Security Policies Management¶
Policies and Factors¶
Policy is a set of rules specified for an action performed by Excalibur User which needs to be fulfilled to allow the action. Policy can specify which factors need to be provided by the user, allows the action to be performed just on some subset of clients, inside specified set of geofences, and / or at the right time and day of the week.
Policies can contain any of the following rules and their combinations:
- Factors
- Fingerprint
- PIN
- Geofences - subset of geofences where user must be physically located to perform the action
- Clients - subset of clients on which the action is allowed to be performed
- Time of day
- Day of week
- IP address of the client
- IP address for the token
- Additional verification by Manager / Peer / Service Desk / Administrator
- New geofence scope
- New geofence type
By default, Excalibur has predefined a Default policy which is assigned to each registered user.
Required steps to assign policy:
-
Create policy - Described in this document
-
Greate a User group with users - Described in Excalibur Administrator Dashboard Manual
-
Assign policy to User group - Described in this document
Security Policies Management¶
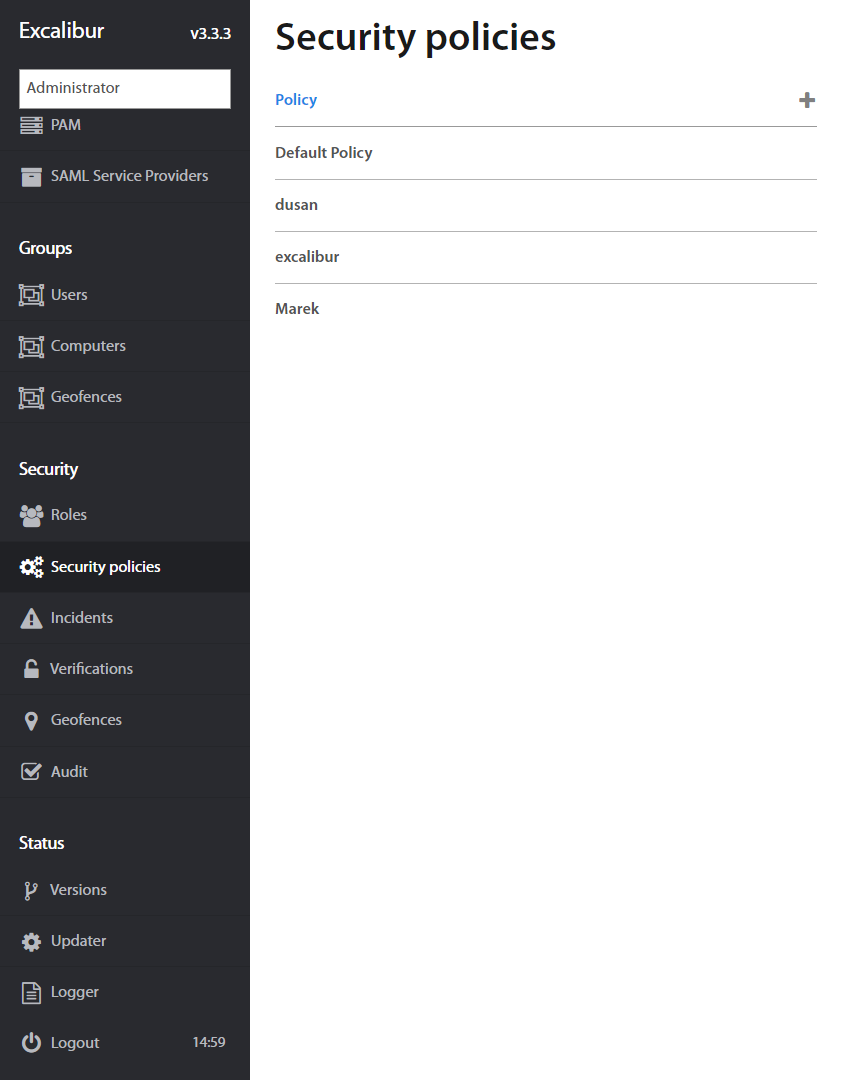
Administrator may view, add or edit existing Security policies from Excalibur Dashboard. Policies with Excalibur can be widely adjusted to assure the highest possible level of security with the best user experience for its users. For more information about Excalibur dashboard please refer to Excalibur Dashboard Administrator Manual.
Security policies section contains the list of all Excalibur Security policies in a company. Policies are listed by their names and by clicking on an individual policy detailed information shows up.
Warning
!!! Please be aware of manipulating by Security policies in Excalibur Dashboard. Any issues with Security policies may cause harm or possible security threats in your company !!!
Sections Summary¶
| Section | Description |
|---|---|
| Roles | List of all roles from the company's Active Directory. |
| Security policies | Page to view, edit, add or remove individual policies. |
| Incidents | Lists of all registered incidents in Excalibur. |
| Verifications | List of all verifications that happened or are currently happening in Excalibur. |
| Geofences | Page which serves to manage existing and create new geofences in Excalibur. |
| Audit | Page with changes which have occured. Audit is divided to Roles, Policies, PAM, Group users, Group computers, Group geofences, Geofences, Locations and Components. |
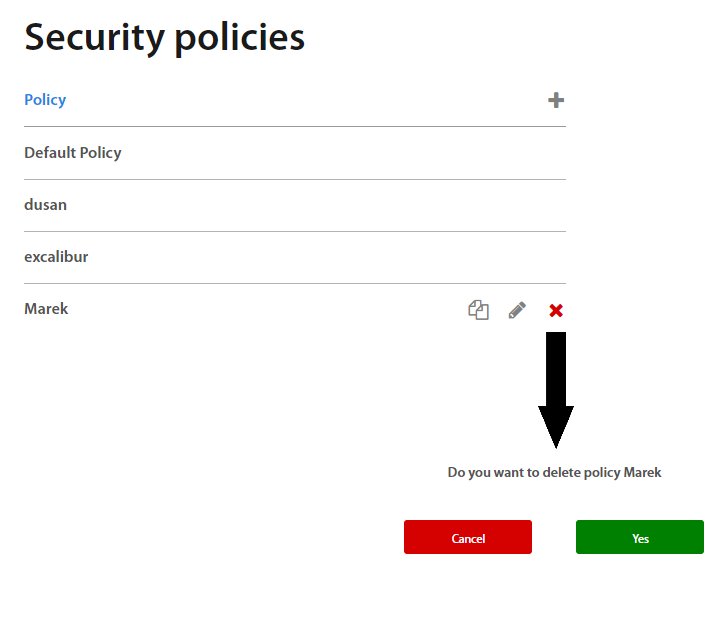
Removing existing Security policy¶
Administrator may remove any existing Security policy from the list of all policies. By hovering the mouse over policy x button will appear. Administrator is asked by clicking on the button to delete the selected policy.
