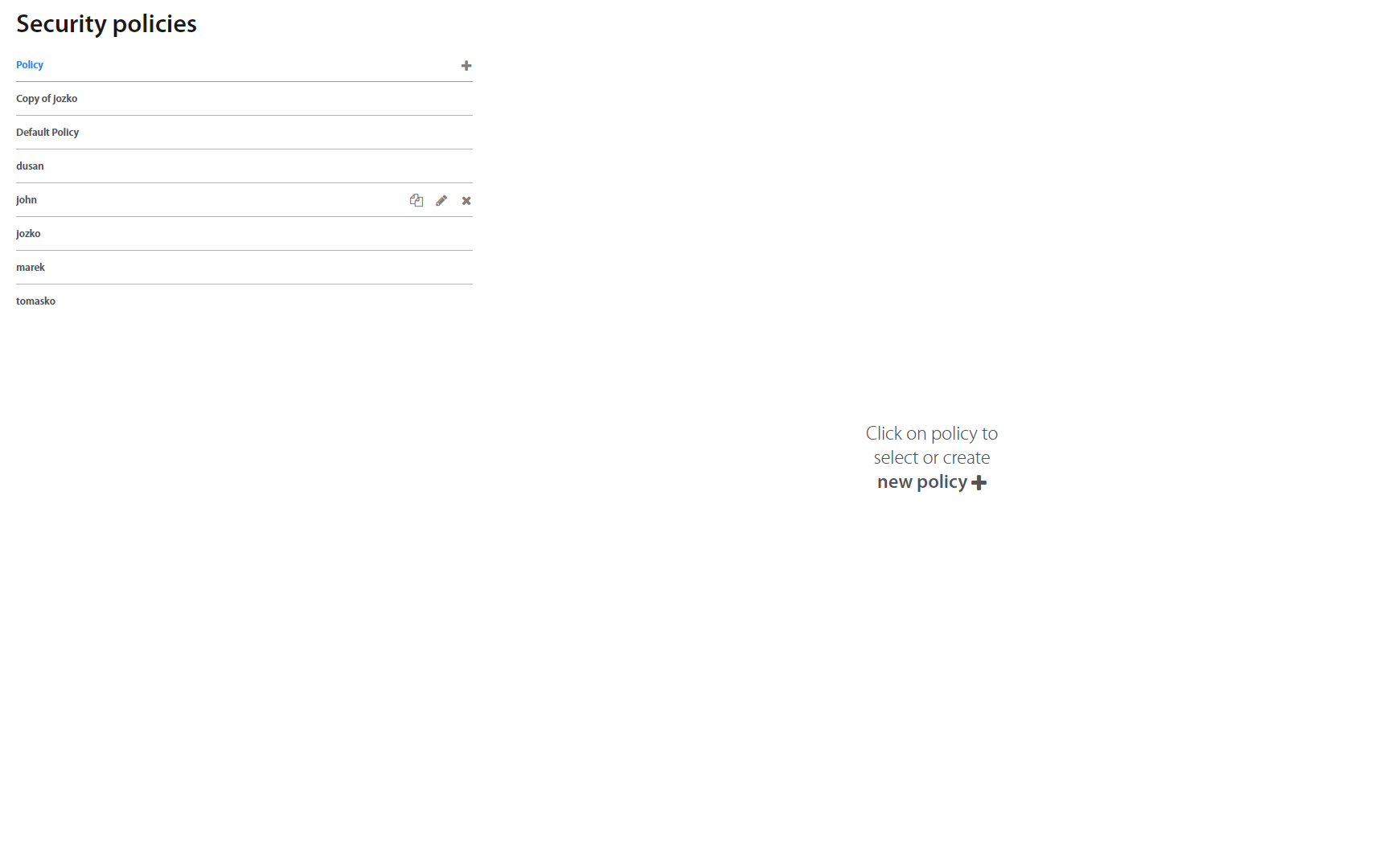
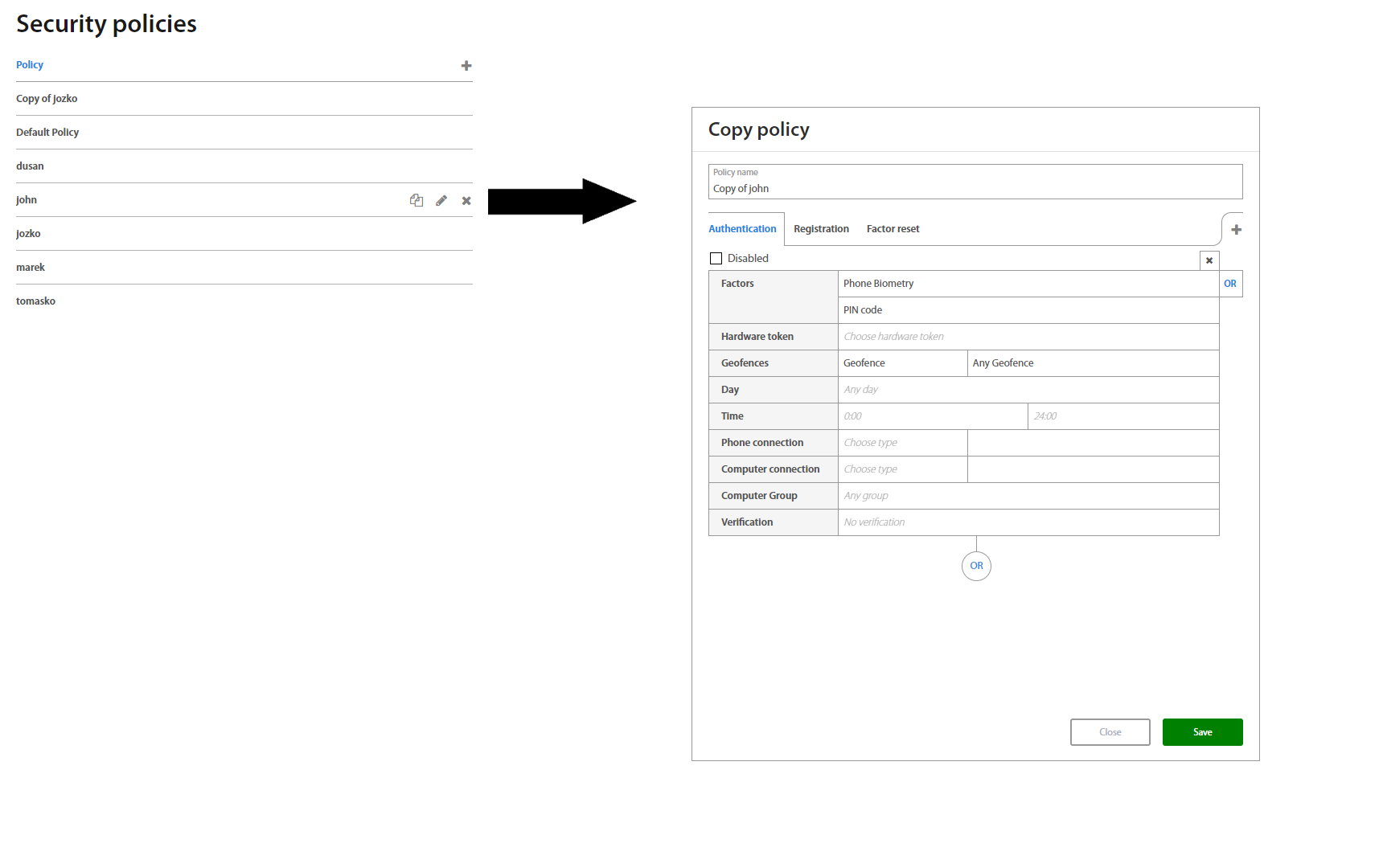
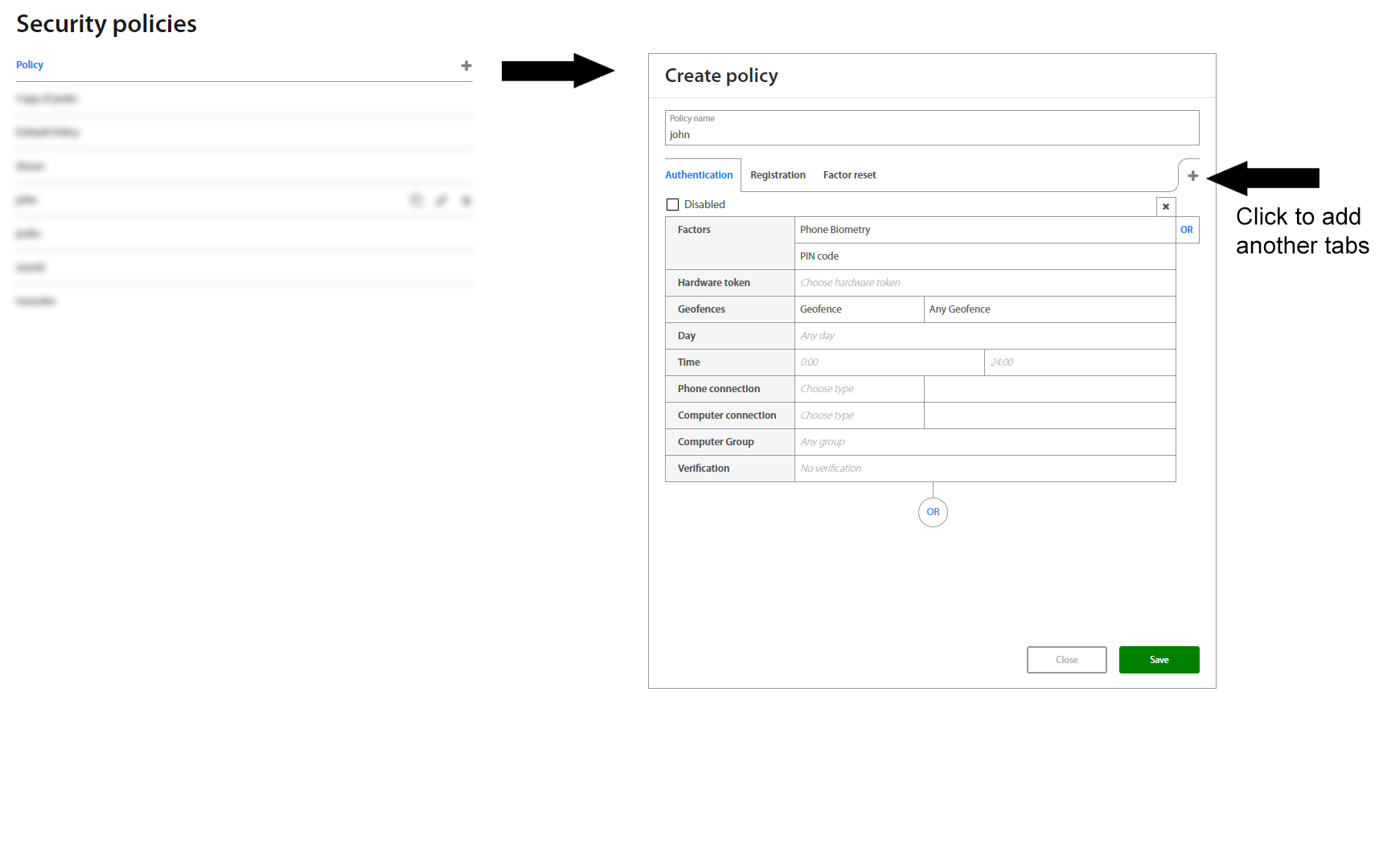
On the Security policies page it’s possible to view, edit, add or remove individual policies.
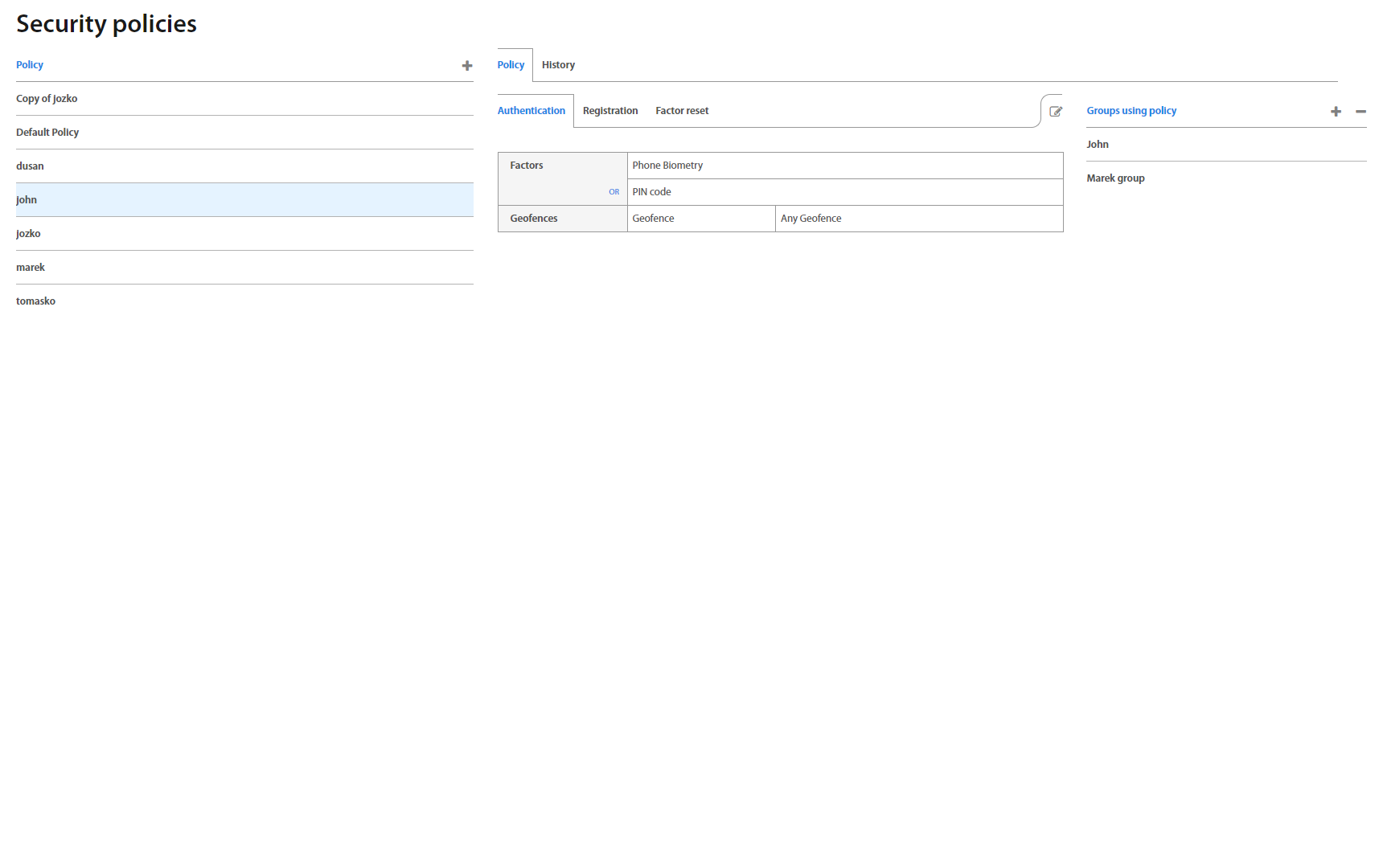
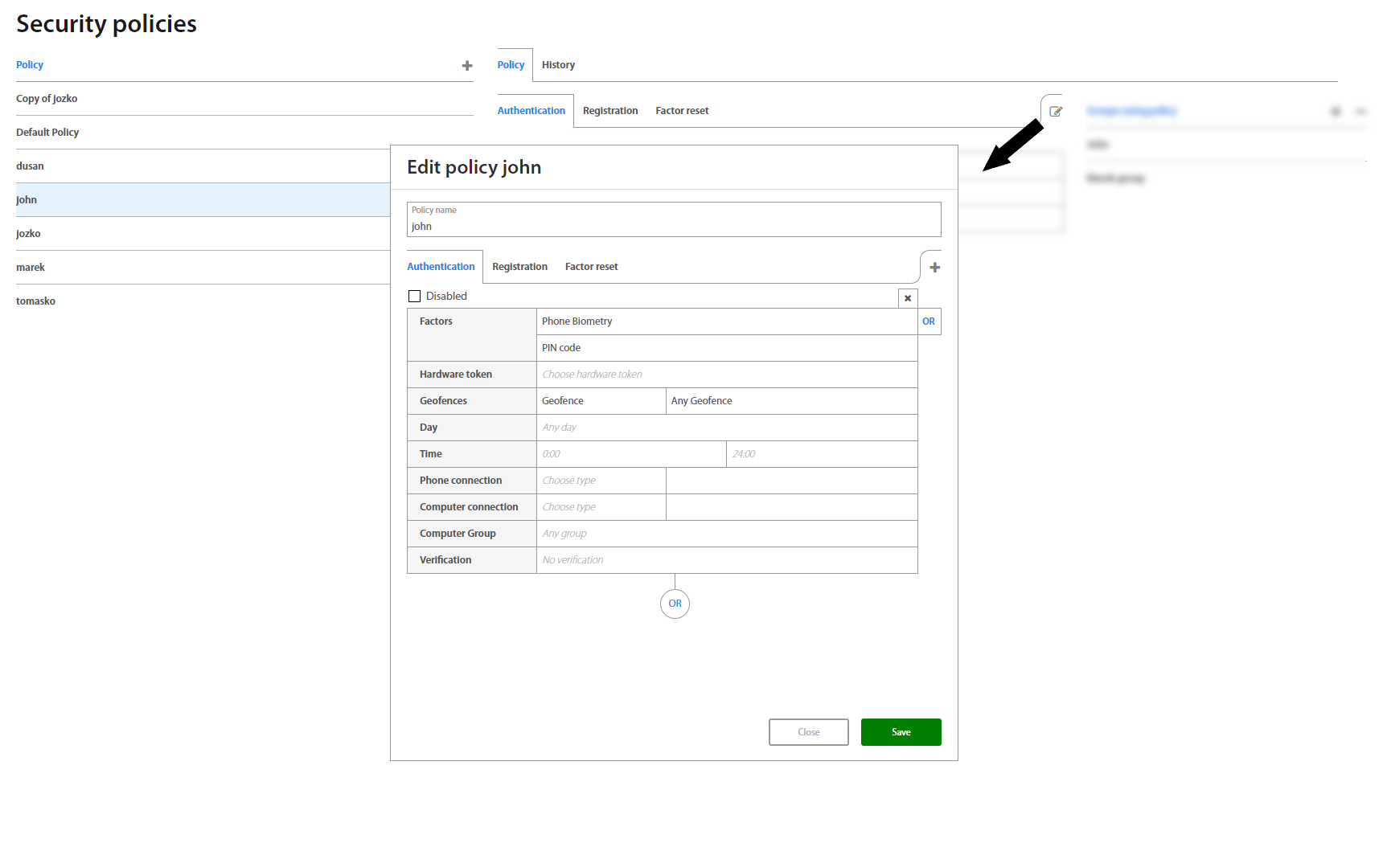
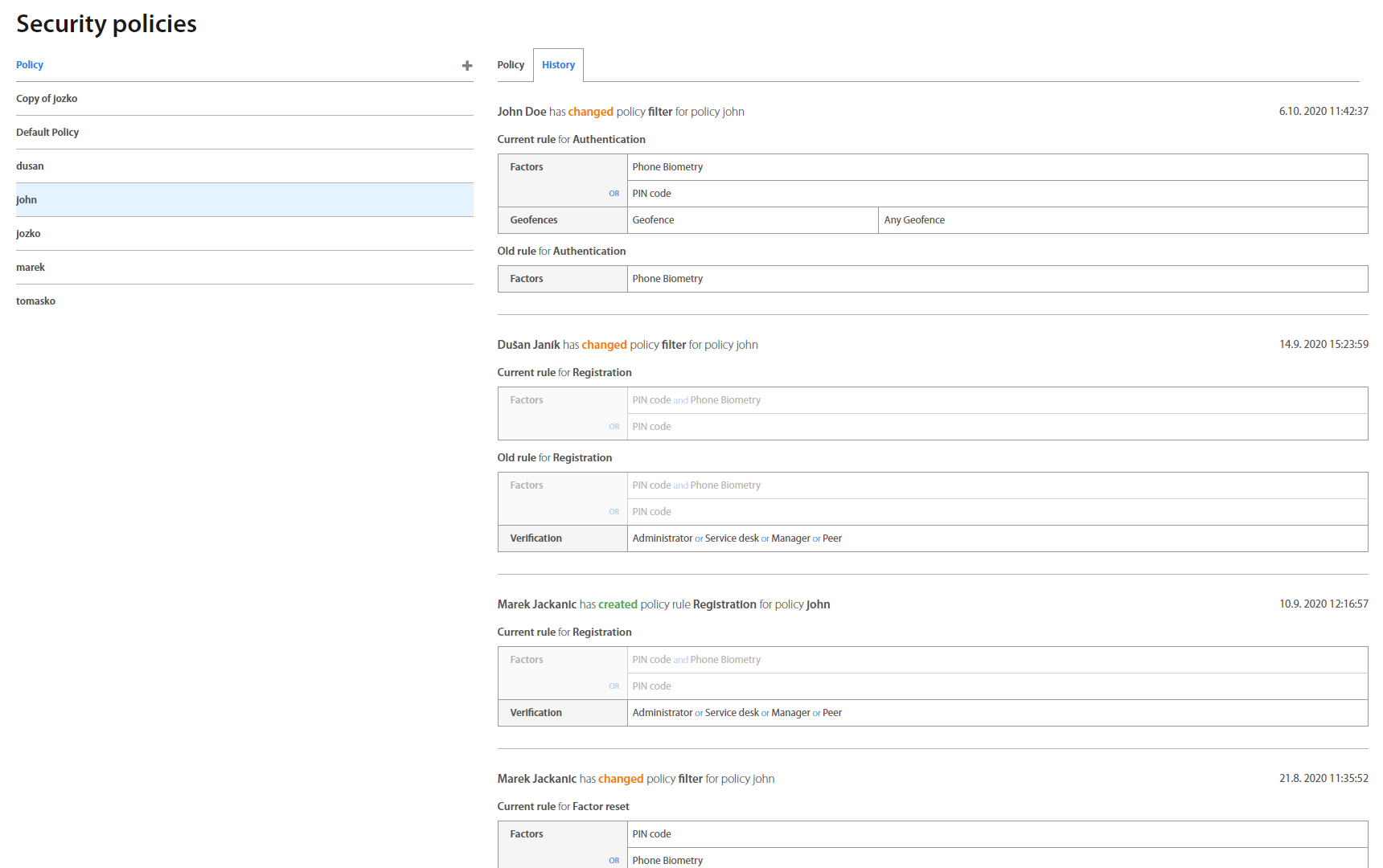
Clicking on a policy shows a view with policies for Authorization, Authentication, Verification, Registration Factor Reset, Show password and Set geofence, which also allows to directly edit them - assign and combine different factors and restrictions for different use-cases for each individual action.
On the right side there’s also a list of all groups using a given policy, and it’s also possible to add and remove them directly in this list.