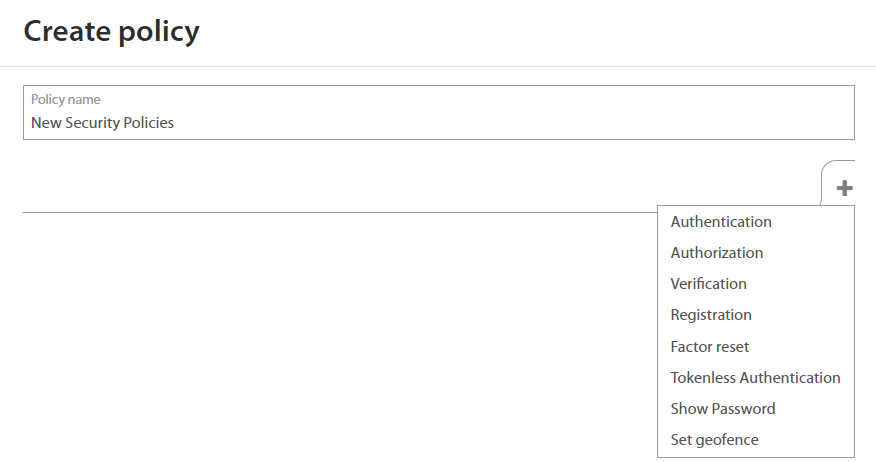
Adding new Security policy¶
Administrator may create new Security policy by clicking on the + button located at the top of the policies list. A new window with policy settings shows up.
Firstly, there is a need to fill Policy name which will be distinguished from others policies in a company. Once it is done Administrator can start with setting of desired policy by clicking on the + button.
Administrator can set different rules for Authentication, Authorization, Verification, Registration, Factor reset, Tokenless Authentication, Show Password or Set geofence. In case that any action doesn’t have a set of rules, then action is directed by default policy which is predefined by Excalibur. For more information about these Actions refer to Excalibur Administrator Dashboard Manual
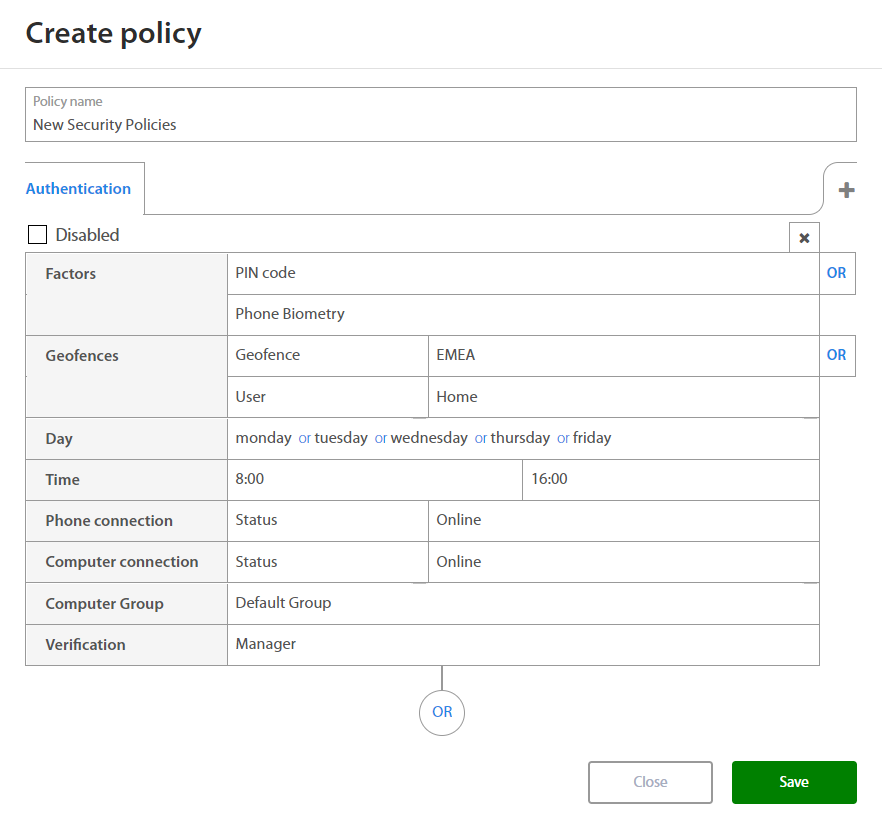
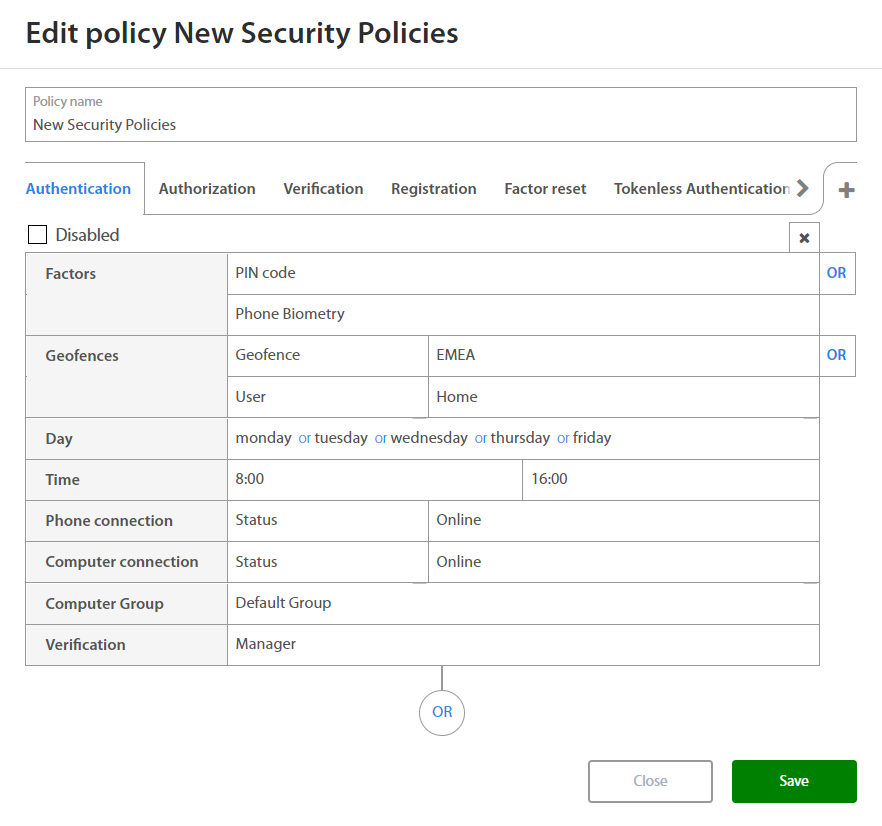
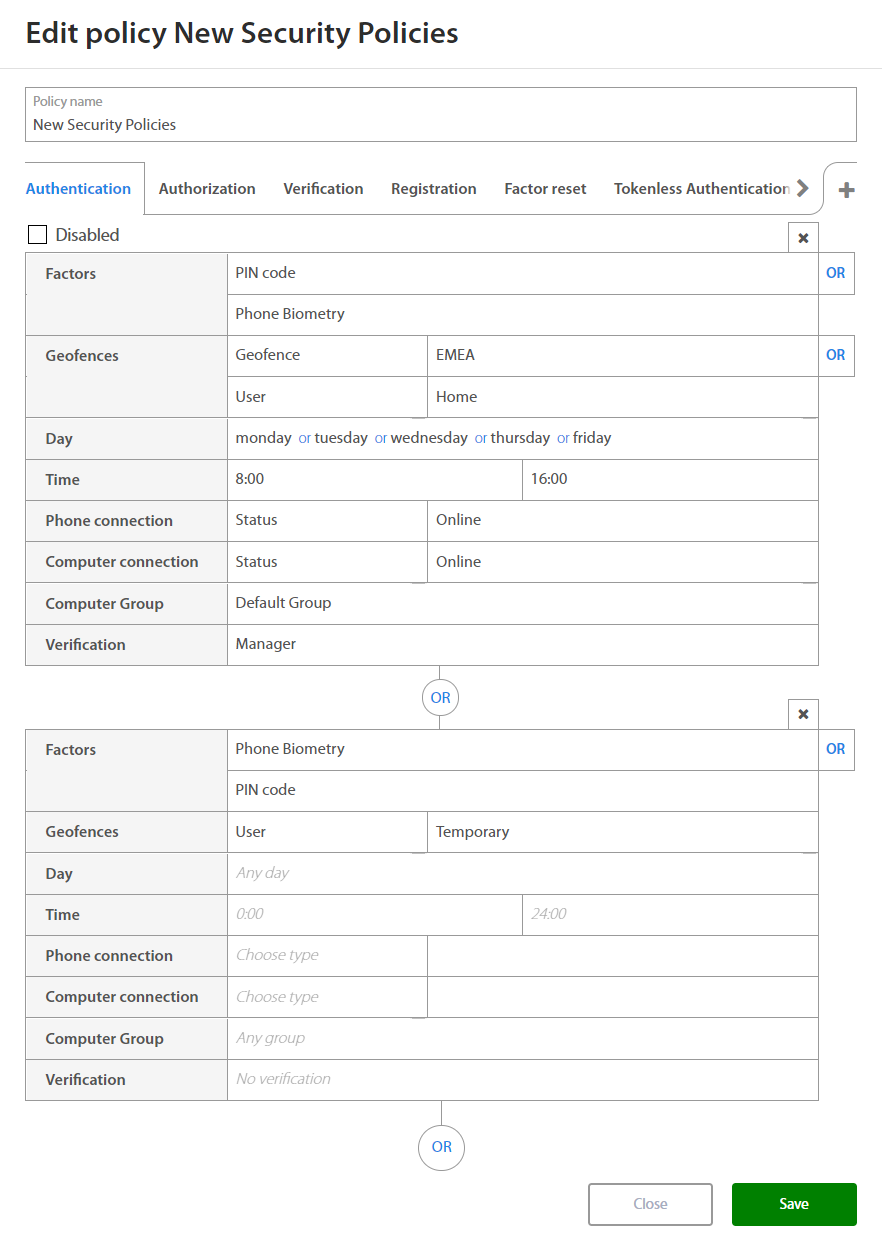
Authentication¶
When setting rules for new Authentication policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone connection | |
| Computer connection | |
| Computer Group | Select computer group where user can make action |
| Verification |
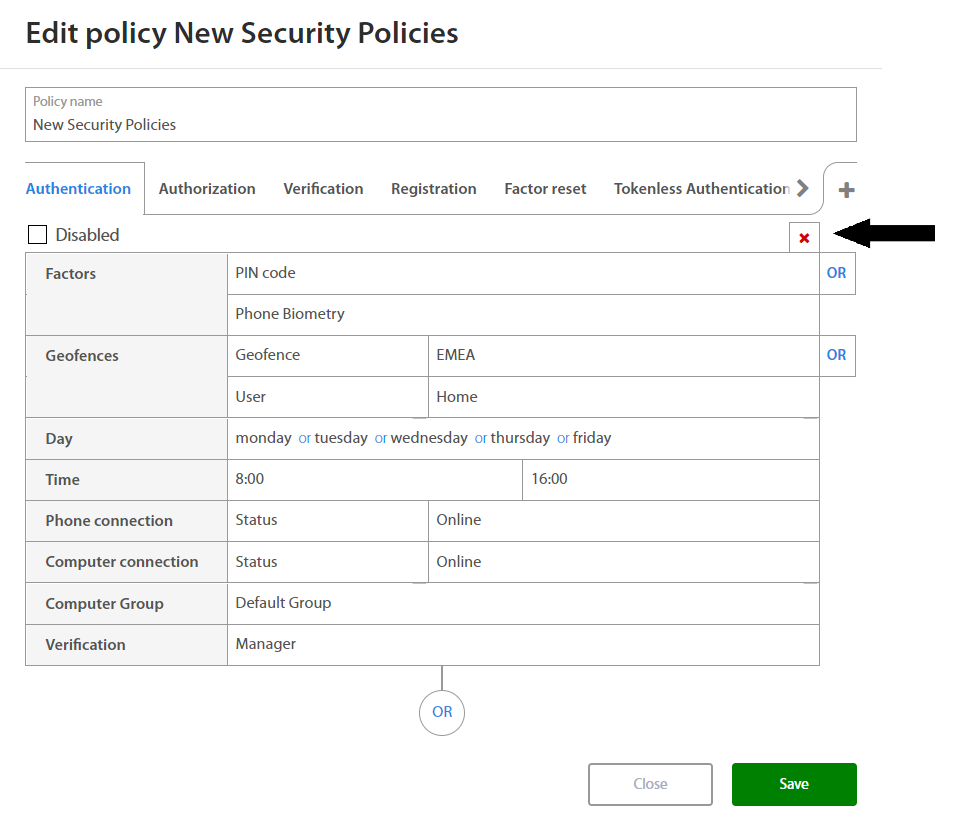
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
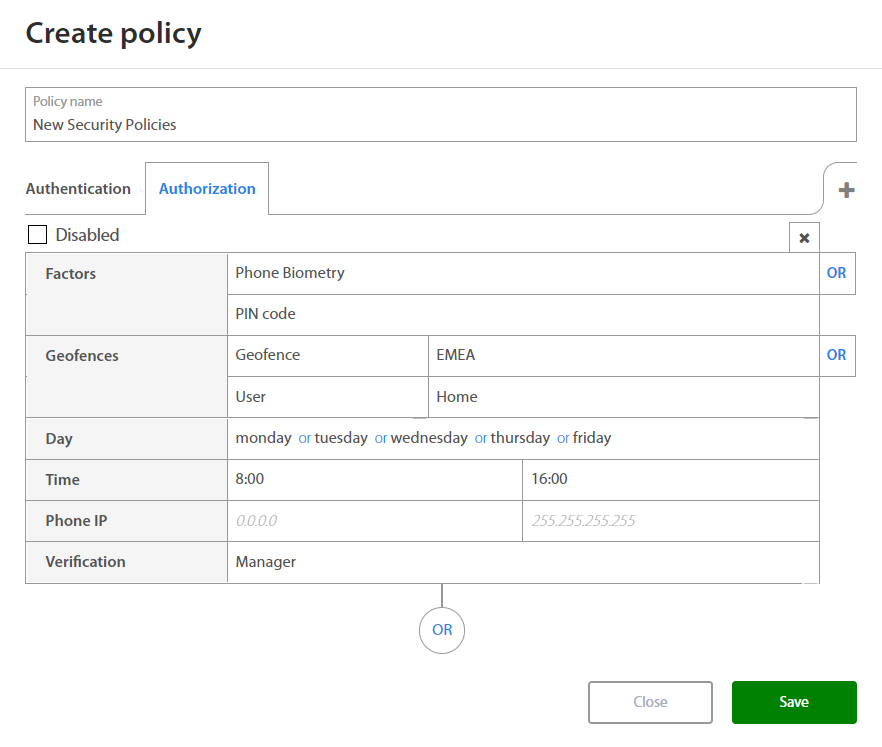
Authorization¶
When setting rules for new Authorization policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone IP | Set IP Range |
| Verification |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