For detailed information about Security policies please see Excalibur Security Policies Management.
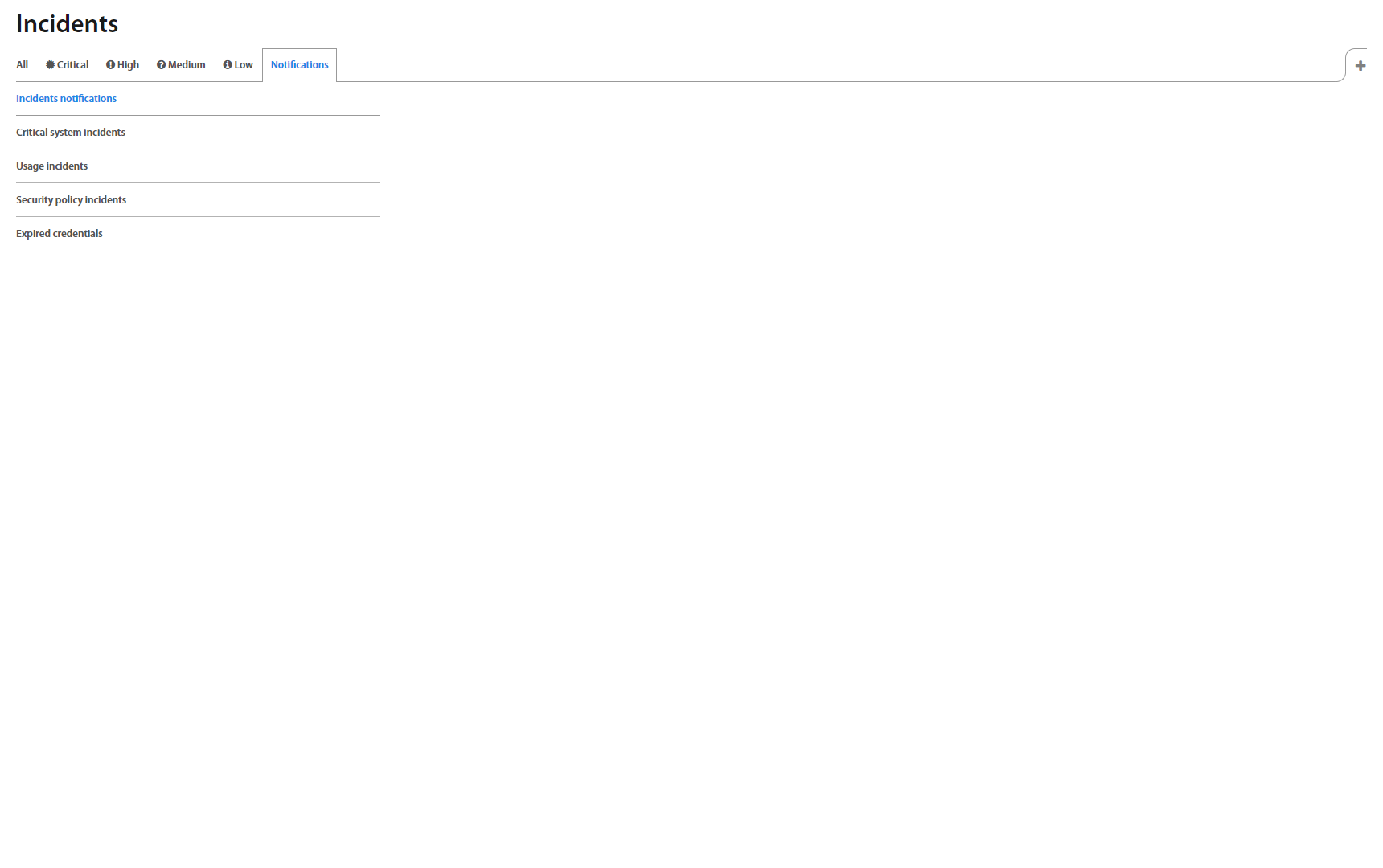
Incidents¶
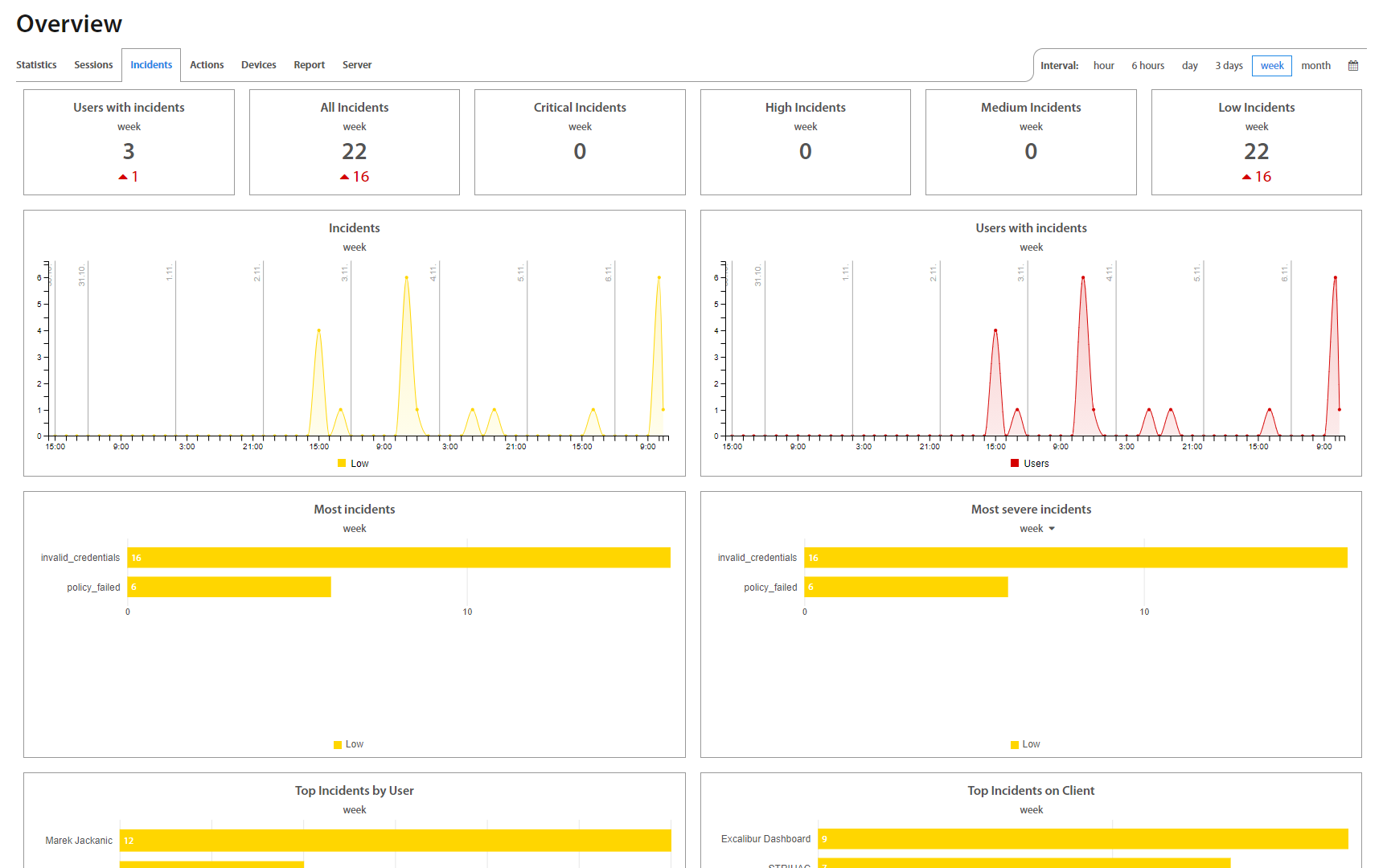
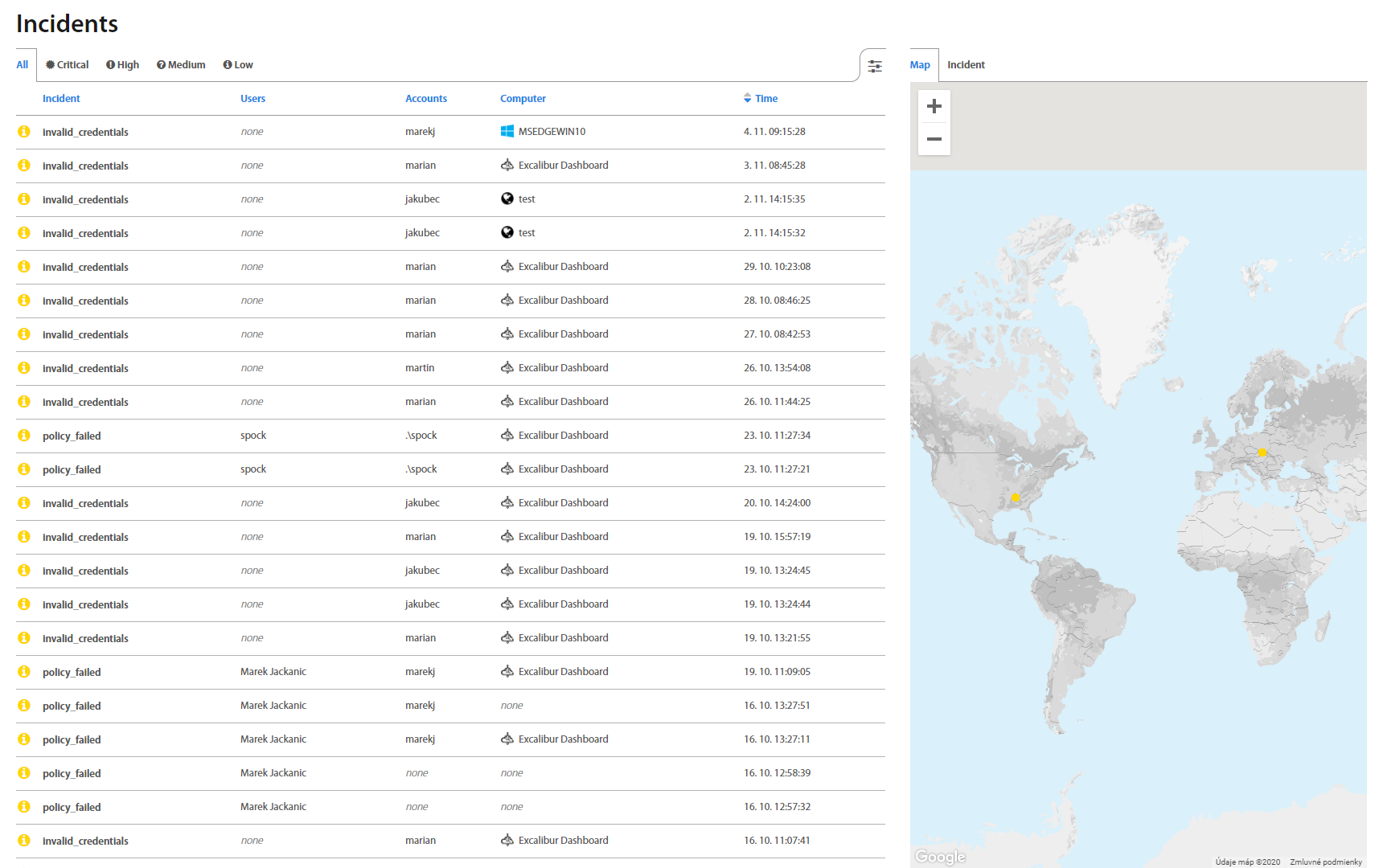
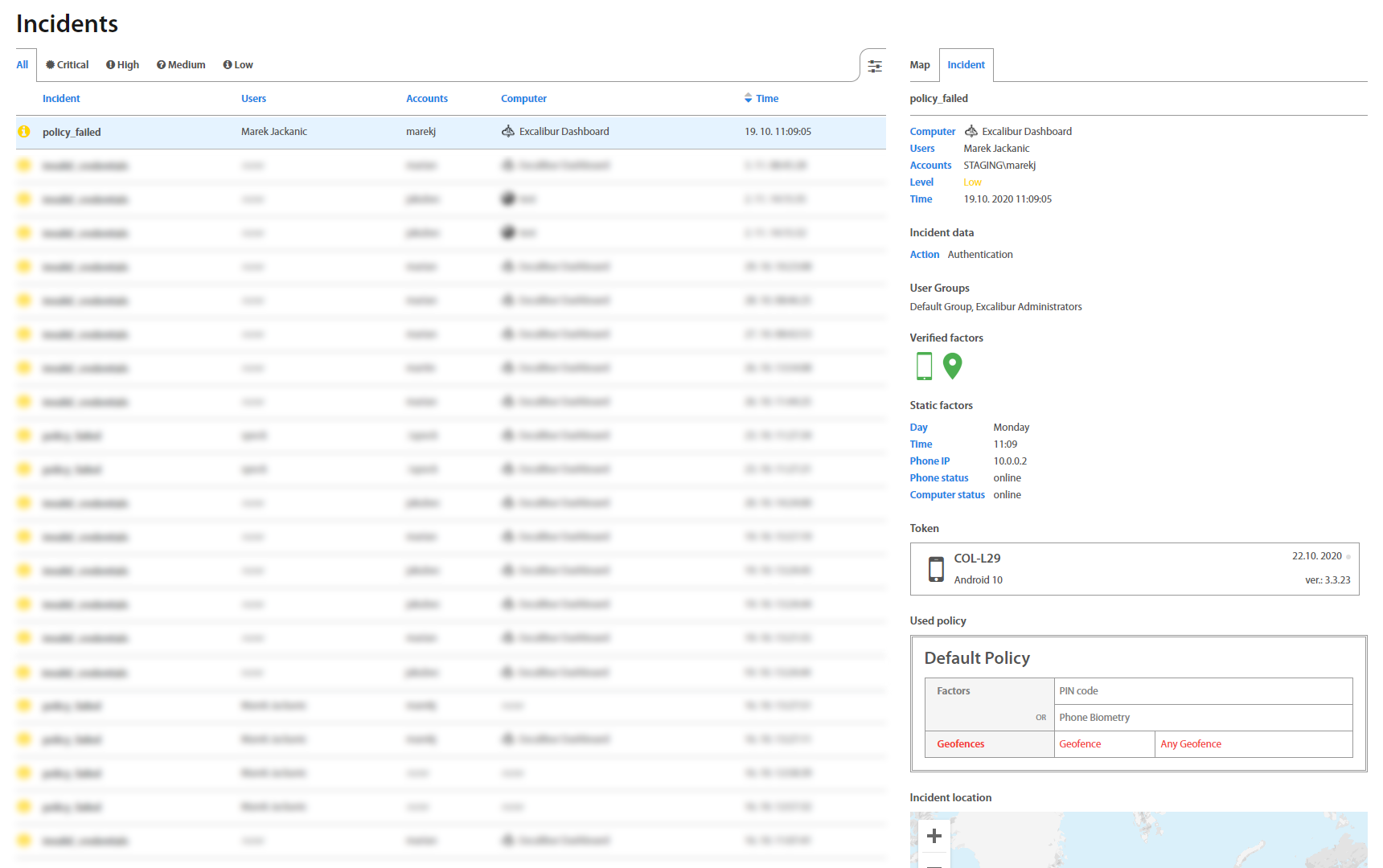
Incidents page lists all registered Incidents in Excalibur. By clicking on an individual Incident, detailed information shows up. Factors that failed are shown red so Administrator may find out what was the reason for User's failed action. Administrator can see there also Incident location on the map which may help him with investigation. Besides a list with all incidents, there are also separate tabs that group incidents based on their priority.