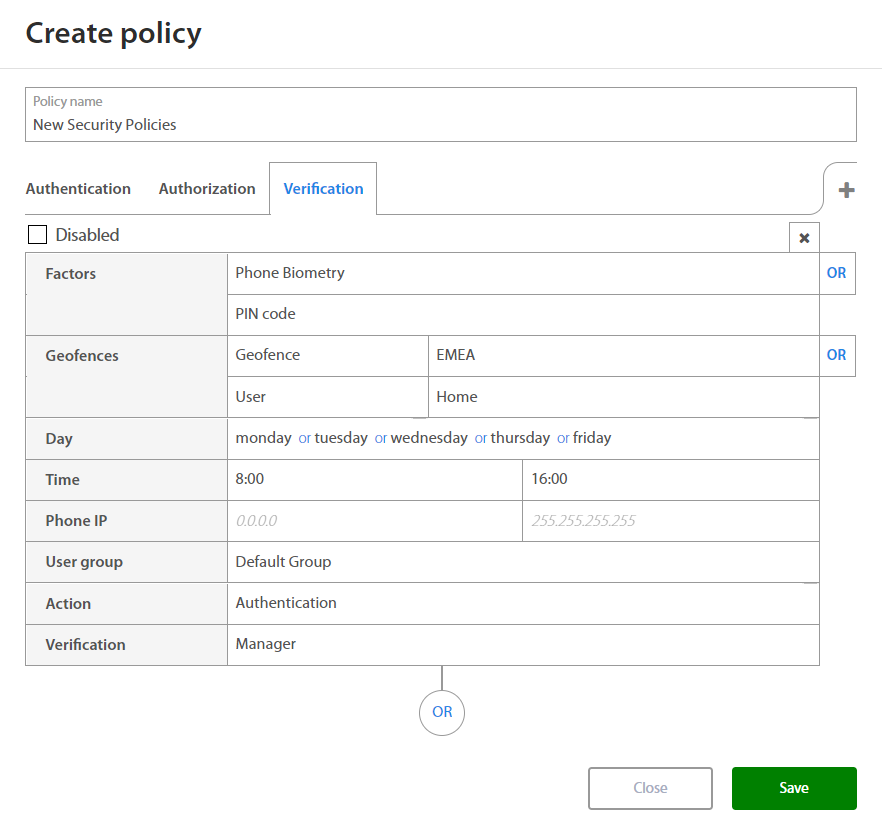
Verification¶
When setting rules for new Verification policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone IP | Set IP Range |
| User group | Select User group for wich verification will be applied |
| Verification |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
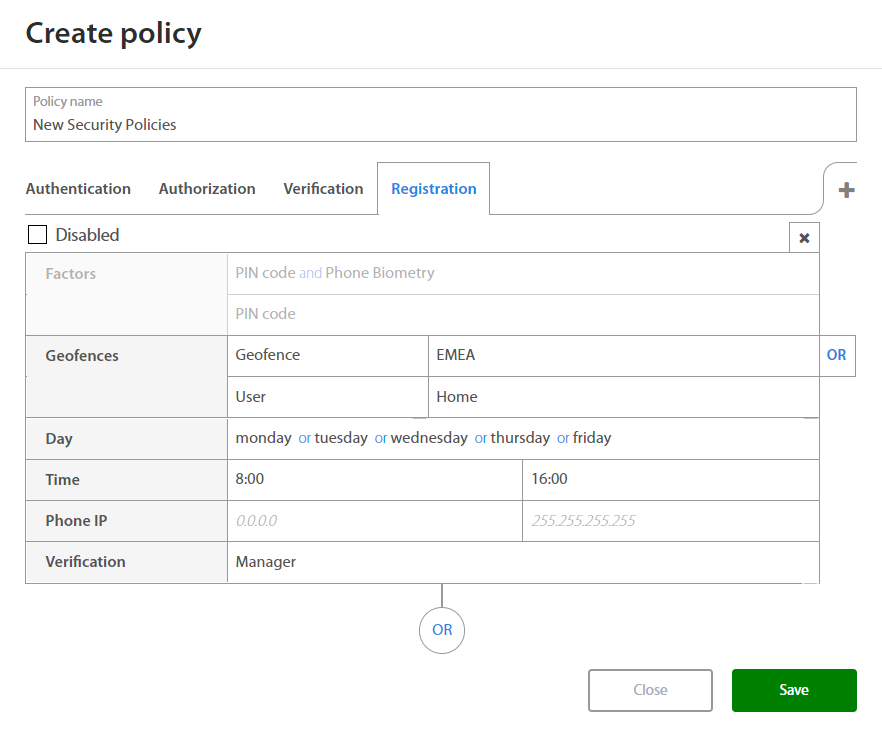
Registration¶
Factors on Registration policy are predefined and is not possible to change them. When setting rules for new Registration policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone IP | Set IP Range |
| Verification |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
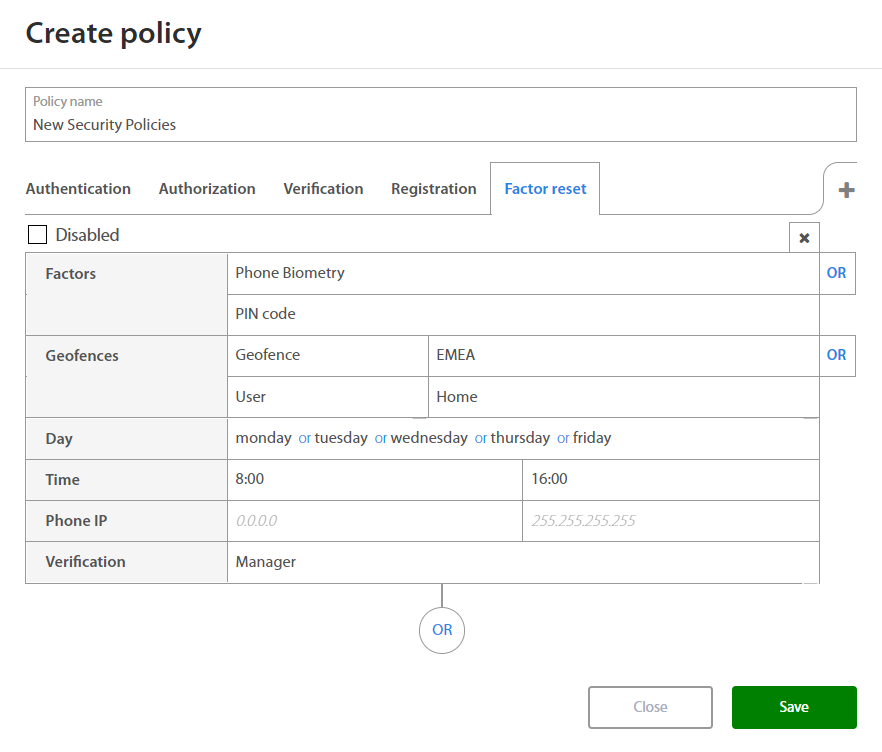
Factor Reset¶
When setting rules for new Factor Reset policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone IP | Set IP Range |
| Verification |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
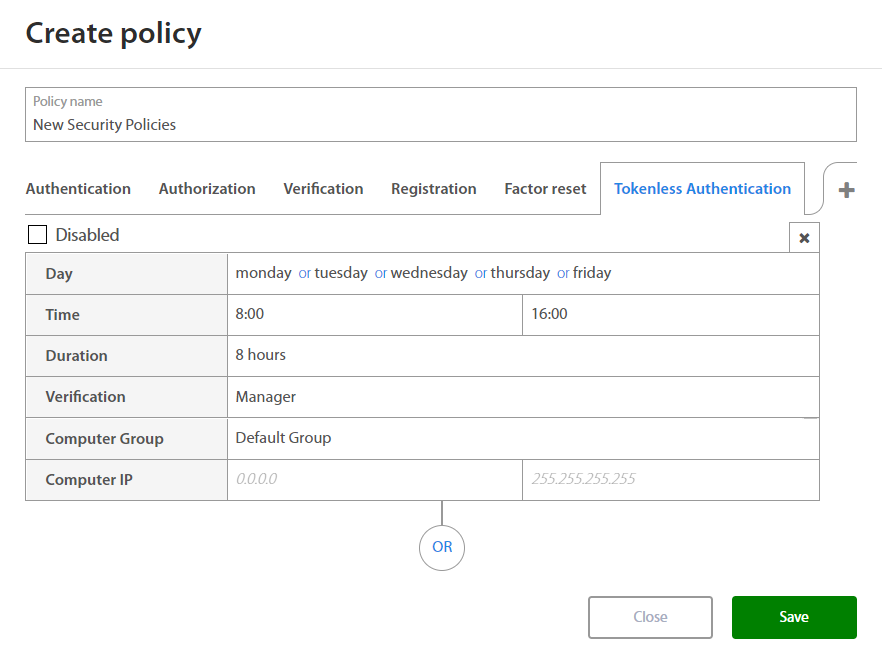
Tokenless Authentication¶
When setting rules for new Tokenless Authentication policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Duration | |
| Verification | |
| Computer group | Select Computer group for wich action will be applied |
| Computer IP | Set IP Range |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
Info
Duration
Based on the user's policy, verifiers have the option to select a time interval on theirs tokens during which the user can login without further verification on a particular computer. For further tokenless login on this computer, User must type username, PIN and give the reason.