Incidents Notifications /In Progress/¶
Configuration for sending email consists of following steps:
1. Create SMTP configuration used for sending emails - Chapter Configurations
2. Create notification definition, which includes recipients (group of users) - Chapter Notification
3. Create incident notification where you specify which incidents will trigger appropriate notification - Chapter Incidents: Notifications
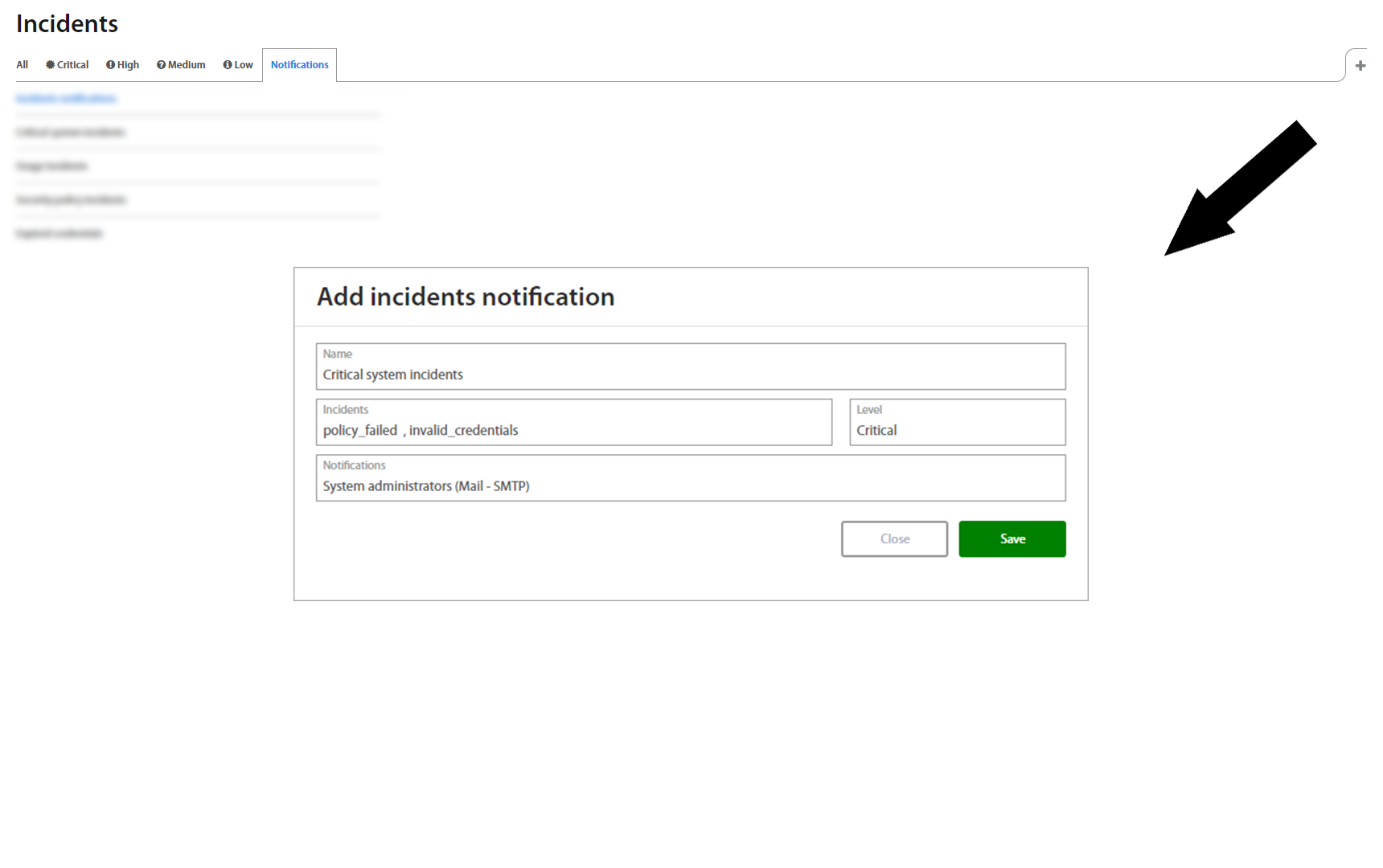
To specify incidents for email notifications click on the + button and define required fields:
| Field | Description |
|---|---|
| Name | Name for Incident notification group. |
| Incidents | Select incidents which will trigger the configured notification |
| Level | Incident severity (Low, Medium, High, Critical) |
| Notification | Select notification (defined in Notification part) used when incident(s) occurs. |
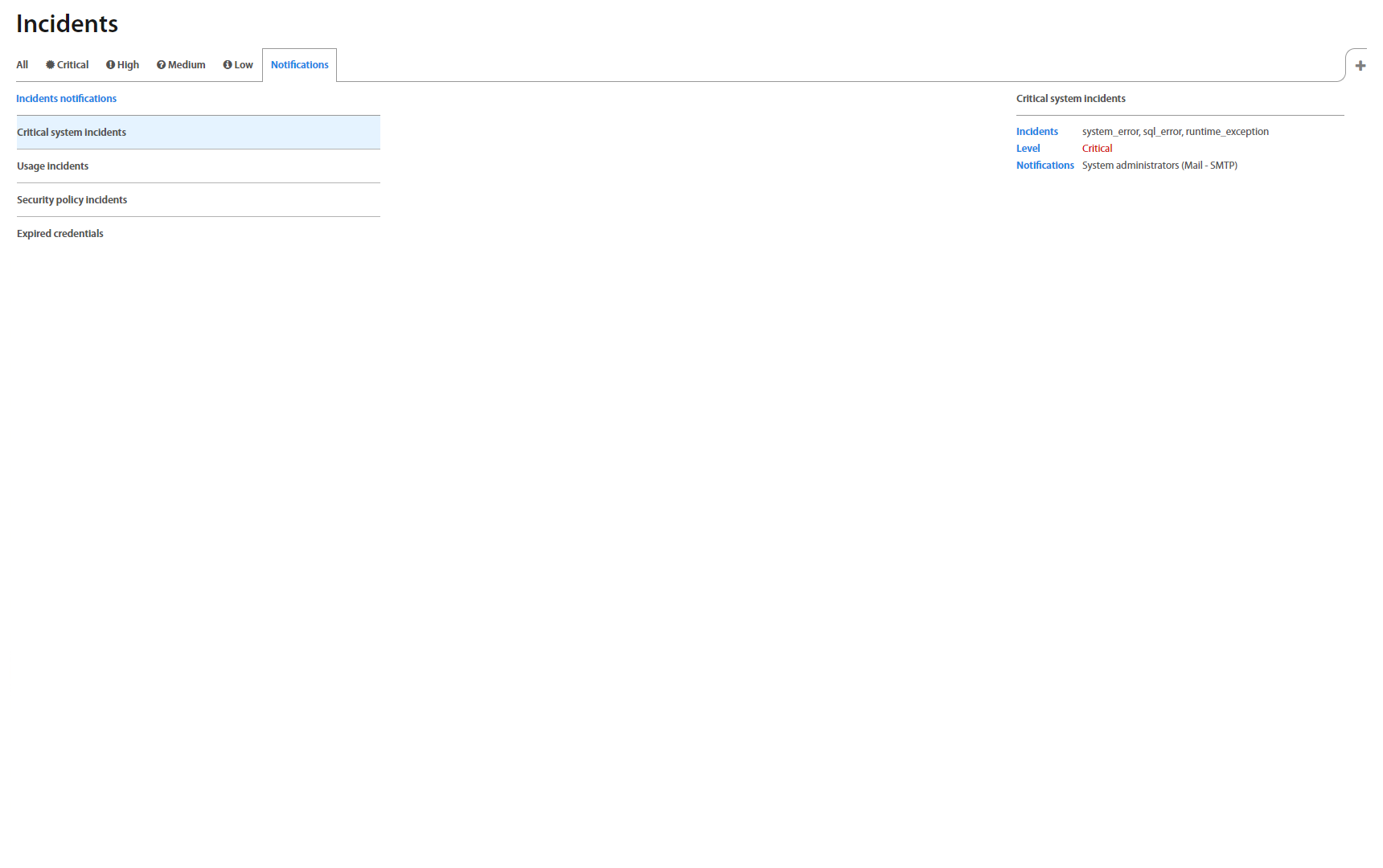
To show Incident notification’s detail, click on the specific row and detail shows up on the right side.