For instance:
Let’s say that User’s tokenless duration is set up to 8 hours. If user clicks on Tokenless button and types username, PIN and reason, verification QR code on CPUI screen will be shown. Verifier scans this QR and provides authentication factors and select duration to one hour on token. Now, User can make further Tokenless logins without verification on this computer. In this time interval, user will type username, PIN and the reason only.
In case that login is verified by peers, the duration is set by peer who sets duration as the second in order.
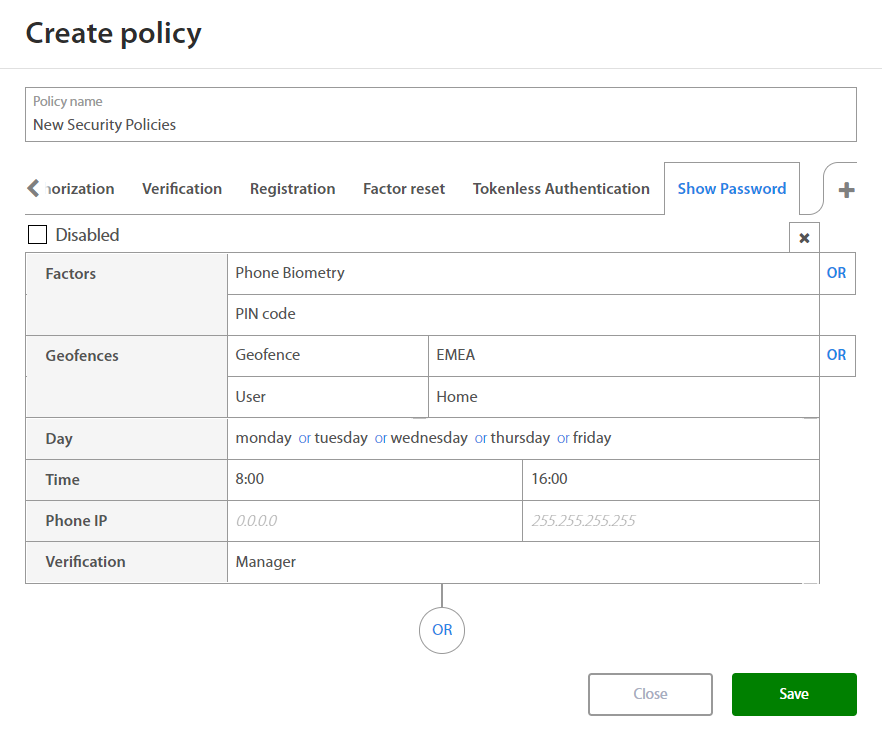
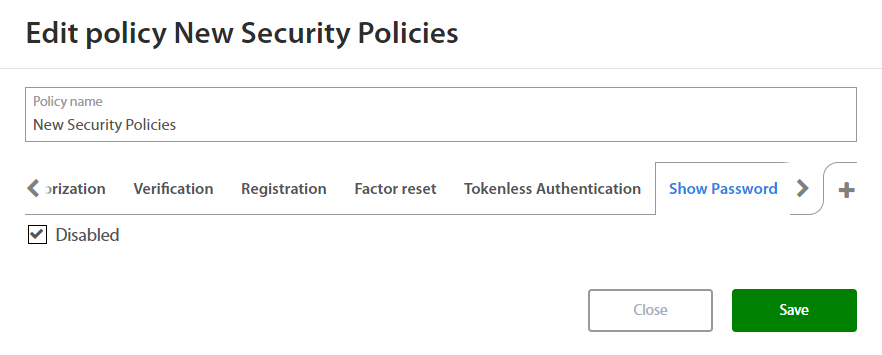
Show Password¶
When setting rules for new Show Password policy Administrator may set:
| Factor | Option / Description |
|---|---|
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone IP | Set IP Range |
| Verification |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
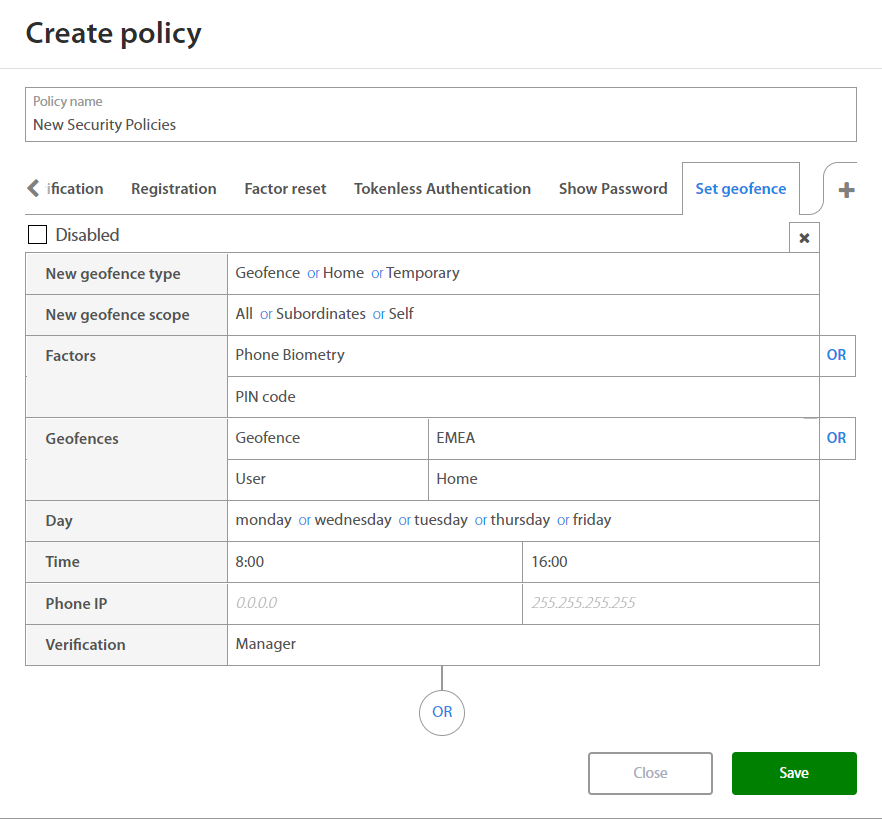
Set geofence¶
Set geofence’s policy provides options to set rules to set new geofence or location. Each user who uses Excalibur has an option to set its own home or temporary location by token or dashboard. Administrator can create geofences and GeofencesGroup.
When setting rules for new Set geofence policy Administrator may set:
| Factor | Option / Description |
|---|---|
| New geofence type - Type of geofence which user can create | |
| New geofence scope - Defines range of users for who can user create a geofence. | |
| Factors | |
| Geofence - Location where user have to be located. | |
| Day | Monday, Tuesday, Wednesday, Thursday, Friday, Saturday, Sunday |
| Time | Select time interval |
| Phone IP | Set IP Range |
| Verification |
By clicking on the OR button below the set of rules and Administrator may add a new set of rules if needed. By clicking on the x button, administrator may delete the existing set of rules.
Once done with creating a new Security policy click on the Save button, a policy will appear in a list of existing policies. By clicking on policy detailed information will show up together with a list of all Users Groups using that policy.
How to create copy of policy¶
The simplest way how to create policies with the same settings is to create a copy of the policy. Excalibur dashboard provides the option to create a copy of policy, if it is needed. If you want to make a copy of the policy, hover with mouse cursor over selected policy and click on  button. Set the new name of policy and save it.
button. Set the new name of policy and save it.
How to edit Security policy¶
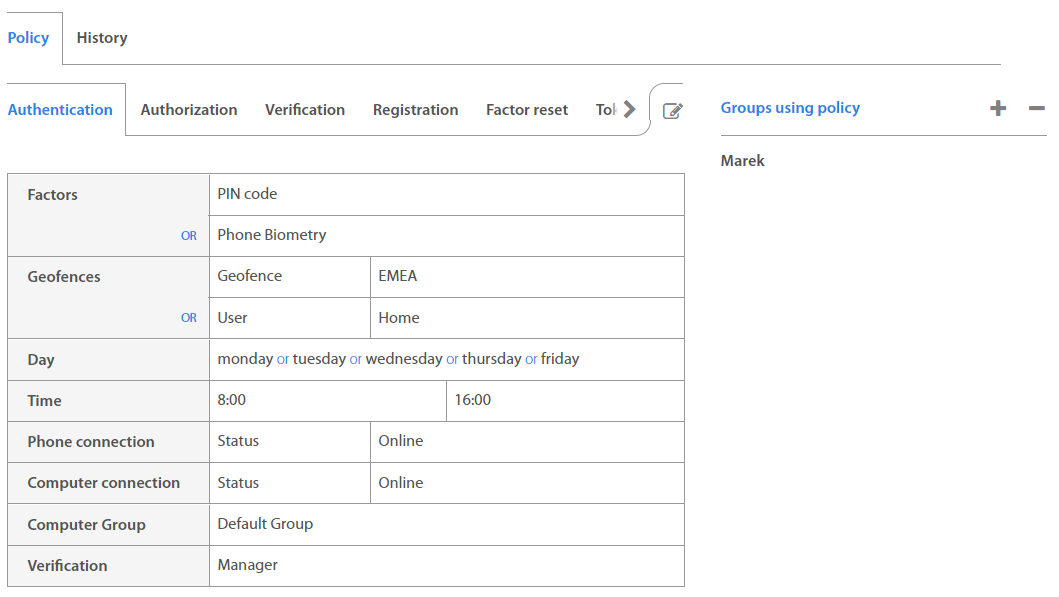
Administrator can edit existing policy or add a new set of rules if needed. By clicking on desired policy, the window with detailed information will appear. There is the edit button located in the top right corner of the window.
How to add a new set of rules¶
Let's say that the Administrator wants to add a new set of rules for Authentication Action.
Choose the desired tab from the list of available Actions, click on the OR button and set new rules for Security policy. Once done confirm new rules by saving the policy.
How to delete set of rules¶
On the other hand, Administrator may also delete existing sets of rules by clicking on the x button in the top right corner.