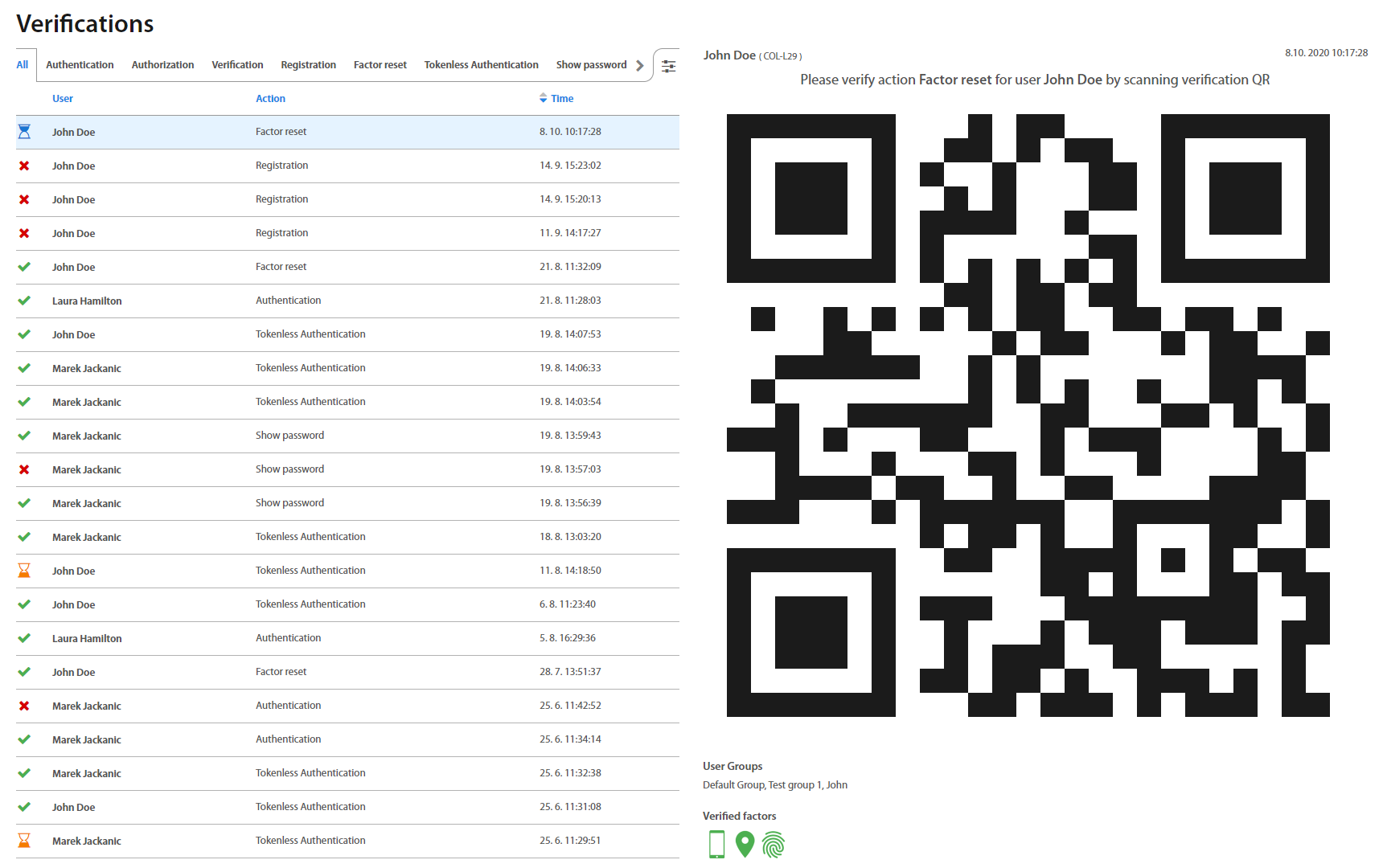
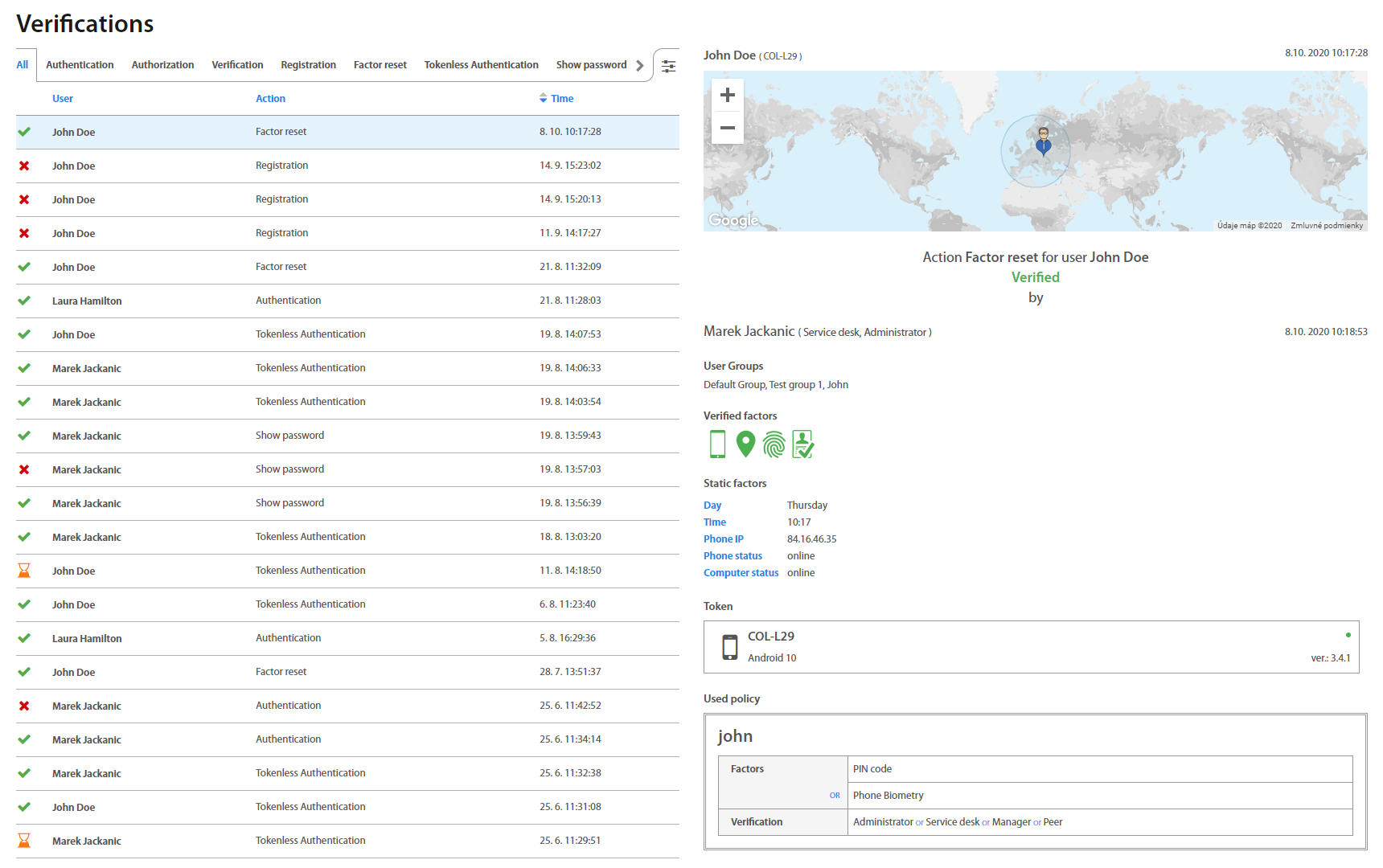
Verifications¶
Verifications page lists all verifications that happened or are currently happening in Excalibur, as well as categorizes them into tabs based on a type of Action they are associated with.
Info
By clicking on an individual verification, detailed information with GPS location shows up.
Geofences¶
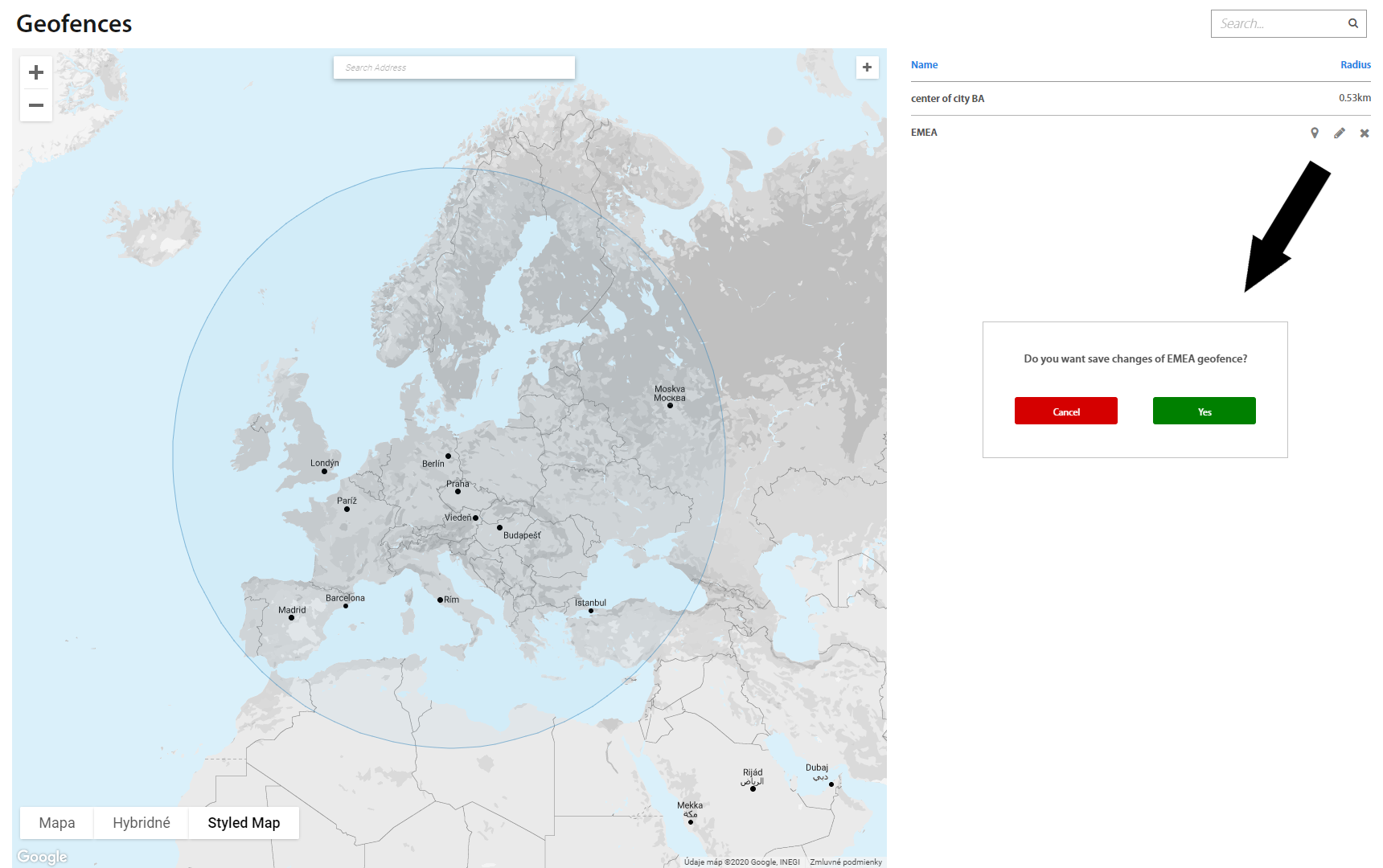
Geofences page serves to manage existing and create new geofences in Excalibur. In the top right corner, there’s a search of geofences based on their names, below it is a list of all geofences. Selected geofence always appears on the map.
Edit geofence
Rename geofence
Remove geofence
It’s also possible to Edit, Rename and Remove existing geofences as needed. Editing means moving a selected geofence around the map by dragging it where it’s desired or scaling it by dragging the circle by its rim. Once done, click outside the geofence circle and confirm changes. All new settings of geofence may to be authorized by token /it depend by security policy/. Administrator authorizes this action by confirming push notification which is received on token or scans QR code with token.
It’s also possible to Edit, Rename and Remove existing geofences by right clicking on the geofence circle and select option.
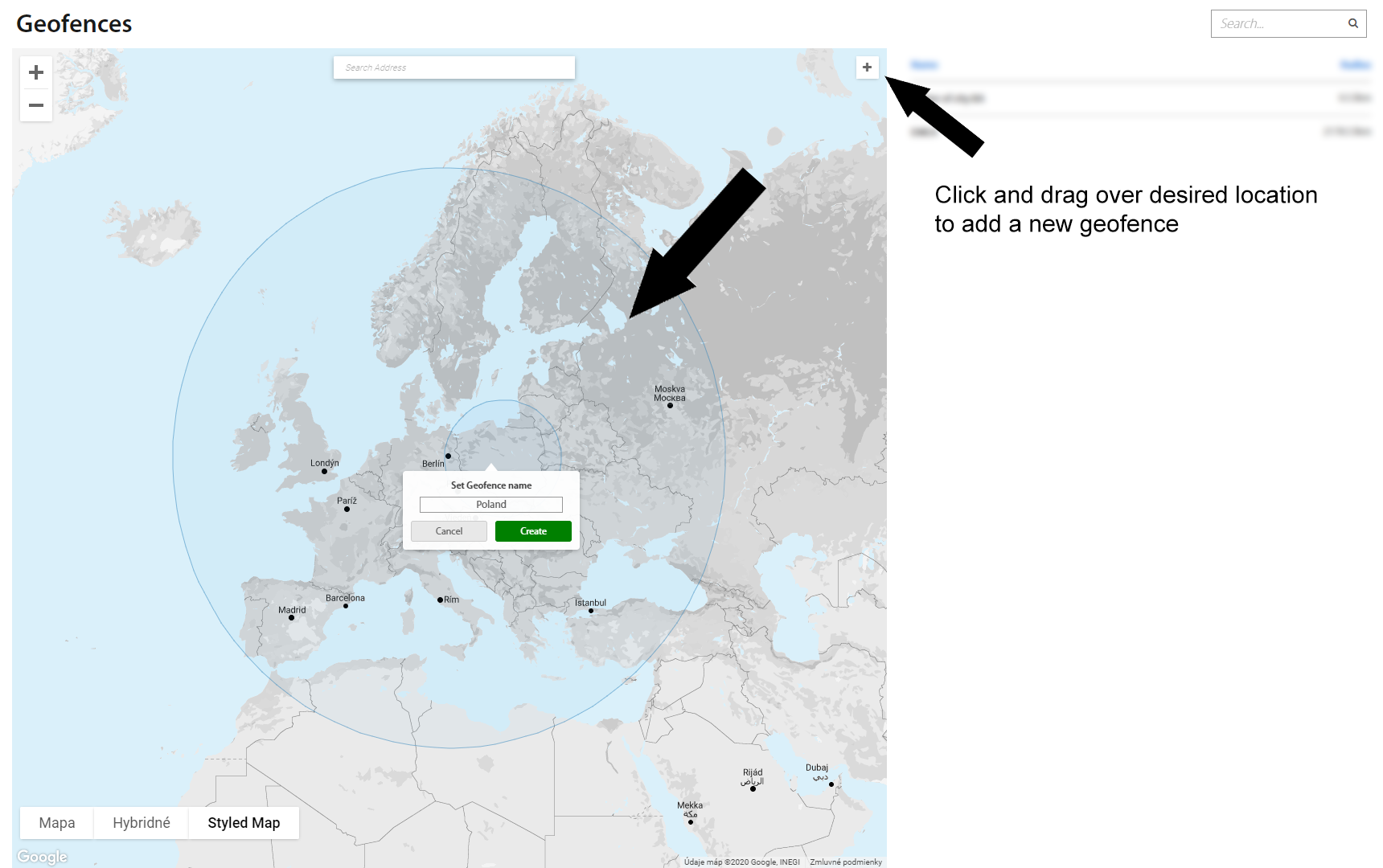
By clicking on “+” plus button, a new geofence can be added to the current (desired) location.
To create a new geofence, click on the desired location on the map and drag a mouse scale the circle. Once the circle covers a desired area, set a geofence name and click the “Create” button. New geofence will appear in the top right corner list of all geofences.
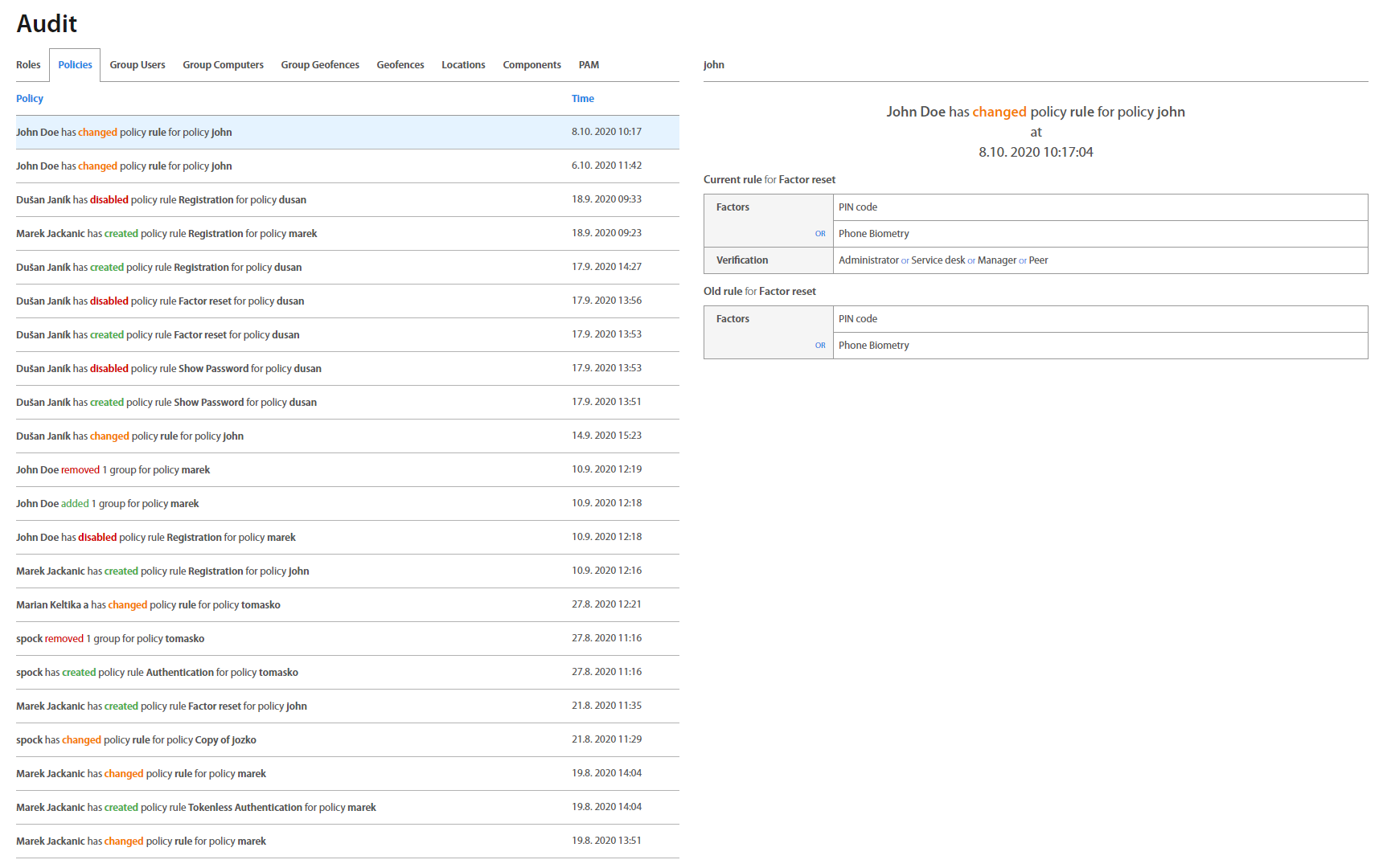
Audit¶
Audit page is a special view available only for Auditor and Administrator roles. It’s designed to provide a glanceable overview of all changes made by Administrators in Roles, Policies and Groups (Users, Computers, Geofences) in chronological order. Because the Auditor's role is designated for audit / review purposes of everything that happened in Excalibur, including changes which only Administrators can make, Auditors can see everything just as Administrators, but cannot change or take any action in the Dashboard.