How to disable set of rules¶
Excalibur has an option to disable any action when it is needed. For instance: When a company wants to forbid access for action Show password. Select desired action tab in selected policy to disable action. Check Disable field and save changes
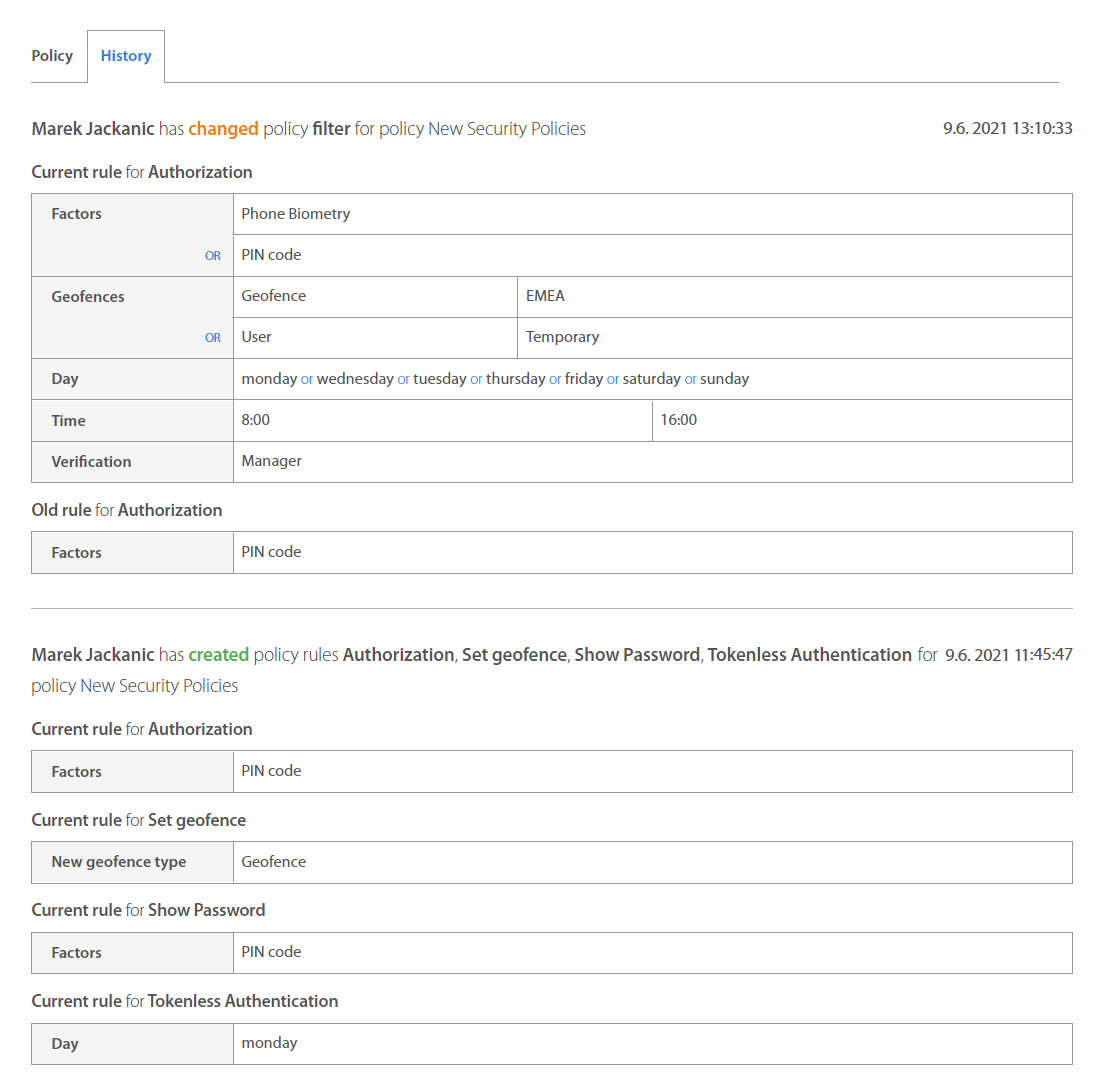
Security policy history¶
Administrator may also review all changes of policy from the history tab. Administrators can see there, person who made the change, timestamp and changed rule.
How to add a Group of Users to Security policy¶
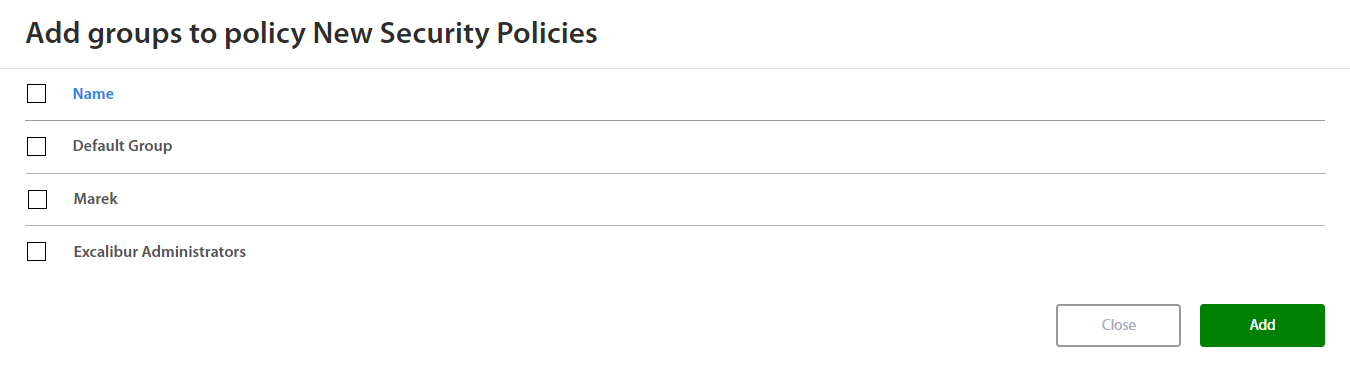
After setting a Security policy, Administrator may assign the policy to a group of Excalibur Users. Select the policy and click on + button in the top right corner.
Administrator may also see a list of already assigned groups and if needed, administrator can also remove a group from the list by clicking on - button.
Administrator may assign a group of users and also to select multiple groups at the same time. To confirm selection, click on the Add button.
Groups are managed in the “Groups section”, for more information please read Excalibur Administrator Dashboard Manual.