Logger¶
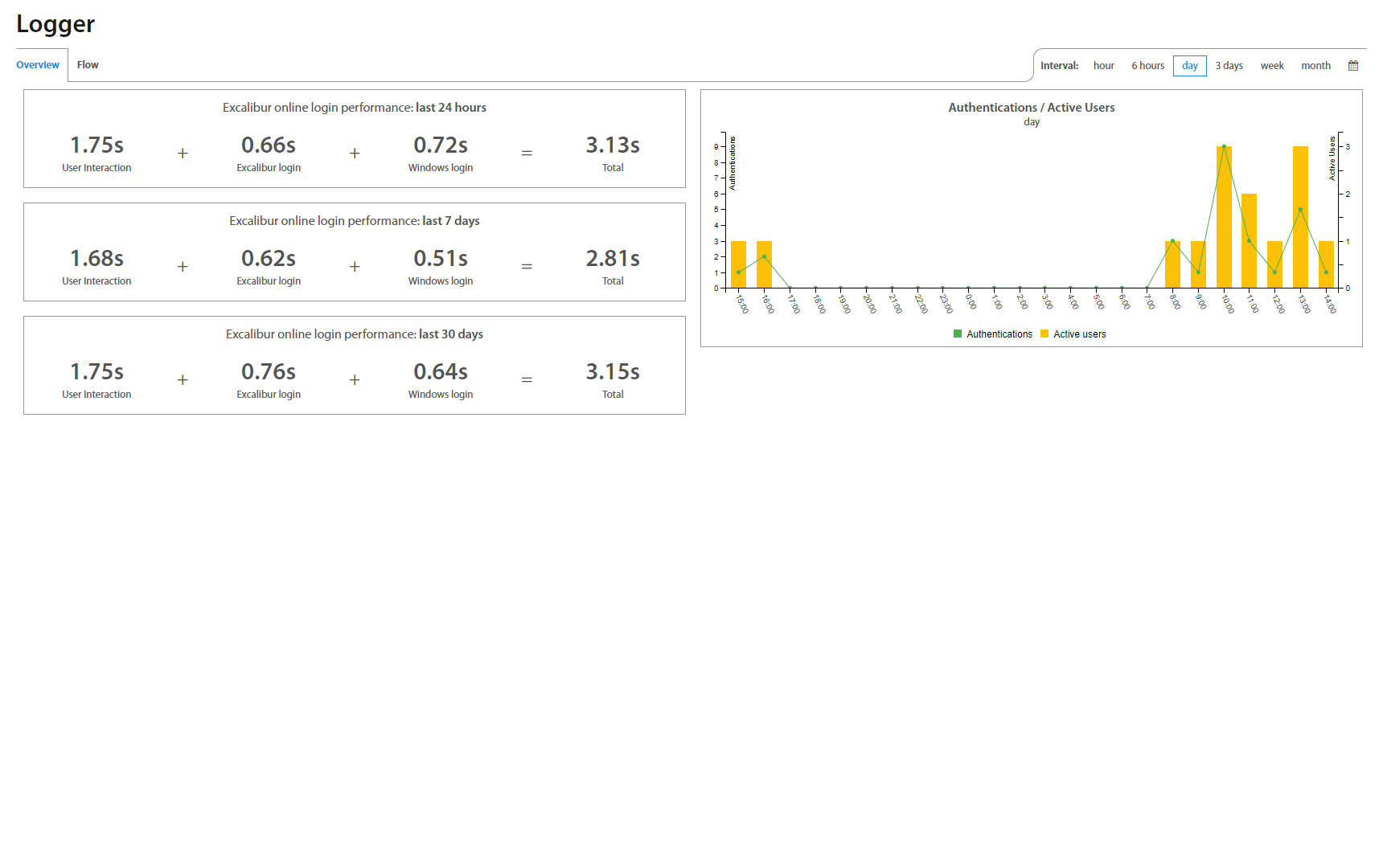
Logger tab provides information about each action of the user's token. To load all actions from the user's token is necessary to enable Usage & Diagnostics in the user’s token. Overview tab provides a preview of online login performance, amount of authentication and active users in the selected time interval which is located in the right top corner.
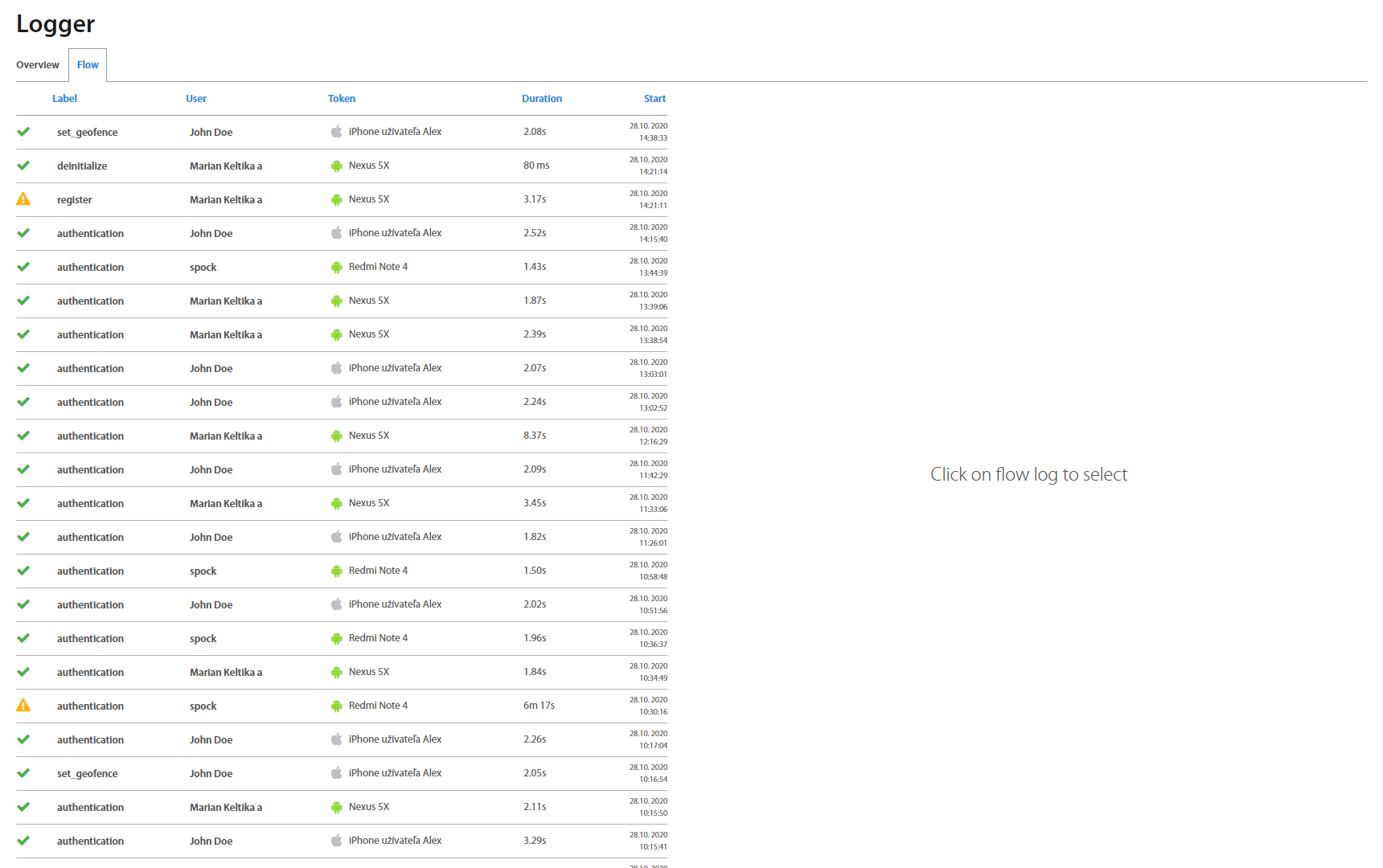
Flow tab lists all operations of tokens with their status and duration which have been performed by tokens and user interaction. By clicking on a specific row, further information on the right side shows up.
Status: - successful operation, - error, - warning, - timeouted
Label: Label of operation
User: Users’ name
Token: Name of token.
Duration: Duration of operation
Start: Date and time when operation started
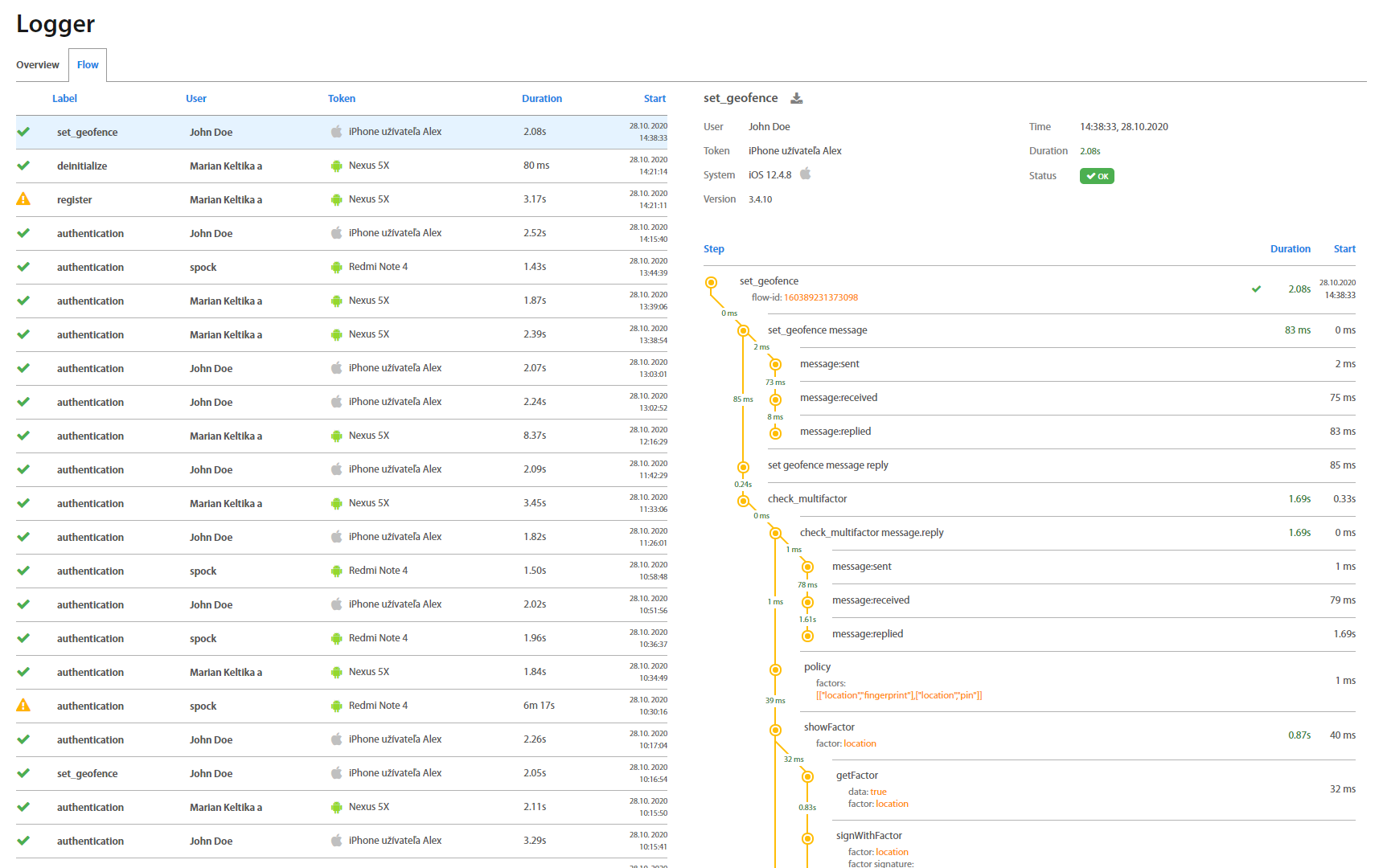
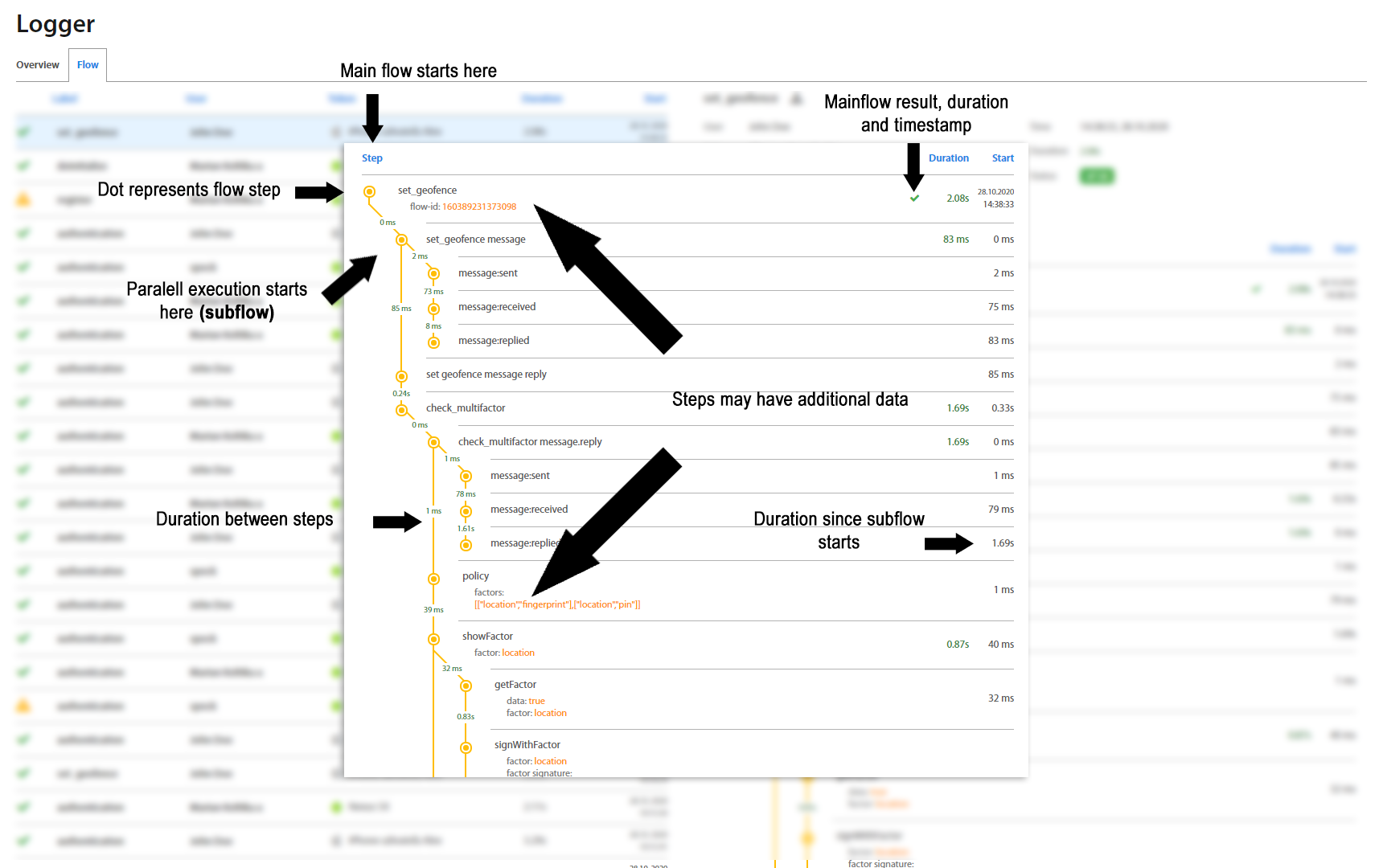
Most common interactions with Logger are analyzing action flows. Those flows are represented by flow graphs displayed in detail window after selecting specific flow in main window. Detail window for selected flow consists of areas listed below.
-
Flow Summarization - shows summarization for current action flow (duration, status, system information, …)
-
Flow Graph - graphical representation of current action flow (detailed in Flow Graph section).
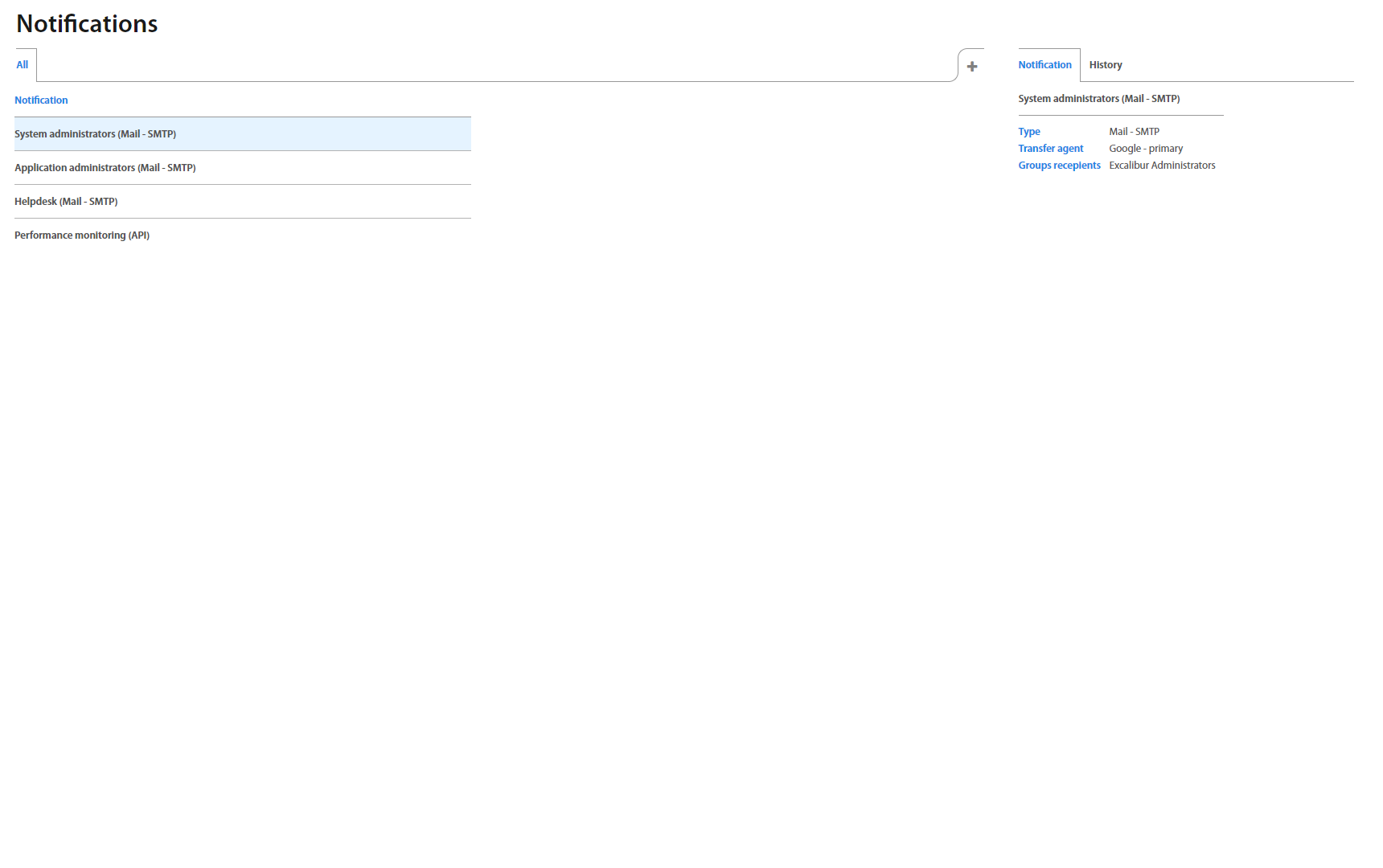
Notifications /In Progress/¶
Configuration for sending email consists of following steps:
- Create SMTP configuration used for sending emails - Chapter Configurations
2. Create notification definition, which includes recipients (group of users) - Chapter Notification
3. Create incident notification where you specify which incidents will trigger appropriate notification - Chapter Incidents: Notifications
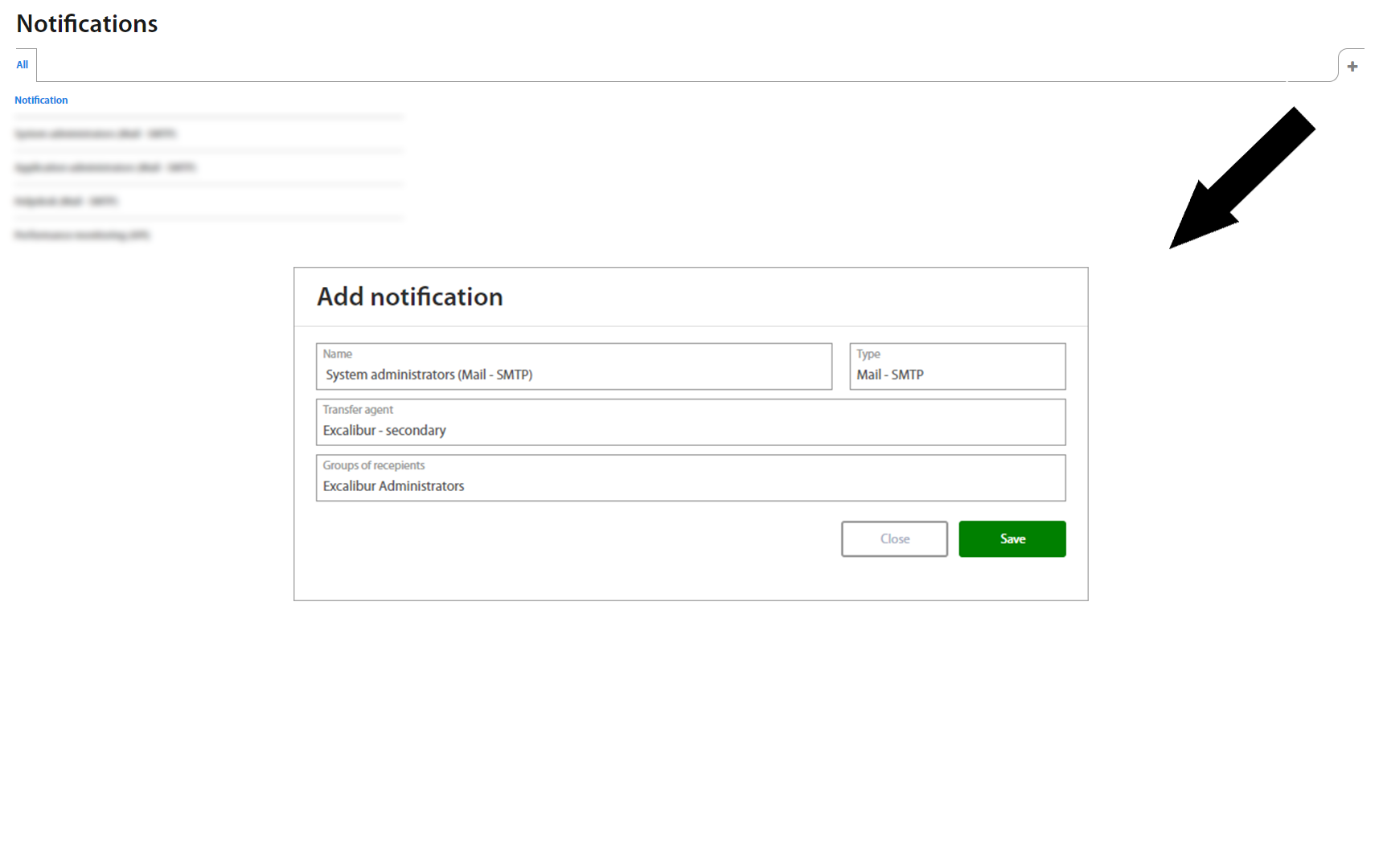
Notifications allow you to create a connection for sending email notifications to the User group. To create a connection, click on the + button and define required fields:
| Field | Description |
|---|---|
| Name | Name of the connection. |
| Transfer agent | Select SMTP server created in Configuration part. |
| Groups of recipients | Select a User group for which the email notifications will sent - email is read from the AD account of the given user thus doesn’t need to be manually specified. |
To show Notification’s detail click on the specific row and detail shows up on the right side.
History tab shows a list of email notifications sent.
Status¶
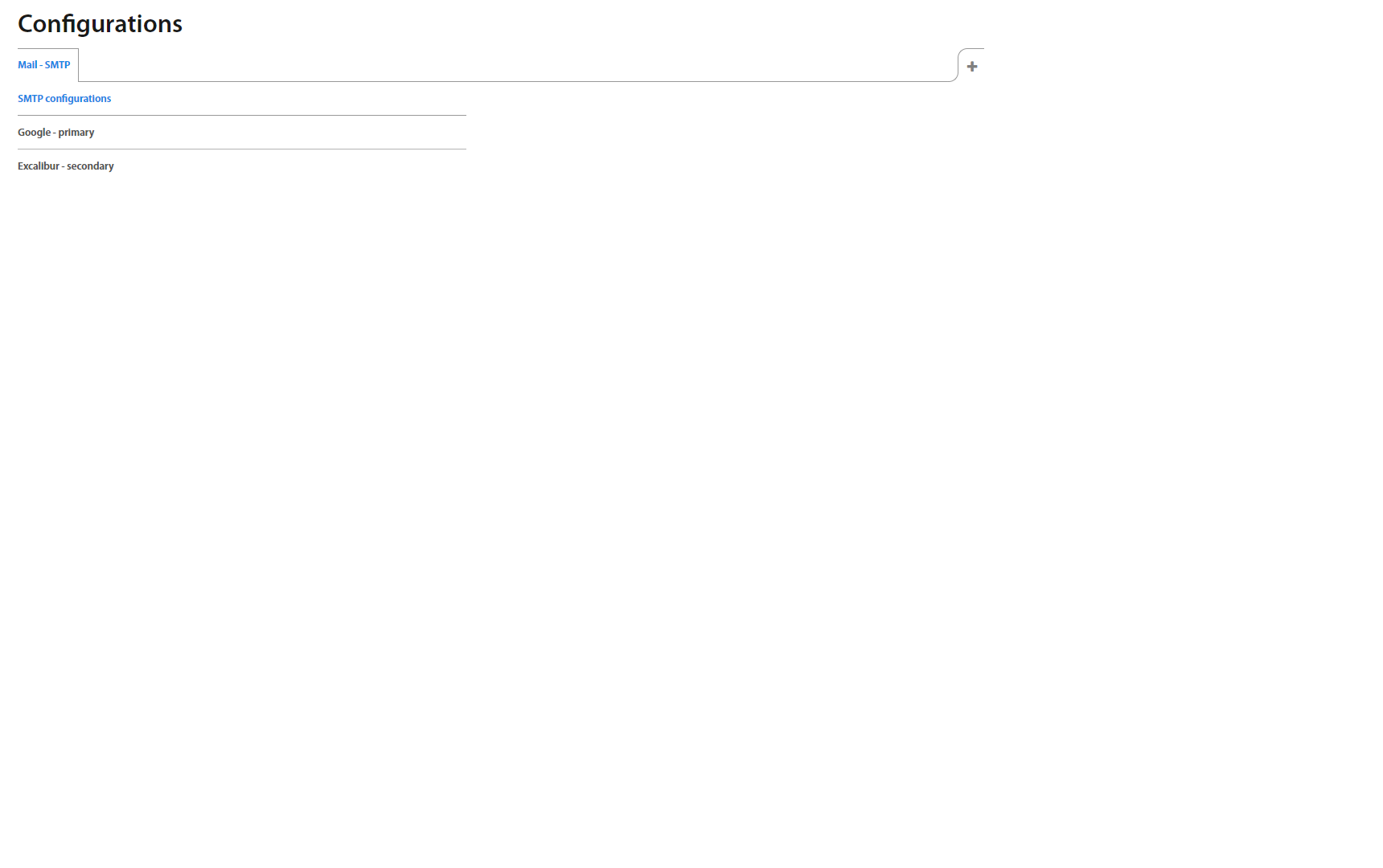
Configuration /In Progress/¶
Configuration for sending email consists of following steps:
1. Create SMTP configuration used for sending emails - Chapter Configurations
2. Create notification definition, which includes recipients (group of users) - Chapter Notification
3. Create incident notification where you specify which incidents will trigger appropriate notification - Chapter Incidents: Notifications
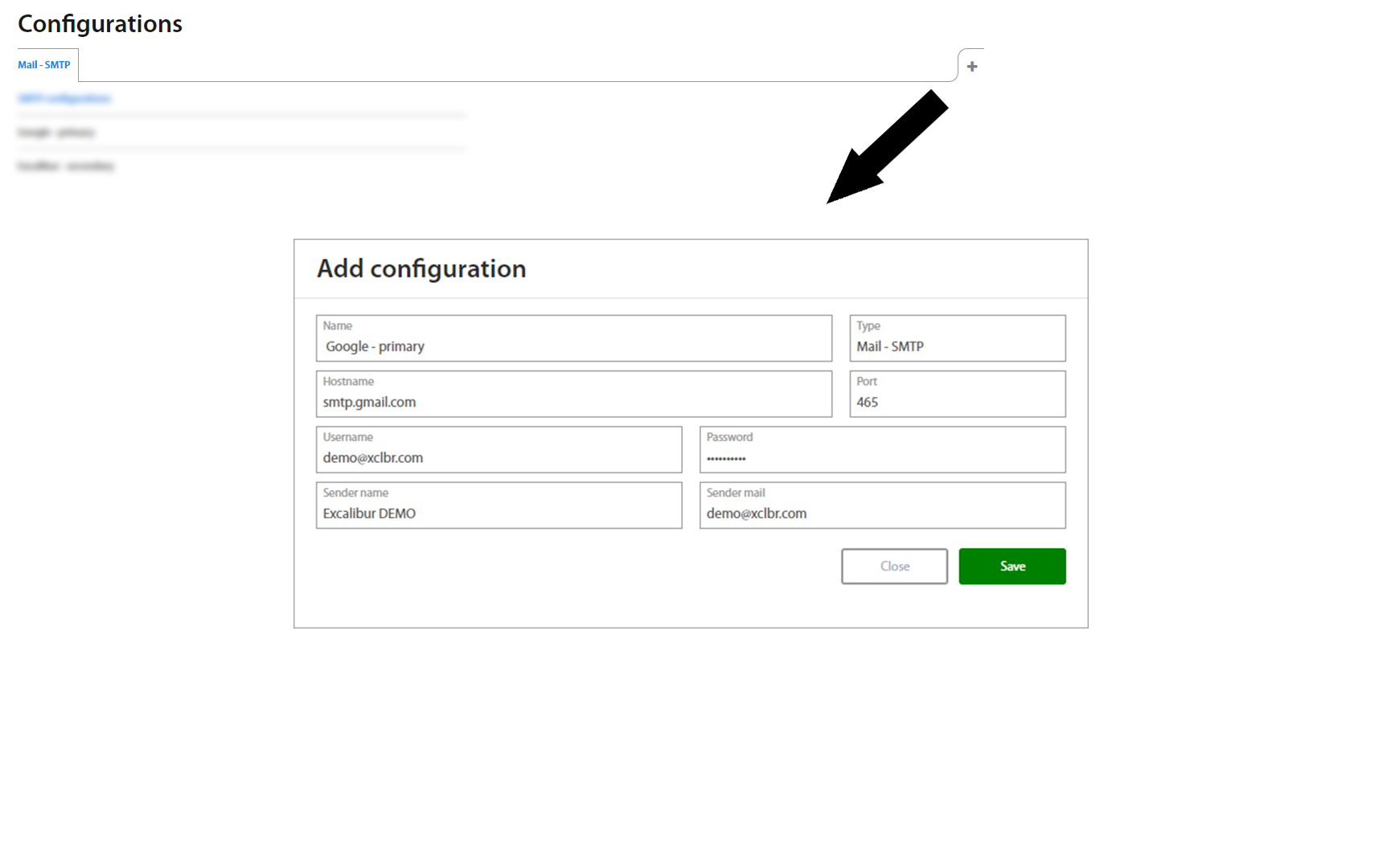
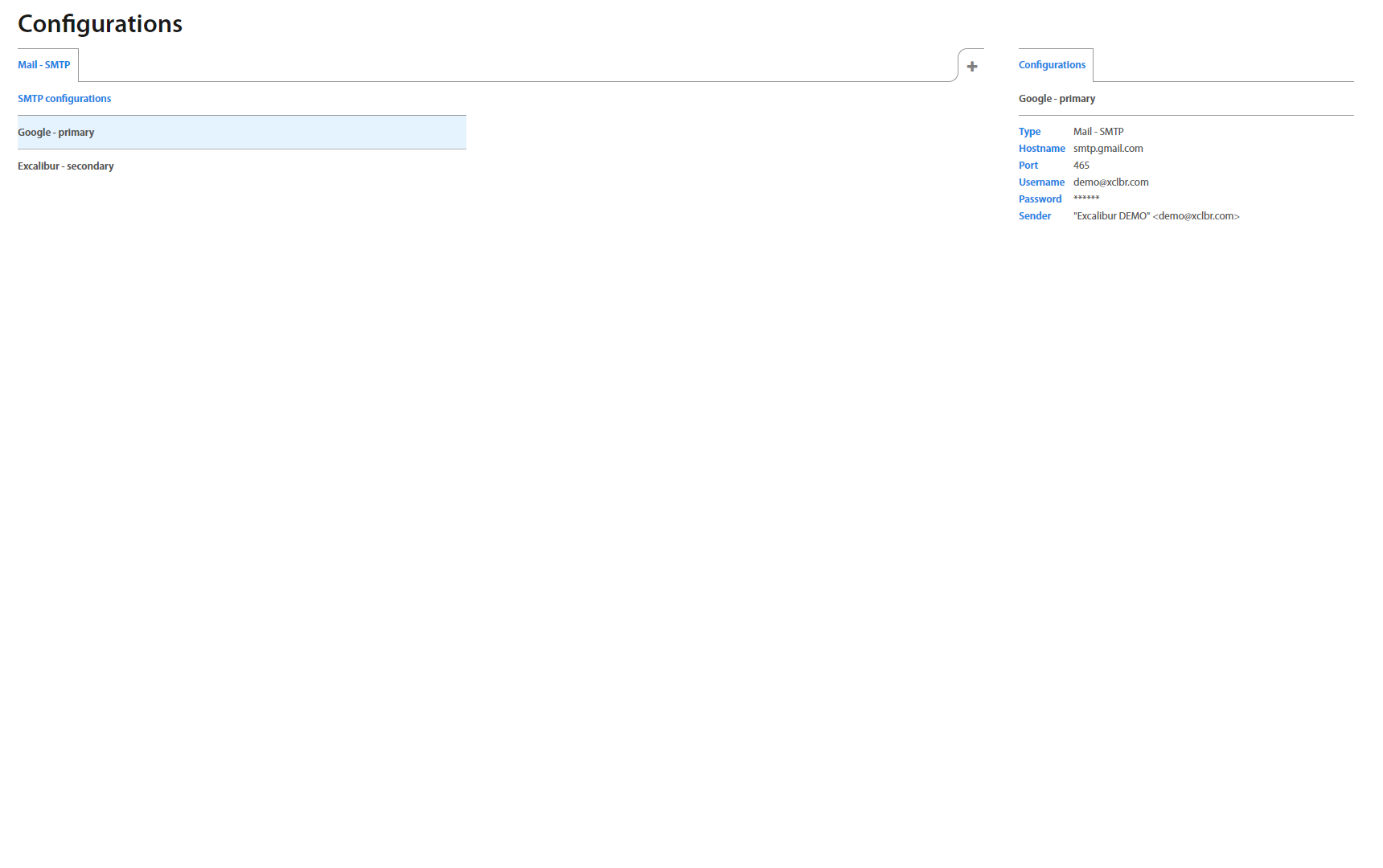
To configure SMTP server click on the + button and fill the required fields:
| Field | Description |
|---|---|
| Name | Name of the SMTP server. |
| Hostname | IP or hostname. |
| Port | Range 0-65535 |
| Username and Password | Credentials to authenticate SMTP client to the server. |
| Sender name | Name of sender who sent. |
| Sender mail | Email address from where the mail will sent. |
To show detail of the SMTP server, click on the specific server and detail shows up on the right side
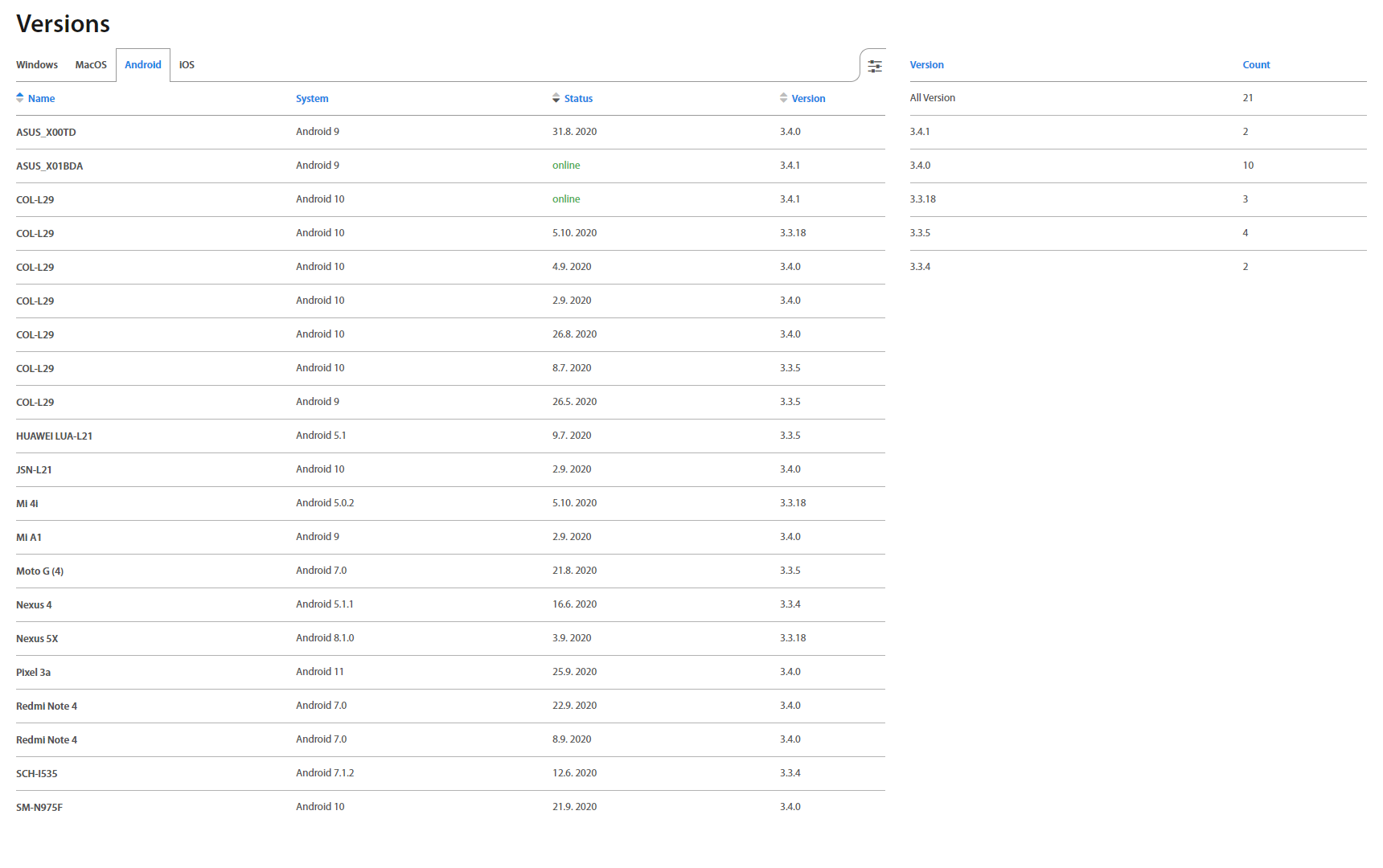
Versions¶
Versions page lists an Operating System (OS) version, Status and Excalibur version (version of a respective component) of every device in Excalibur ecosystem, as well as a summary of all versions currently used.
Versions are divided into tabs by OS.
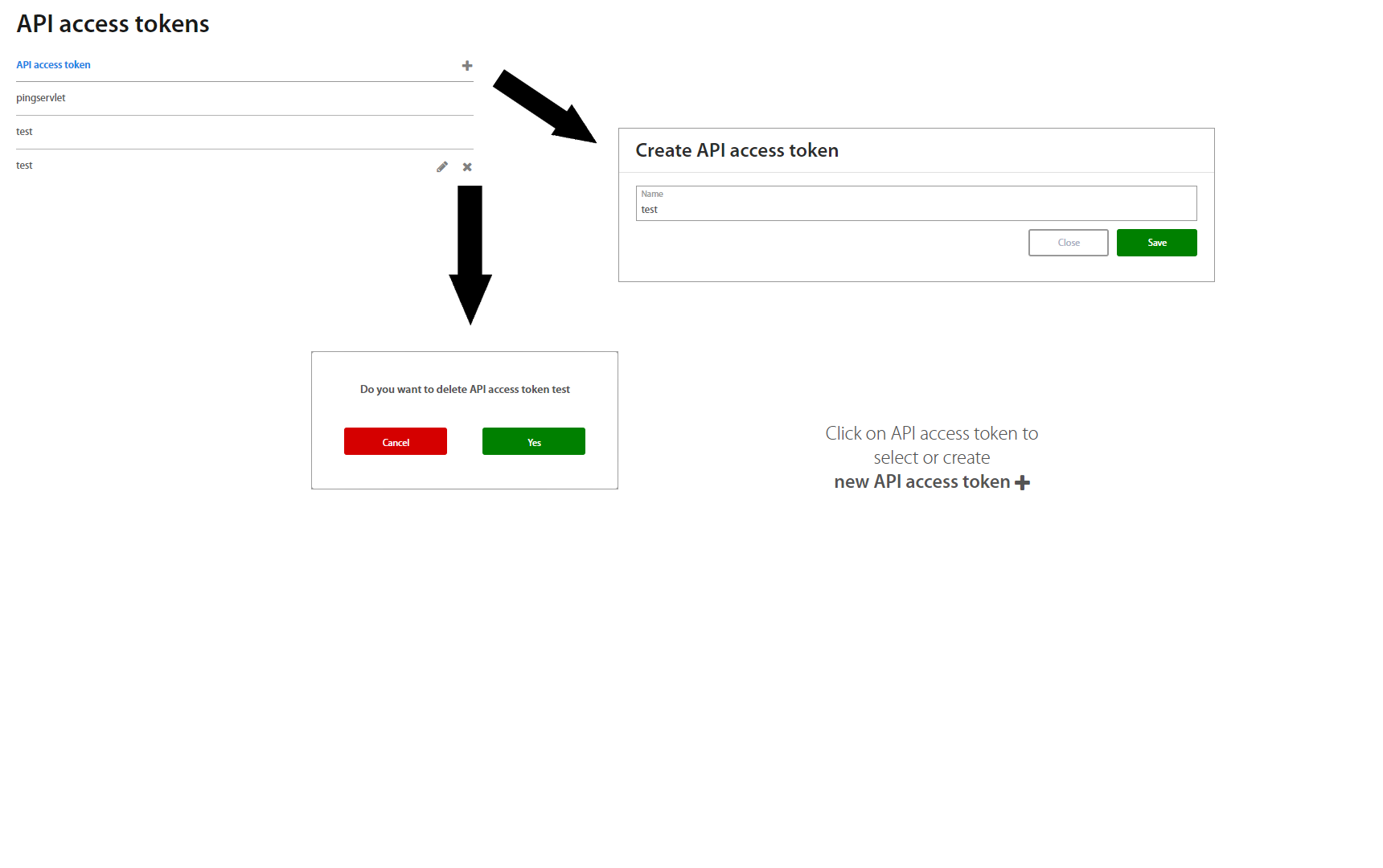
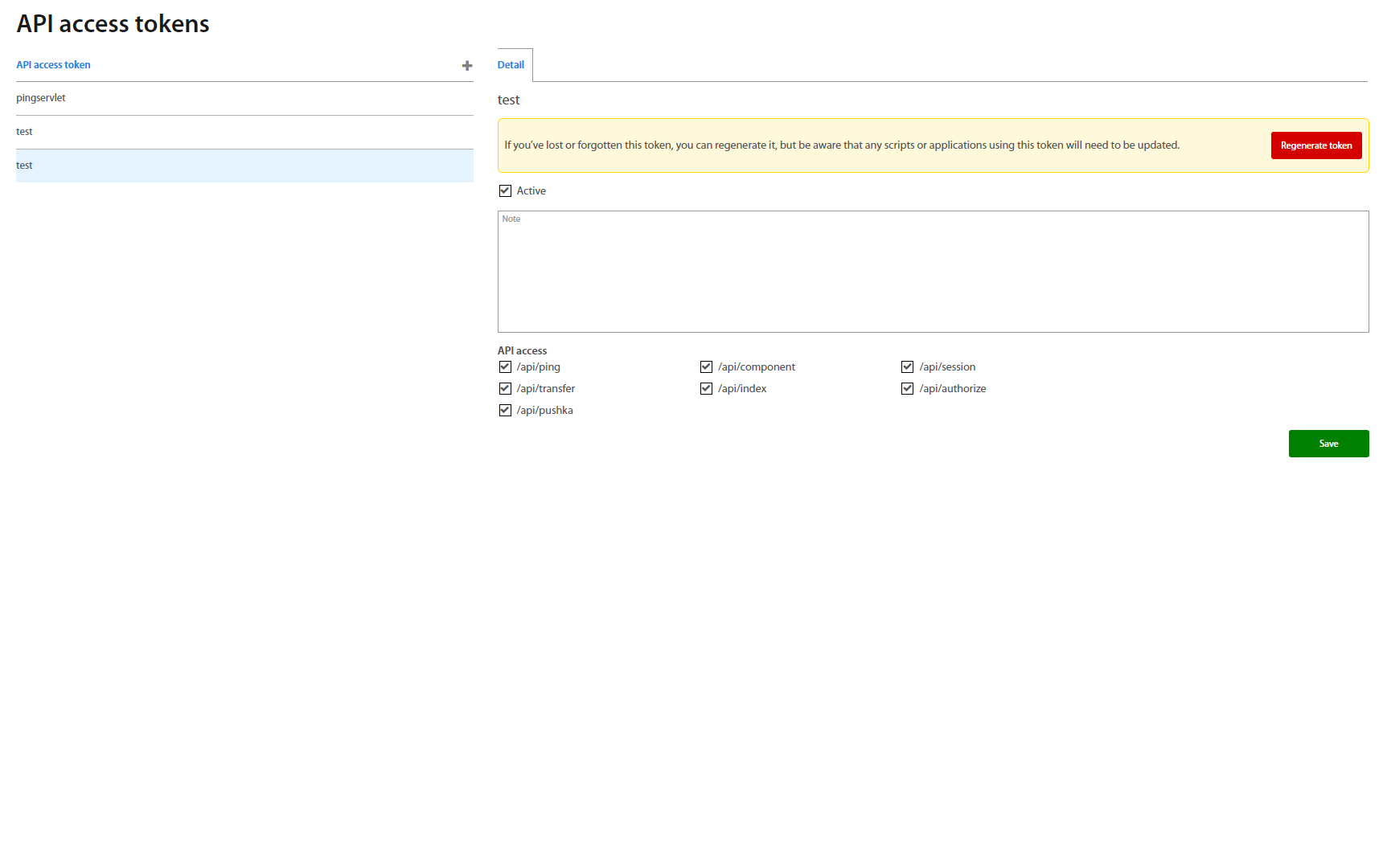
API Access Tokens¶
API access token serves to create API calls for external software. Click on the “+” button and fill the name of the new API call. By clicking on spcific row, the detail of API call is shown
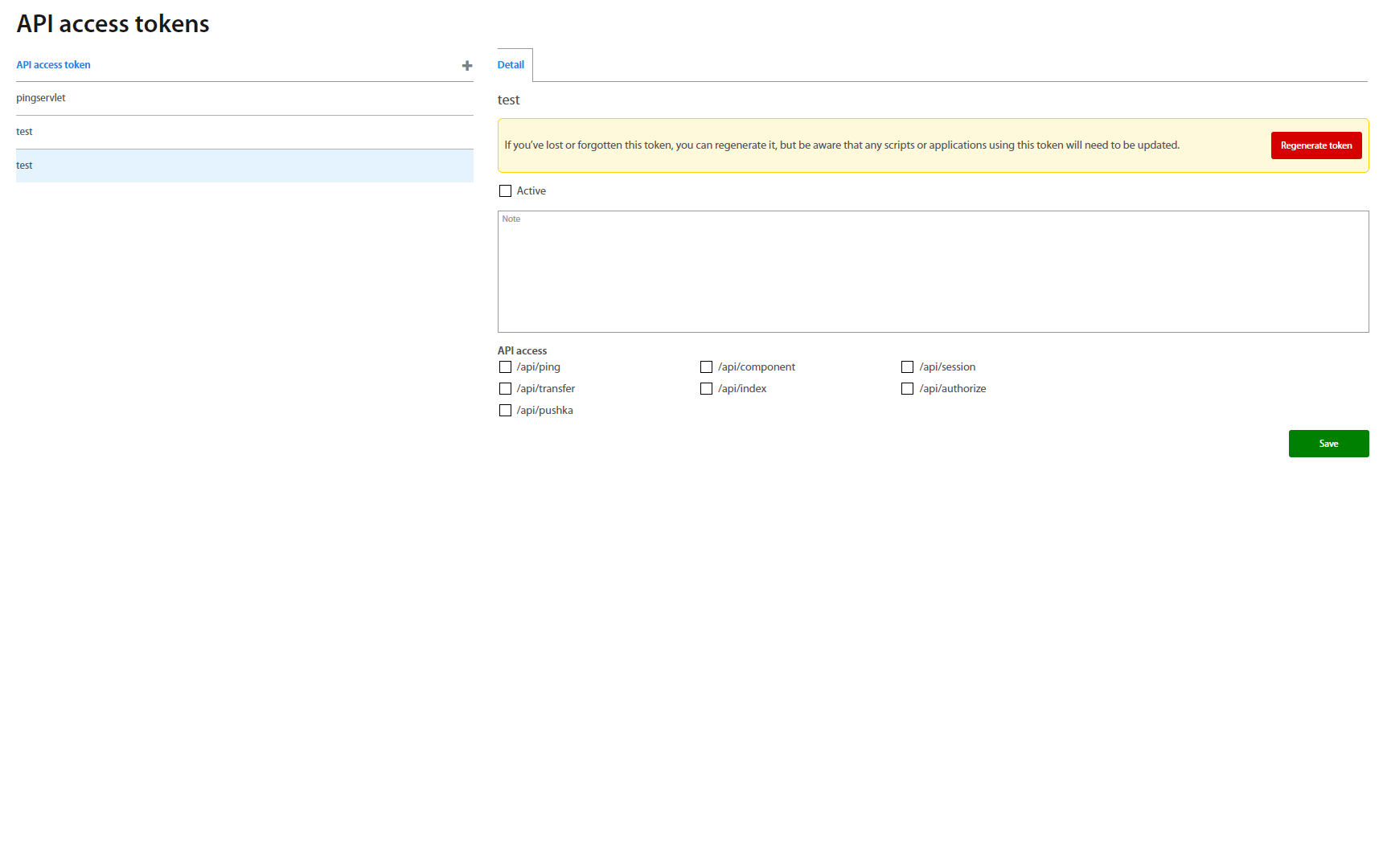
Detail of calls consist of three parts:
-
Hash chain generating
-
Notes
-
API Access
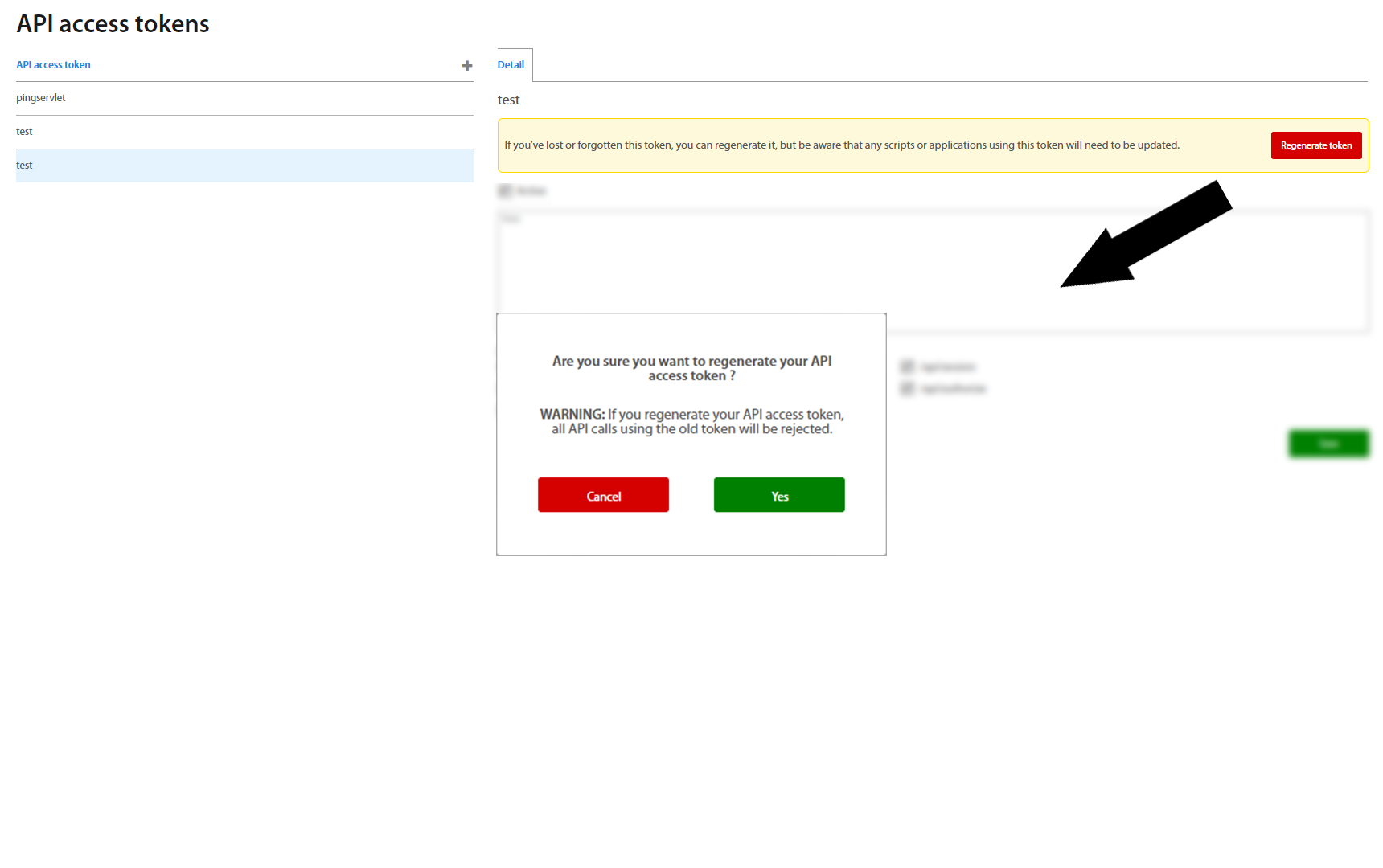
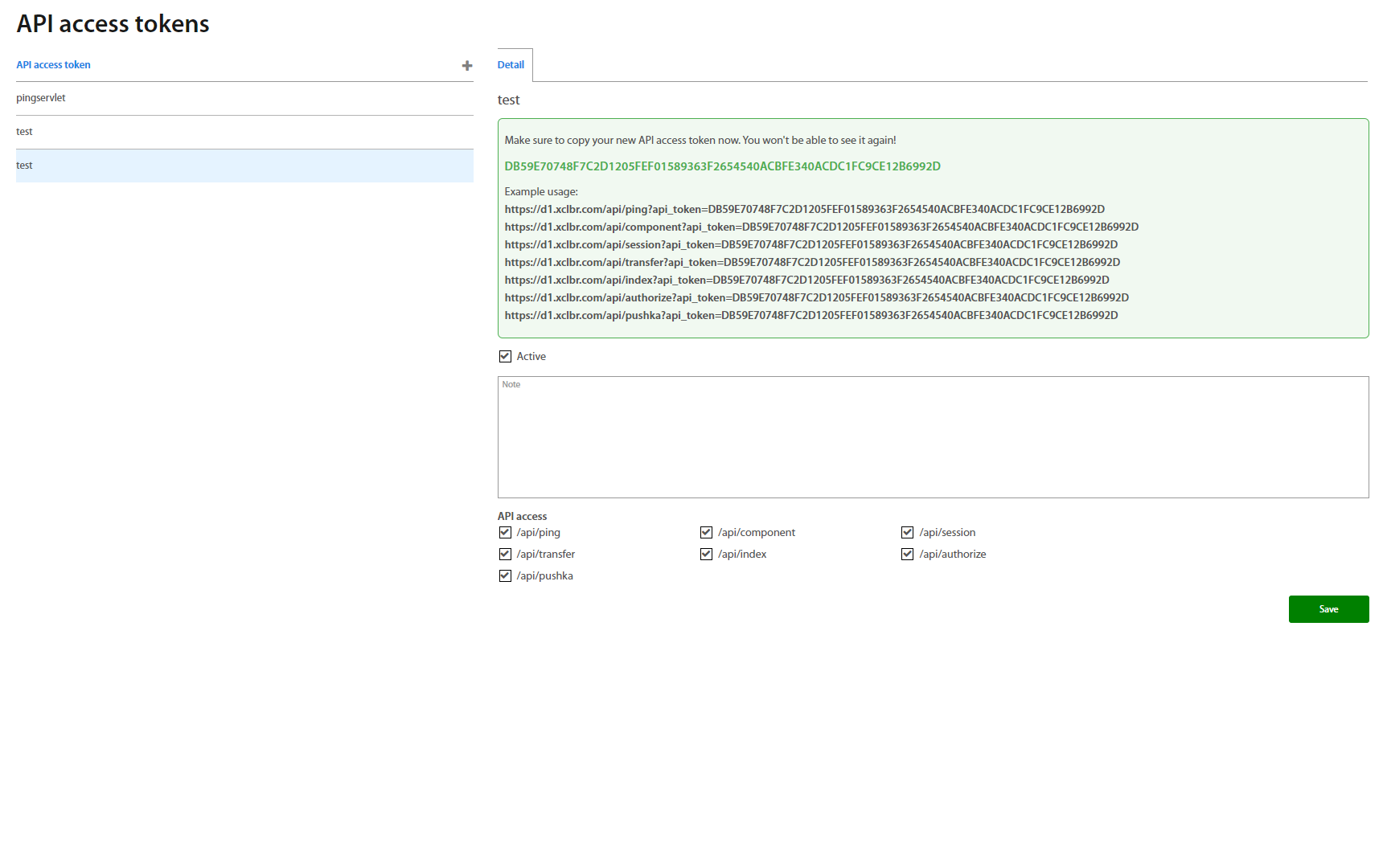
Select the API access which you want to use and click on the Regenerate token button to generate the new hash chain. Please save it to another place because hash is not shown the next time. On the next Regenerate token the hash is changed. Examples of usage of hash chain for API calls are shown below. By checking Active field you activate access.
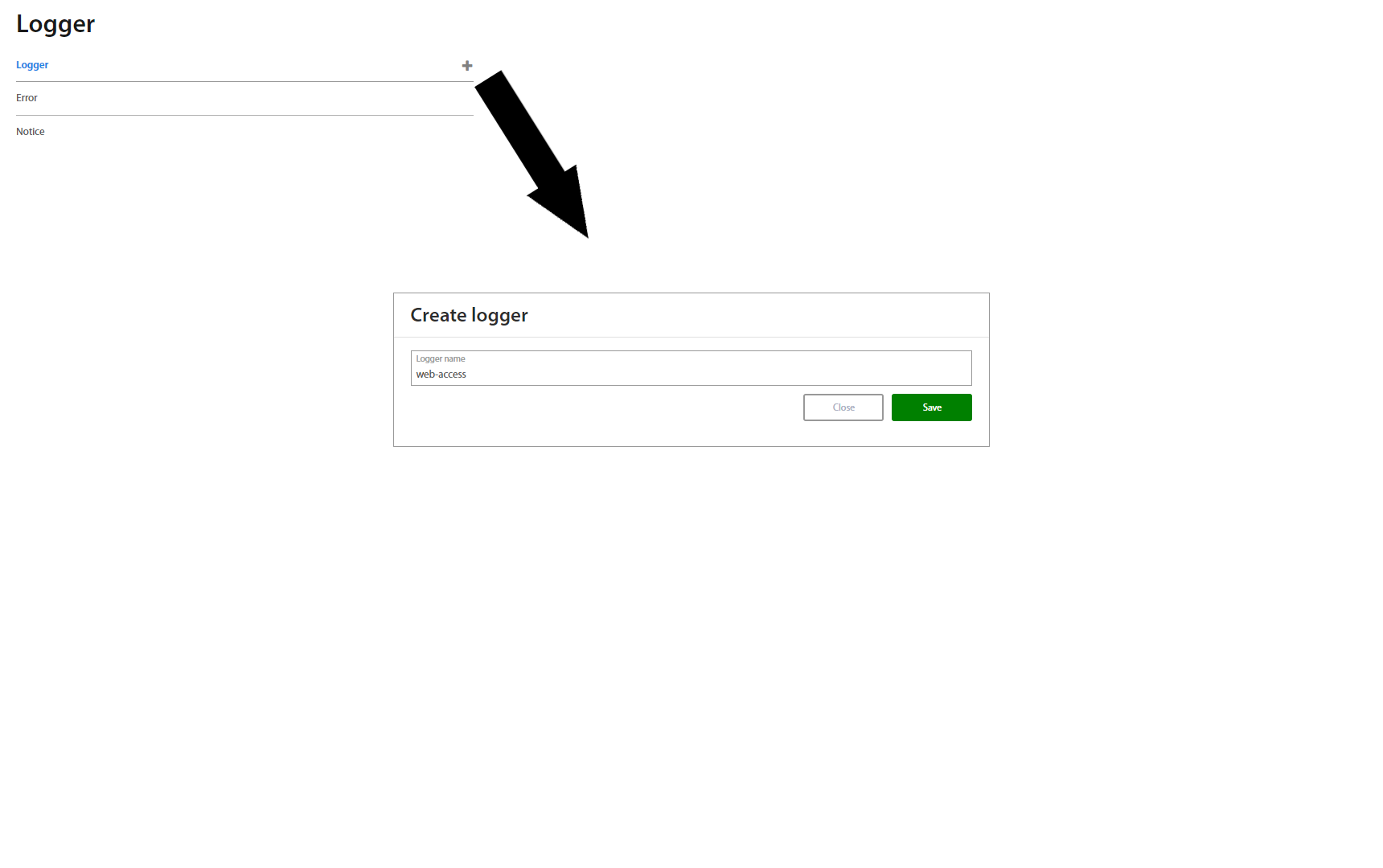
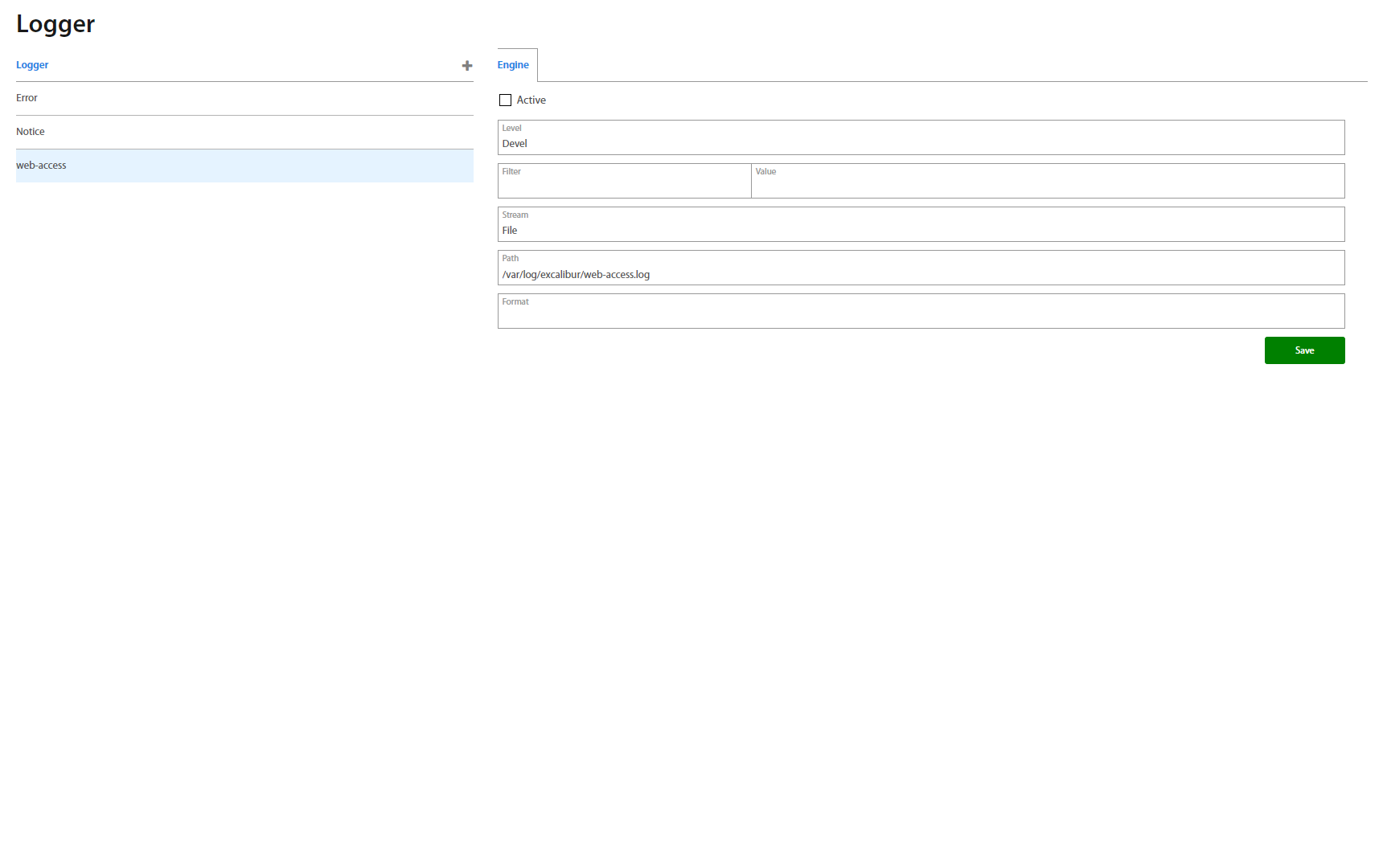
Syslog¶
Syslog is a tool which provides recording of logs which have occured. To add a new Logger type, click on the “+” button, and type the name of the Logger and save it. If it is necessary to delete or rename the Syslog, click on “” or button and make the changes or delete it. Syslog can be set up for all Levels of logs and Logs are filtered by Value. Change of log level is posssible without Server restart. Logs can be saved and exported in file to selected path.